If you’re considering entering the in-demand cloud security field, you might find ISC2’s Certified Cloud Security Professional (CCSP) certification attractive yet challenging.
The CCSP certification exam comprises six domains focusing on critical aspects of cloud security. What does each CCSP domain mean, and what knowledge must you master to earn this industry-recognized certification?
Fear not: we’ve got you covered. We’ll deconstruct the six CCSP domains to help you plan your studies and next steps, such as obtaining the five required years of work experience.
We’ll explain key ideas, terms, and acronyms you must remember when taking the exam and show you examples of CCSP exam questions in every domain.
When you’re ready, let’s begin.
About the CCSP Certification
CCSP is an advanced cloud security certification for IT and information security leaders seeking to prove their understanding of cyber security and securing critical assets in the cloud.
The more people hold cloud security certifications like CCSP, the more cloud security positions we can fill worldwide.
According to ISC2's CCSP webpage, passing the exam proves that you have “the advanced knowledge and technical skills to design, manage, and secure data, applications, and infrastructure in the cloud using best practices, policies, and procedures established by [ISC2-certified] members and cybersecurity experts around the globe.”
CCSP Exam Details
The weights of CCSP domains are as follows:
| 1. Cloud Concepts, Architecture and Design | 17% |
| 2. Cloud Data Security | 20% |
| 3. Cloud Platform & Infrastructure Security | 17% |
| 4. Cloud Application Security | 17% |
| 5. Cloud Security Operations | 16% |
| 6. Legal, Risk and Compliance | 13% |
The CCSP exam is three hours long and contains 125 items. The passing score is 700 out of 1,000 points.

The exam questions are multiple-choice, and you can’t skip them and return to them later.
Passing the CCSP exam not only confers the title of “Associate of ISC2” but also opens up new career opportunities.
To be fully CCSP-certified after passing the exam, you need at least five years of cumulative work experience in information technology, with three years in information security and one year in at least one of the exam’s six domains.
You then obtain the endorsement of an ISC2-certified professional in good standing who can attest to your experience.
CCSP allows you to substitute CISSP for the entire CCSP experience requirement.
CCSP Cost
The standard CCSP cost is $599 USD in the US and Asia Pacific, and rescheduling the exam costs $50 while canceling it costs $100.
1. Cloud Concepts, Architecture and Design
This domain is about how well you understand cloud computing concepts, describe cloud reference architecture, understand security concepts relevant to cloud computing, understand design principles of secure cloud computing, and evaluate cloud service providers. These concepts include definitions, roles, and responsibilities.
You should be familiar with terms such as:
- Cloud service customer
- Cloud service provider
- Cloud service partner
- Cloud service broker
- Regulator
To pass the exam, you must know key cloud computing characteristics such as on-demand self-service, broad network access, multi-tenancy, rapid elasticity and scalability, resource pooling, and measured service.
You should also familiarize yourself with building block technologies such as virtualization, storage, networking, and orchestration.
Cloud reference architecture—which refers to cloud computing activities and cloud service capabilities such as application capability types, platform capability types, and infrastructure capability types—will also be part of the exam.
Finally, you’ll also be tested on cloud service categories, including Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS),
Apart from cloud-shared considerations, this domain tests you on the impact of cloud-related technologies, including:
- Data Science
- Machine learning
- Artificial intelligence (AI)
- Blockchain
- Internet of Things (IoT)
- Containers
- Quantum computing
- Edge computing
- Confidential computing
- DevSecOps
You must also understand cryptography, key management, identity and access control, data and media sanitization, network security, virtualization security, common threats, and security hygiene.
Other things to consider should be secure cloud computing design principles, which include the cloud secure data lifecycle, cloud-based business continuity (BC) and disaster recovery (DR) plans, business impact analysis (BIA), functional security requirements, security considerations and responsibilities for different cloud categories, cloud design patterns, and DevOps security.
Information Security Courses Bundles
Want lifetime access to expert-led cyber security training? Explore our Information Security Course Bundles — one-time purchase packages covering top topics like Ethical Hacking, Cloud, Linux, DevSecOps, and CompTIA certifications.
When evaluating cloud service providers, you must learn about verification against criteria such as the ISO/IEC 27017 and PCI DSS and system/subsystem product certifications such as Common Criteria (CC) and Federal Information Processing Standard (FIPS) 140-2.
Here are some key terms to remember:
- Virtualization
- Zero trust network
- SLA: Service-level agreements
- BIA: Business impact analysis
- PCI DSS: Payment Card Industry Data Security Standard
Example questions from this domain: (answer key follows)
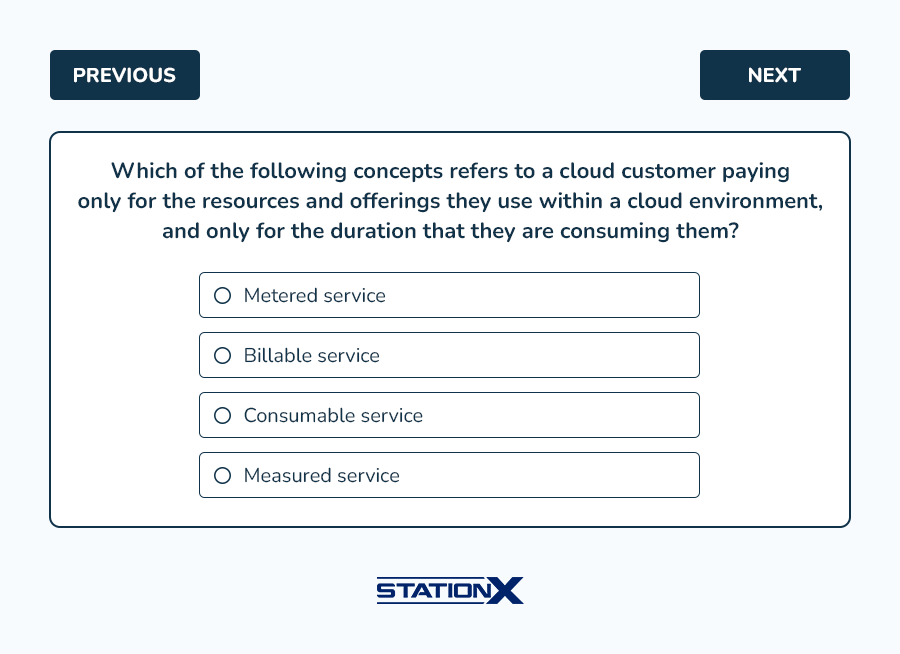
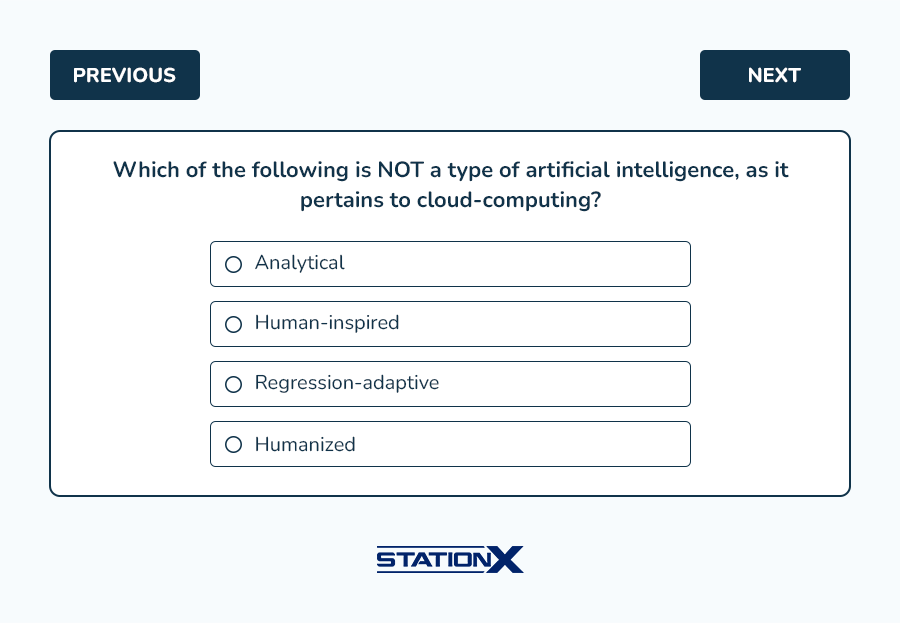
Answers:
- D is correct. Measured service is where cloud services are delivered and billed metered. The cloud customer only pays for those services they use and for the duration they use them. A, B, and C are incorrect.
- C is correct. Regression-adaptive does not pertain to cloud computing. The AI types utilized within a cloud computing environment are analytical, human-inspired, and humanized.
2. Cloud Data Security
This domain covers cloud data concepts, cloud data storage architectures, data security technologies and strategies, data discovery, data classification, Information Rights Management (IRM), data retention, deletion, and archiving policies, and following the trail of data events.
Cloud data life cycle phases, data dispersion, and data flows are cloud data concepts you’ll describe in the exam. Cloud storage types include long-term, ephemeral, and raw storage, and you must be aware of their relative potential threats.
Data security technologies and strategies include encryption, key management, hashing, data obfuscation, tokenization, data loss prevention (DLP), and more.
You’ll learn about implementing data discovery with concepts such as data location and structured, unstructured, and semi-structured data.
Data classification policies, mapping, and labeling fall under this domain.
Information Rights Management's (IRM) objectives include data rights, provisioning, and access models. The exam expects you to know the appropriate tools for issuing and revoking certificates.
You should know how to plan and implement data retention, deletion, and archiving policies, be familiar with their procedures, and understand the notion of legal hold.
This domain concludes with how to audit and trace data events and hold them accountable. You must know the definition of event sources and the requirements of event attributes such as identity, Internet Protocol (IP) address, and geolocation. Remember what logging, storage, and analysis of data events, chain of custody, and non-repudiation mean.
Here are some key terms to remember:
- Cloud data life cycle phases
- Data loss prevention
- Semi-structured data
- Legal hold
- Chain of custody
- Non-repudiation
Example questions from this domain: (answer key follows)
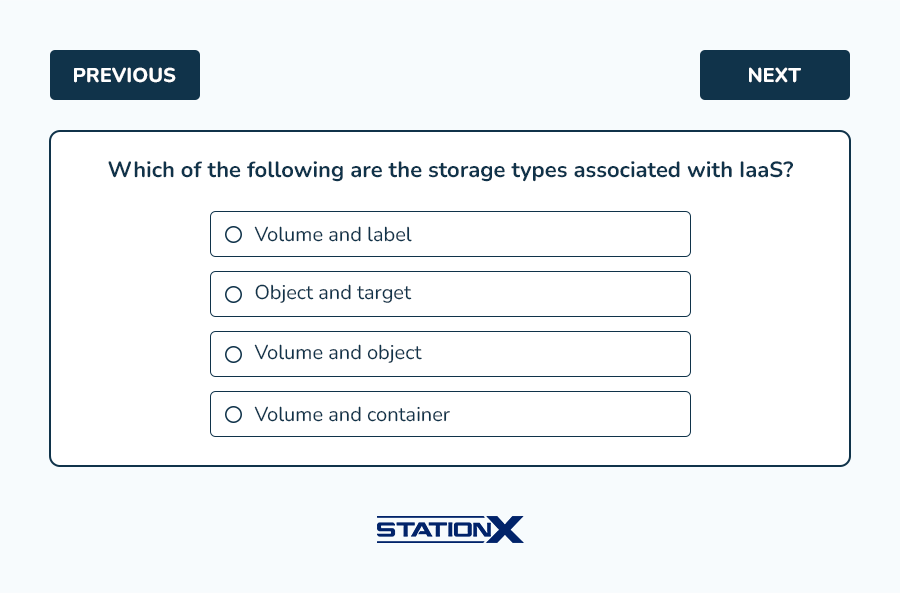
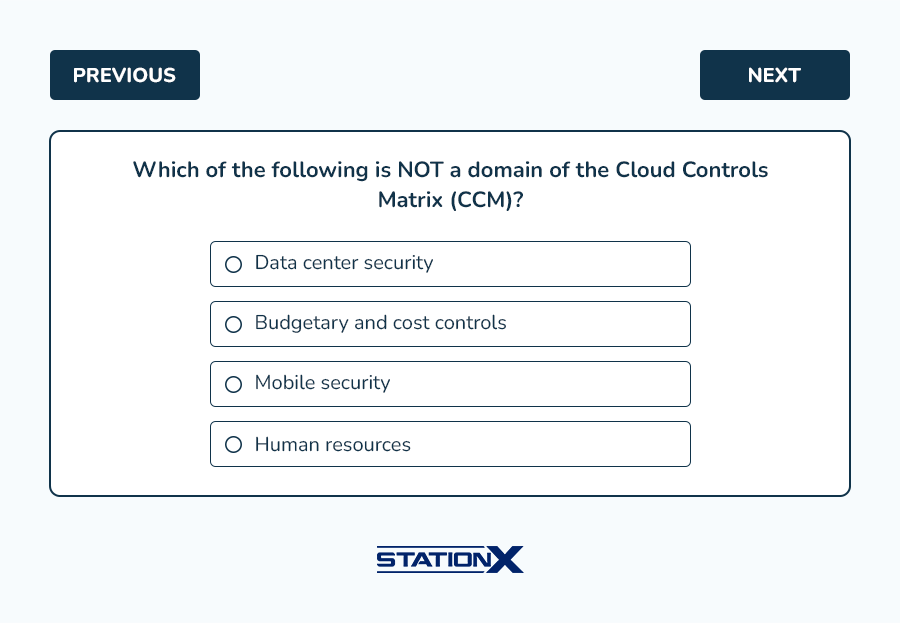
Answers:
- C is correct. Volume and object are the two storage types associated with IaaS. A, B, and D are incorrect.
- B is correct. Budgetary and cost controls aren’t among the domains outlined in the CCM. A, C, and D are incorrect.
3. Cloud Platform & Infrastructure Security
This domain’s primary foci are cloud infrastructure and platforms, security controls, business continuity, and disaster recovery.
You’ll need to know how the physical environment, network and communications, computing, virtualization, storage components, and management plane intersect.
In questions about designing a secure data center, you’ll need to consider logical design, such as tenant partitioning and access control; physical design, including location and buy or build; environmental design, such as Heating, Ventilation, and Air Conditioning (HVAC) and multi-vendor pathway connectivity; and making your design resilient.
This domain expects you to analyze risks associated with cloud infrastructure and platforms. You’ll conduct risk assessments, identify cloud vulnerabilities, threats, and attacks, and suggest risk mitigation strategies.
Mastering security controls—such as on-premises and other physical and environmental protection, system, storage, communication protection, identification, authentication, and authorization in cloud environments, and audit mechanisms, including log collection, correlation, and packet capture—would help.
This domain concludes with emphasizing business continuity (BC) and disaster recovery (DR) planning.
You’ll familiarize yourself with business requirements such as Recovery Time Objective (RTO), Recovery Point Objective (RPO), and recovery service level, and the exam will test your ability to create, implement, and test such plans.
Here are some key terms to remember:
- Management plane
- HVAC: Heating, Ventilation, and Air Conditioning
- BC: Business continuity
- DR: Disaster recovery
- RTO: Recovery Time Objective
- RPO: Recovery Point Objective
Example questions from this domain: (answer key follows)
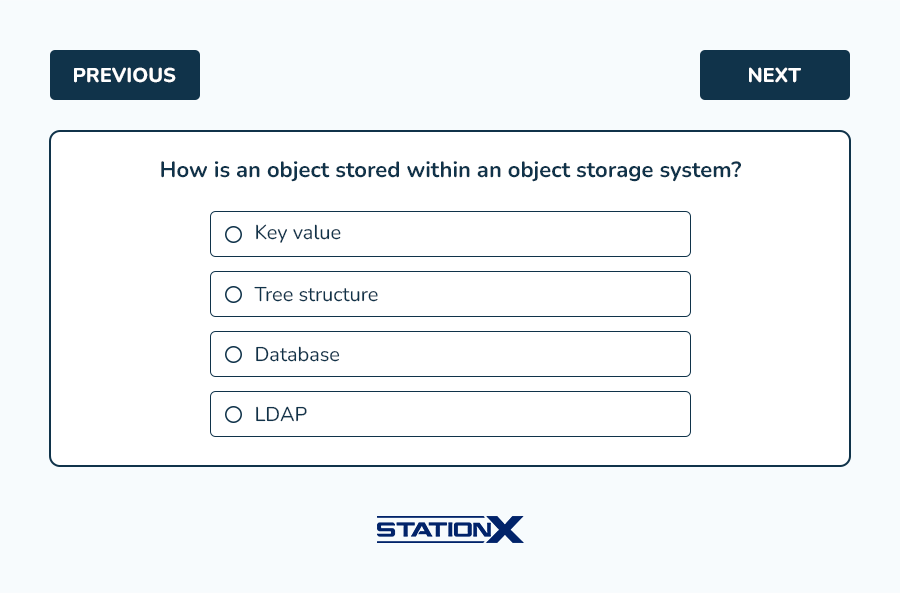

Answers:
- A is correct. Object storage uses a flat structure with key values to store and access objects. B, C, and D are incorrect.
- B is correct. Auto-scaling would not be covered. Reservations are designed to ensure systems can be powered on, operate, and perform their normal operations at all times. They aren’t designed or intended to ensure that applications can expand or provision new resources at any given time if other systems in the environment are using a larger share of the pooled resources.
4. Cloud Application Security
The previous domain was about cloud hardware security. This domain, instead, concerns software security in the cloud.
It covers the basics of cloud development, common pitfalls, and common cloud vulnerabilities such as OWASP Top-10 and SANS Top-25. The Secure Software Development Life Cycle (SDLC) process is a major exam item with business requirements, phases, and methodologies. You’ll also need to differentiate between waterfall and agile code development.
Moving on to cloud-specific risks, the intimidating section here is acronyms.
In threat modeling, we have lengthy expanded versions of acronyms like STRIDE, DREAD, ATASM, and PASTA. Secure coding includes acronyms such as OWASP’s Application Security Verification Standard (ASVS) and Software Assurance Forum for Excellence in Code (SAFECode).
You’ll apply cloud software assurance and validation strategies, such as functional and non-functional testing and security testing methodologies, including:
- Blackbox
- Whitebox
- Static
- Dynamic
- Software Composition Analysis (SCA)
- interactive Application Security Testing (IAST)
You’ll also check for quality assurance (QA) and conduct abuse case testing.
Here, learning how to use verified secure software is crucial. Securing application programming interfaces (API), supply-chain management such as vendor assessment, third-party software management including licensing, and validated open-source software are part and parcel of this aspect.
FREE Cyber Security Career Guide
Thinking of a career in cyber security? Our Cyber Security Career Guide walks you through the industry landscape, skill-paths, certifications, and realistic timelines to become job-ready.
To pass the exam and work in this field, we must thoroughly comprehend the cloud application architecture to ensure secure cloud applications function properly. Examples of supplemental security components include web application firewalls (WAF), Database Activity Monitoring (DAM), Extensible Markup Language (XML) firewalls, and API gateway.
You should be familiar with application virtualization and orchestration methods such as microservices and containers, cryptography, and sandboxing.
This domain concludes with questions on designing appropriate identity and access management (IAM) solutions. Some concepts you must know about are:
- Federated identity,
- Identity providers (IdP)
- Single sign-on (SSO)
- Multi-factor authentication (MFA)
- Cloud access security broker (CASB)
- Secrets management
Here are some key terms to remember:
- SDLC: Secure Software Development Life Cycle
- OWASP: Open Web Application Security Project
- STRIDE: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege
- QA: Quality assurance
- DAM: Database Activity Monitoring
- CASB: Cloud access security broker
Example questions from this domain: (answer key follows)

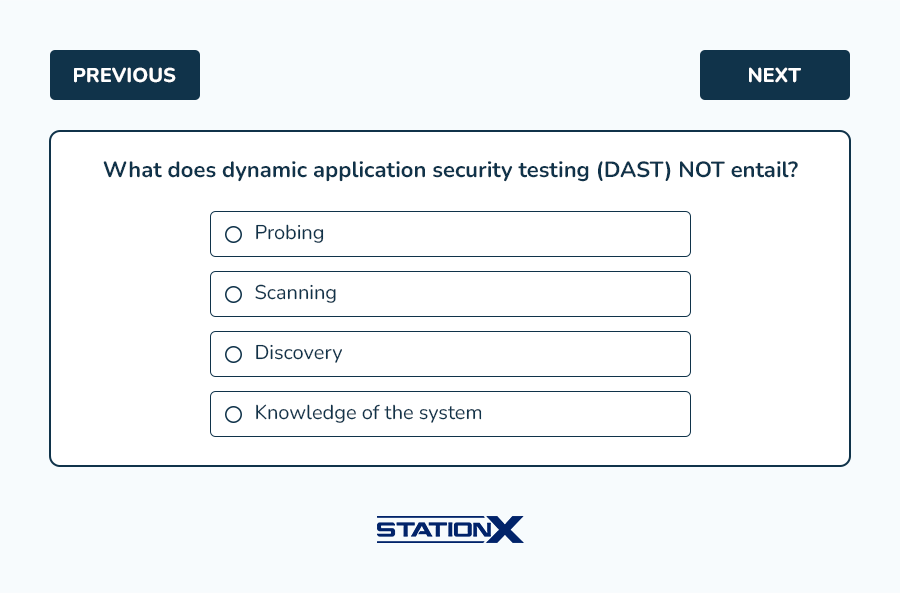
Answers:
- A is correct. Missing function-level access control does not validate. It is imperative for an application to perform checks when each function or portion of the application is accessed, to ensure that the user is properly authorized to access it. Without continual checks each time a function is accessed, an attacker could forge requests to access portions of the application where authorization has not been granted.
- D is correct. Dynamic application security testing (DAST) is considered “black box” testing and begins with no inside knowledge of the application or its configurations. Everything about the application must be discovered during the testing. A, B, and C are incorrect.
5. Cloud Security Operations
This domain concerns the day-to-day execution of security procedures for cloud environments, digital forensics, and security operations.
Know the hardware-specific security configuration requirements of the hardware security module (HSM) and Trusted Platform Module (TPM) and the virtual hardware-specific security configuration requirements on the network, storage, memory, central processing unit (CPU), and Hypervisor types 1 and 2.
Get familiar with installing and configuring management tools and guest operating system (OS) virtualization toolsets.
Learn how to operate and maintain a cloud environment’s physical and logical infrastructure. It has many complex moving parts, beginning with access controls for local and remote access, such as:
- Remote desktop protocol (RDP)
- Secure terminal access
- Secure shell (SSH)
- Console-based access mechanisms
- Jumpboxes
- virtual clients
Implementing operational controls and standards, such as ITIL and ISO/IEC 20000-1, is necessary for this domain. Terms like change management and information security management aren’t going away.
The digital forensics questions test your knowledge of forensic data collection methodologies, evidence management, and how to collect, acquire, and preserve digital evidence.
Questions assess your ability to manage communication with relevant parties, including but not limited to vendors, customers, partners, regulators, and other stakeholders.
CCSP holders are eligible for roles at security operations centers (SOC), so they must understand the intelligent monitoring of security controls such as:
- Firewalls
- Intrusion detection systems (IDS)
- Intrusion prevention systems (IPS)
- Honeypots
- Network security groups
- Artificial intelligence (AI) applications
They’ll also need to know about log capture and analysis methods such as security information and event management (SIEM), incident management, and vulnerability assessments.
Here are some key terms to remember:
- TPM: Trusted Platform Module
- ITIL: Information Technology Infrastructure Library
- ISO: International Organization for Standardization
- IEC: International Electrotechnical Commission
- IaC: Infrastructure as Code
- SIEM: Security information and event management
Example questions from this domain: (answer key follows)
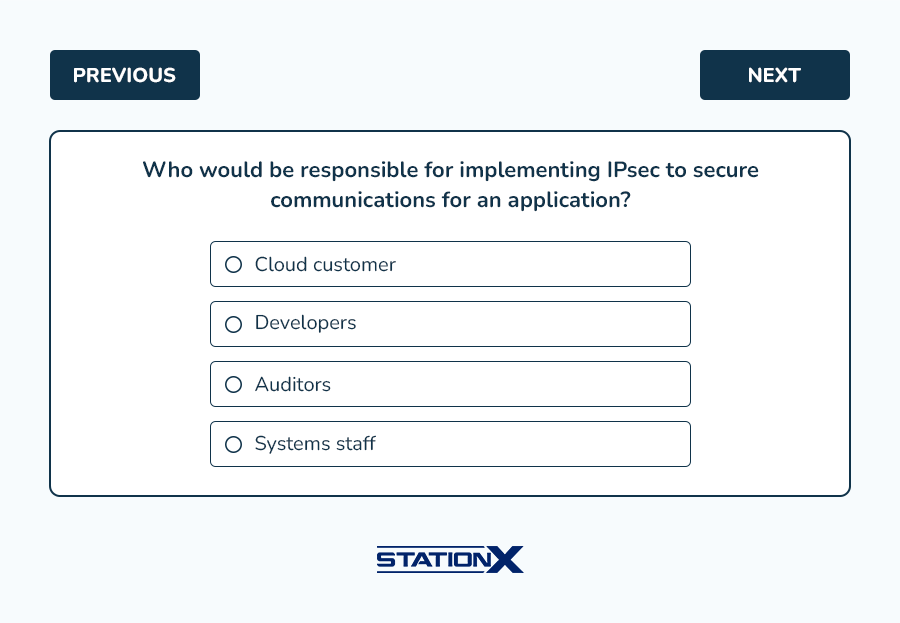
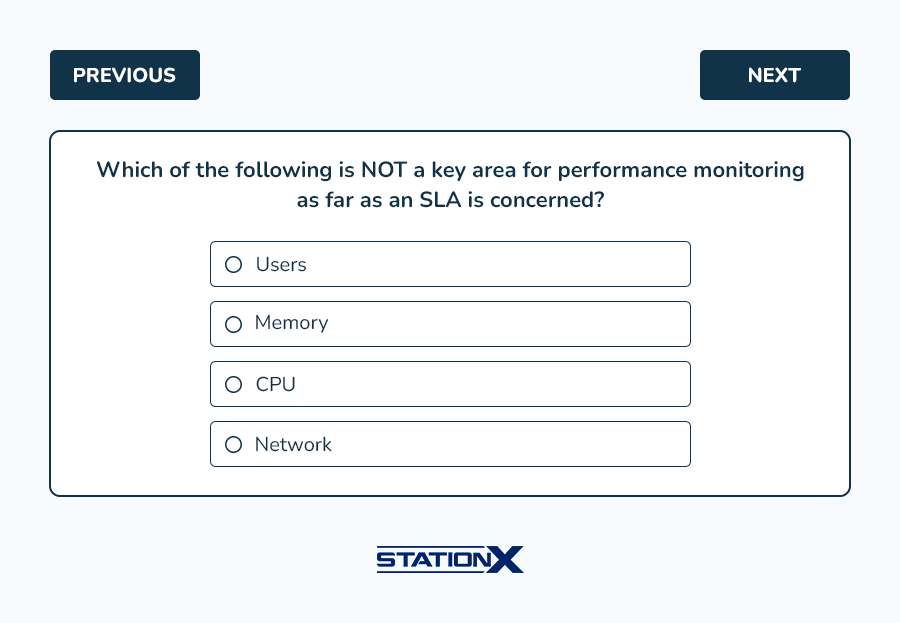
Answers:
- D is correct. Because IPsec is implemented at the system or network level, it is the responsibility of the systems staff. IPsec removes the responsibility from developers, whereas developers would implement other technologies such as TLS. A, B, and C are incorrect.
- A is correct. An SLA requires performance monitoring of CPU, memory, storage, and networking. The number of users active on a system would not be part of an SLA specifically, other than in regard to the impact on the other four variables. B, C, and D are incorrect.
6. Legal, Risk and Compliance
Like other cyber security disciplines, cloud security has its set of regulatory challenges and risk management best practices.
This domain covers legislation, privacy, audit processes, methodologies, required adaptations for a cloud environment, and the implications of cloud computing for enterprise risk management, outsourcing, and cloud contract design.
Acronyms also abound in this domain; be careful as you navigate this territory.
In questions asking you to articulate legal requirements and unique risks within the cloud environment, think about conflicting international legislation, evaluate legal risks specific to cloud computing, and apply what you know about eDiscovery, legal frameworks and guidelines, and forensics requirements.
It’s necessary to tell apart contractual and regulated private data because of country-specific legislation, jurisdictional differences in data privacy, and standard privacy requirements. The legal framework that stands out here is the General Data Protection Regulation (GDPR).
Questions on auditing and compliance will test your knowledge of internal and external audit controls, the impact of audit requirements, identifying assurance challenges of virtualization and cloud uses, and the types of audit reports, to name a few.
Risk management programs specific to a cloud environment, contractual considerations such as service-level agreement (SLA), and supply-chain management round up this domain.
Here are some key terms to remember:
- CSA: Cloud Security Alliance
- PII: Personally identifiable information
- PHI: Protected health information
- GDPR: General Data Protection Regulation
- ISAE: International Standard on Assurance Engagements
- SOX: Sarbanes-Oxley
Example questions from this domain: (answer key follows)

Conclusion: CCSP Domains
We hope that this overview of CCSP domains can help you plan your studies for this highly respected advanced cloud security certification.
CCSP can be a daunting exam, but once you’ve passed it, you can dive into the in-demand field of cloud security and solve the most pressing problems there, earning valuable work experience and furthering your career.
To learn more about CCSP, check out our CCSP articles and course offerings below.
Join our Master's Program today to access CCSP and cloud security courses supported by a like-minded community, including fellow cloud security professionals who will keep you on track in your studies.
The Cloud Computing Courses Bundle: Digital Cloud Training covers AWS, Azure, cloud security, and architecture across 7 industry-recognized certification courses with 85+ hours of hands-on training, labs, and exam preparation for top credentials.
This Cloud Computing Courses Bundle: Digital Cloud Training includes:
- CompTIA Cloud+ Certification Course: CV0-003
- AWS Cloud Practitioner Study Guide - Essential Course
- Best AWS Solutions Architect Course (SAA-C03)
- Microsoft Azure Fundamentals AZ-900 Course
- AZ-104 Training: Azure Administrator Associate
- Microsoft Cybersecurity Architect - SC-100 Exam Preparation
- CCSP Certification Training Course




