If you're preparing to start a career in cyber security, the CompTIA Security+ (SY0-701) exam covers a broad range of essential topics, making it crucial to understand its knowledge domains.
Mastering these domains will help you structure your study plan and ensure you're ready for the exam. But what does each of these Security+ domains mean, and what cyber security concepts do they include?
Look no further: we’ve got you covered. We’ll demystify the exam objectives to help you plan your studies. For each domain, we’ll explain key ideas, terms, and acronyms you must remember. Moreover, we’ll show you examples of questions that assess your knowledge of every exam domain.
When you’re ready, let’s dive in.
About the CompTIA Security+ Exam
CompTIA Security+ is a globally recognized entry-level cyber security certification focusing primarily on up-to-date best practices for risk management and risk mitigation. It emphasizes the practical aspects of identifying and addressing security threats, attacks, and vulnerabilities.
According to CompTIA, the target audience for the Security+ certification is IT professionals with at least two years of experience as security administrators or systems administrators.
They should have experience in IT administration with a focus on security, hands-on experience with technical information security, and a broad knowledge of security concepts.
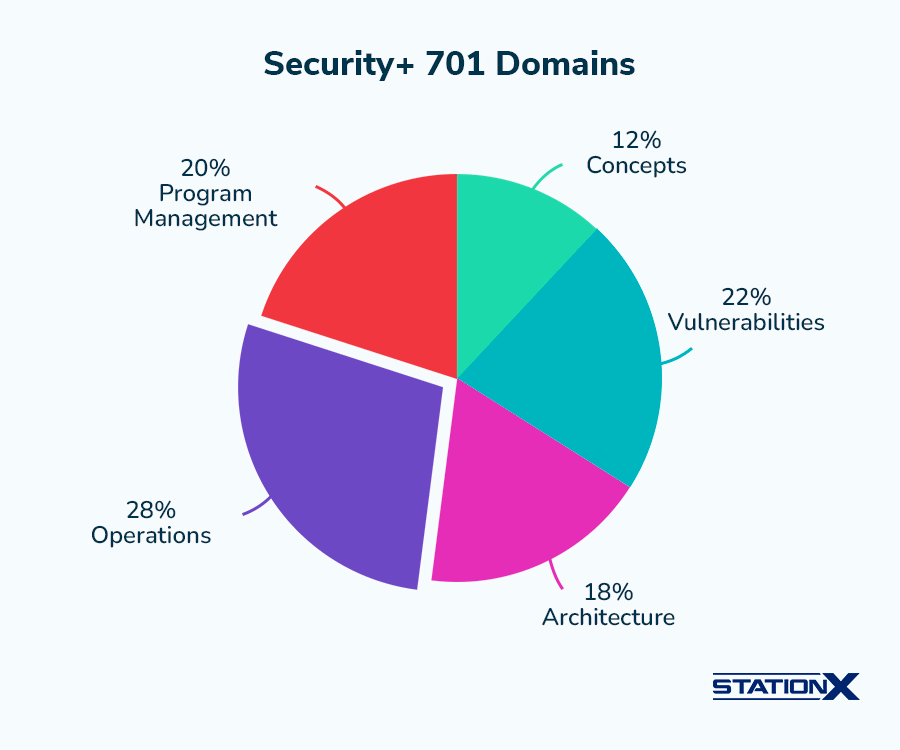
The latest CompTIA Security+ exam code is SY0-701, and the exam domains are:
- General Security Concepts (12%)
- Threats, Vulnerabilities, and Mitigations (22%)
- Security Architecture (18%)
- Security Operations (28%)
- Security Program Management and Oversight (20%)
The Security+ exam is essential for aspiring cybersecurity professionals, IT administrators, and related roles because it validates the skills needed for baseline security readiness and incident response. It equips candidates to handle current threats and take a proactive approach to preventing future attacks.
Topics in these core knowledge domains include the latest trends in threats, attacks, vulnerabilities, automation, zero trust, risk, IoT, and operational technology (OT).
There’s also a strong focus on the latest techniques for cyber security professionals working in hybrid cloud and on-premises environments. So, pay attention to cloud environments, communication, reporting, and teamwork.
Information Security Courses Bundles
Want lifetime access to expert-led cyber security training? Explore our Information Security Course Bundles — one-time purchase packages covering top topics like Ethical Hacking, Cloud, Linux, DevSecOps, and CompTIA certifications.
The CompTIA Security+ exam includes two types of questions:
- Multiple-choice questions, which may admit single or multiple answers;
- Performance-based questions (PBQs), which test your ability to solve problems in a simulated environment.
These make CompTIA Security+ an incredibly valuable certification, demonstrating the holder’s excellence in practical cyber security skills. Anywhere from two to six PBQs appear at the start of the Security+ exam.
It’s a 90-minute examination, during which you’ll answer up to 90 questions and complete a survey afterwards. The passing score is 750 on a scale of 100 to 900.
For more information, refer to our guide to Security+.
Without further ado, let’s move on to the first domain.
Domain 1: General Security Concepts (12%)
“Better safe than sorry.”
—English proverb
Cyber security is an umbrella industry of multiple and diverse roles, including technical and administrative. Different areas of cyber security represent how we can categorize many topics based on their connections and relationships.
This domain concerns key security principles: fundamental cyber security concepts, appropriate security controls, change management processes, security solutions, and cryptographic solutions. Such concepts form the basis for the dynamic field of cyber security knowledge.
Arguably, the most important security principle is the CIA Triad:
- Confidentiality means you need authorization to access certain data.
- Integrity focuses on maintaining the accuracy, consistency, and trustworthiness of data.
- Availability ensures that resources are accessible and usable when needed.
News, such as the infamous Crowdstrike outage, means that no organization is immune to cyber threats.
Therefore, major topics in this domain are risk management, an ongoing process of identifying, analyzing, evaluating, and addressing cyber threats, and change management, the navigation of the impacts of changes to an organization.
Cyber threats often originate from threat actors, which include individuals, groups, or organizations such as hackers, cybercriminals, and nation-state actors.
However, threats can also arise from system vulnerabilities, misconfigurations, and human error. Security controls help organizations avoid, prevent, detect, mitigate, respond to, and remediate risks posed by both intentional and unintentional cyber threats.
Cryptography is an important part of technical security controls in this domain. It protects data such as credit card transactions, emails, and websites from theft or tampering.
It’s based on the use of algorithms and mathematical functions to transform readable plaintext into unintelligible ciphertext, which is difficult to recover computationally.
Some key terms/acronyms to remember:
- AAA: Authentication, Authorization, and Accounting
- Blockchain: a tamper-resistant shared data structure often associated with cryptocurrency.
- Non-repudiation: the inability of a subject to deny having performed an action.
- PKI: Public key infrastructure
- Zero Trust: The zero trust model enforces strict verification for all users and devices inside and outside an organization’s network. It requires continuous authentication and access validation, reducing the risk of breaches caused by compromised credentials or insider threats.
Example questions from this domain: (answer key follows)

Expand for answer key
Answers:
- B. Full-disk encryption ensures that the entire hard drive, including the operating system and all data, is encrypted. This protects against unauthorized access, especially if the device is lost or stolen.
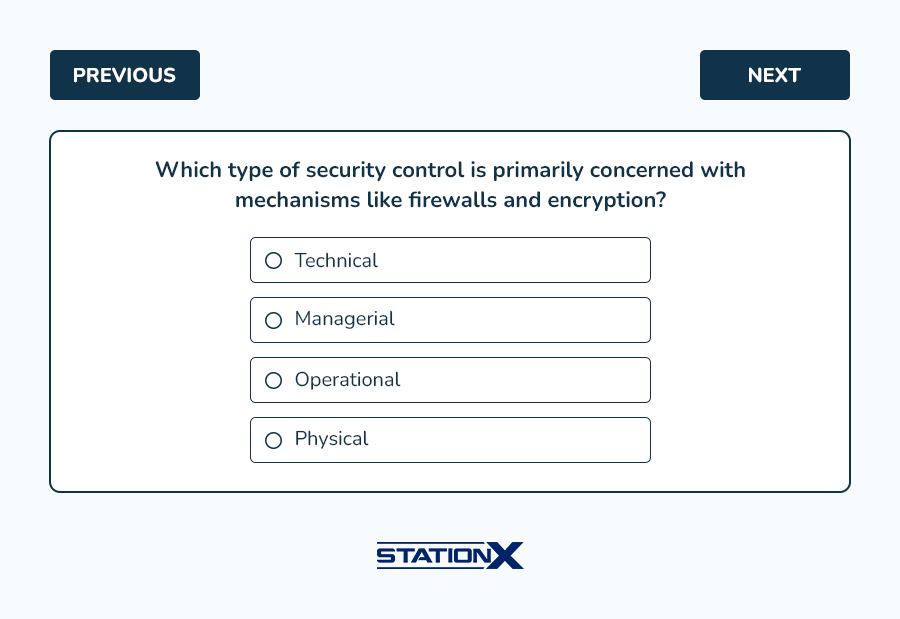
- A. Technical controls, often referred to as logical controls, are implemented using technology. They are designed to protect data's confidentiality, integrity, and availability as it is processed, transmitted, and stored. Examples include firewalls, which block unauthorized access to a network; encryption, which scrambles data so it can’t be understood without the correct key; and intrusion detection systems, which monitor networks for signs of malicious activity.
Domain 2: Threats, Vulnerabilities, and Mitigations (22%)
“Status quo—that’s Latin for the mess we’re in…”
—Ronald Reagan, in Chicago, Illinois, September 3, 1981
This domain focuses on identifying and mitigating security threats and vulnerabilities.
You must understand common threat actors and their motivations, threat vectors and attack surfaces, vulnerabilities, indicators of malicious activity, and cyber threat mitigation techniques.
In cyber security, assets are devices containing something to protect, such as data. You must become familiar with different types of threats:
- Malware refers to applications that steal data from or ruin assets, such as ransomware, Trojans, worms, spyware, bloatware, viruses, keyloggers, logic bombs, and rootkits.
- Social engineering exploits human weakness to gain unauthorized access and perform unauthorized functions on assets.
- Insider threats are accidental or deliberate organizational risks that can cause damage.
- Advanced persistent threats (APTs) are covert operations aimed at long-term intelligence-mining hacking.
Every system has exploitable weak points called vulnerabilities. Those with low cyber security awareness may not know about them until something happens. Here are some common vulnerabilities:
- Outdated software poses cyber security risks because threat actors may have found ways to exploit the old code. Hence, it’s important to patch your systems regularly.
- Misconfigurations may cause systems to crash—the Crowdstrike outage in July 2024 is a case in point.
- Weak authentication mechanisms, such as wireless security settings, permit unauthorized resource access.
But not all hope is lost. Mitigation strategies include:
- Patch management: Always keep systems up-to-date with a rollback in case of a crash.
- Access controls: Limiting permissions to data and systems reduces the likelihood of data breaches and insider threats.
- Security awareness training: A common implementation is having staff respond to simulated phishing emails.
Some key terms/acronyms to remember:
- ACL: Access Control List
- DDoS: Distributed denial-of-service attack
- SQLi: Structured Query Language injection
- Zero-day attack: A previously unknown vulnerability
Example questions from this domain: (answer key follows)
Expand for answer key
Answers:
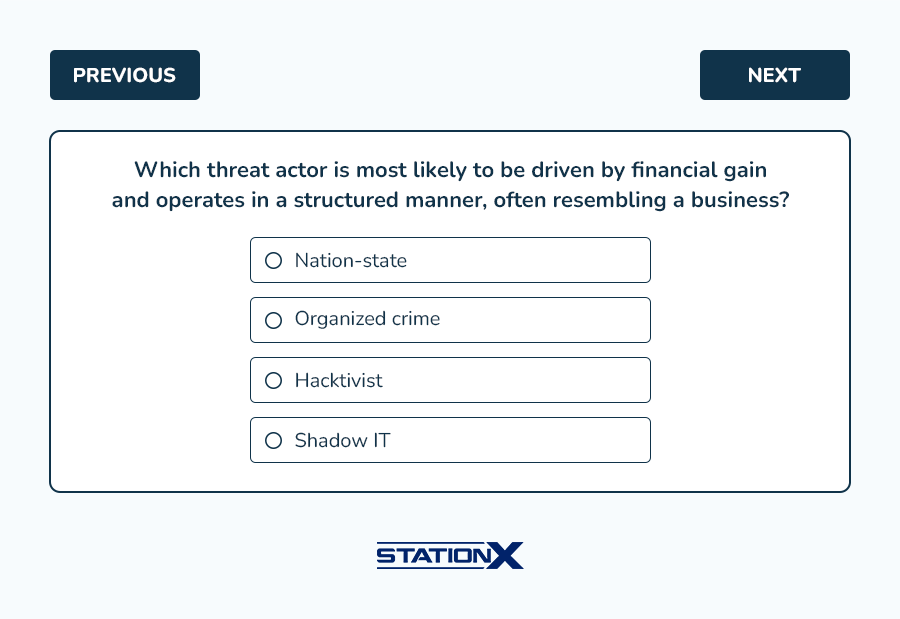
- B. Organized crime groups are primarily motivated by financial gain. They operate in a structured manner, often resembling businesses, and engage in illegal activities to generate profit. Their operations can range from fraud schemes to ransomware attacks, and they often have resources and capabilities that can pose significant threats.
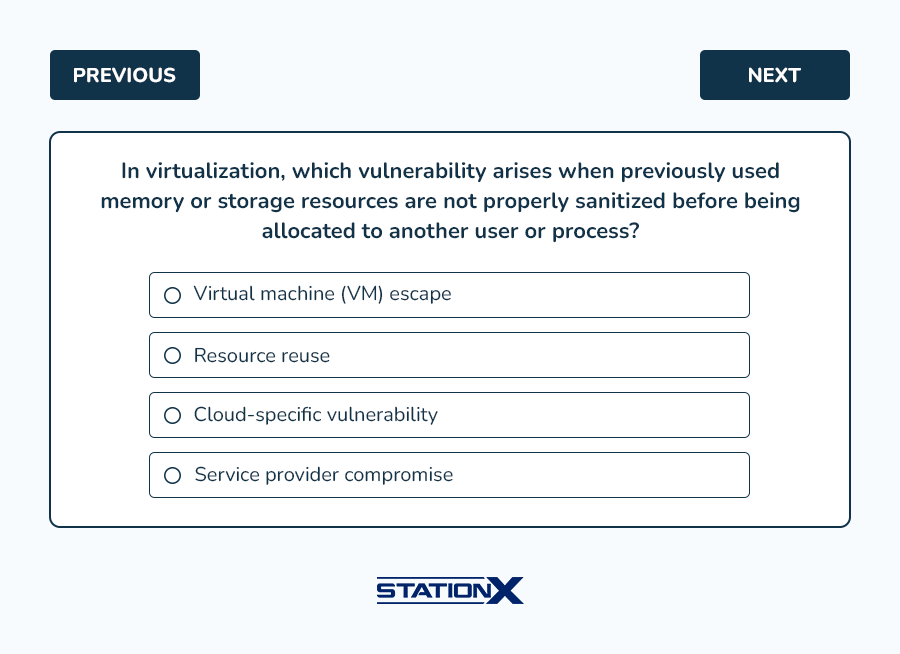
- B. Resource reuse vulnerabilities occur when previously used memory or storage resources in a virtualized environment are not properly sanitized or cleared before being allocated to another user or process. This can lead to data leakage or unauthorized data access.
Domain 3: Security Architecture (18%)
“He wins his battles by making no mistakes. [...] the skillful fighter puts himself into a position which makes defeat impossible and does not miss the moment for defeating the enemy.”
—Sun Tzu, The Art of War
This domain highlights the process of designing secure IT infrastructures, including the security implications of different architecture models, concepts, and strategies to protect data and the importance of resilience and recovery.
Questions will ask you about scenarios in which you apply security principles to secure enterprise infrastructure.
Security models offer a blueprint for organizational security. They often follow security frameworks such as NIST and ISO, which are well-documented standards, policies, procedures, and best practices to strengthen an organization’s security posture and reduce risk.
The most important principles of secure design are defense-in-depth and least privilege. Layering security measures delays threat actors’ intrusion and speeds up their eventual detection. Least privilege limits threat actors’ impact on assets.
Secure network architecture concepts, such as the following, comprise a major part of this domain:
- Segmentation refers to dividing a network into smaller sections or subnets using devices such as hubs, switches, bridges, or logical groupings such as virtual local area networks (VLANs).
- Firewalls are web traffic filters on incoming and outgoing network traffic based on predefined security rules.
- Demilitarized zones (DMZs) are physical or logical sub-networks that separate subnets from external untrusted networks. They typically contain external-facing resources such as DNS, email, proxy, and web servers.
Some key terms/acronyms to remember:
- Defense-in-depth: Using multiple layers of security measures
- ICS: Industrial control systems
- Least privilege: Only grant users/entities the minimum access or permissions needed to perform their job.
- SASE: Secure access service edge
- SCADA: Supervisory control and data acquisition
Example questions from this domain: (answer key follows)
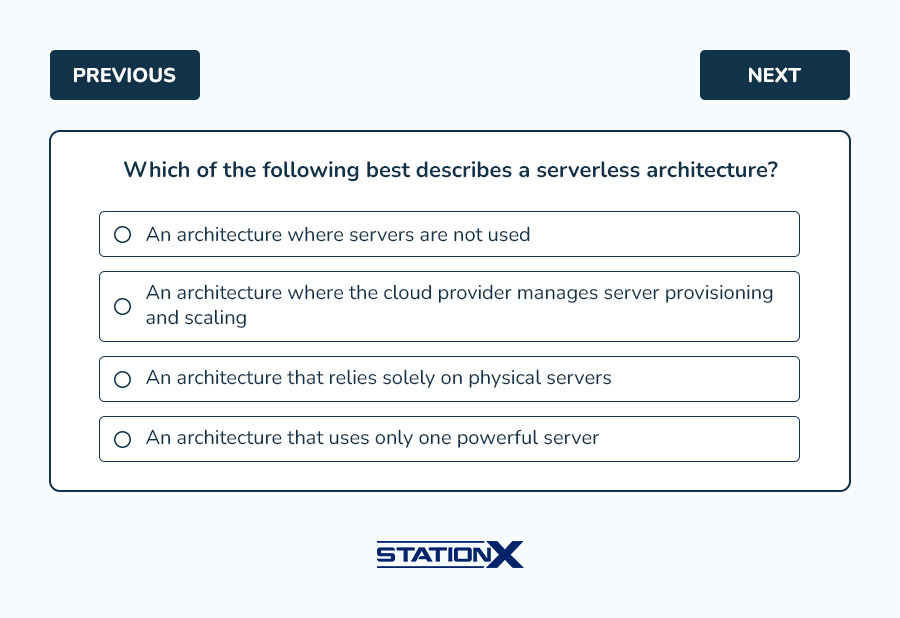

Expand for answer key
Answers:
- B. In a serverless architecture, developers write code that is executed in response to events. The cloud provider automatically manages the infrastructure, including server provisioning and scaling, allowing developers to focus on code.
- B. Multi-cloud systems involve leveraging multiple cloud service providers to distribute cloud computing resources and reduce dependence on a single provider.
Domain 4: Security Operations (28%)
“Keep your head on a swivel.”
— Idiom in English, likely with military or sporting roots
The highest-weighted domain in this exam focuses on daily security tasks and incident response.
You must understand the security implications of proper hardware, software, and data asset management, vulnerability management, security alerting and monitoring, automation and orchestration in secure operations, and incident response.
Scenario-based questions will test your knowledge of common security techniques for computing resources, ways to modify enterprise capabilities to enhance security, identity and access management, and the use of data sources to support an investigation. For example, questions on secure application development belong here.
Monitoring, logging, and continuous security assessment are important because organizations can thus respond promptly to emerging threats, ensuring the security of their systems and data.

Familiarize yourself with operational security practices such as:
- Vulnerability management: the ongoing, regular process of identifying, assessing, reporting on, managing, and remediating vulnerabilities across a network.
- Threat hunting: a proactive approach to identifying previously unknown or ongoing cyber threats.
- Security automation: the use of tools with minimal human intervention for preventing, detecting, identifying, and eliminating cyber threats.
Some key terms/acronyms to remember:
- CVE: Common Vulnerability Enumeration
- NAC: Network access control
- MDM: Mobile device management
- OSINT: Open-source intelligence
Example questions from this domain: (answer key follows)
Domain 5: Security Program Management and Oversight (20%)
“Learn to obey before you command.”
—Solon, ancient Greek statesman
Real-life cyber security professionals must comply with relevant laws, regulations, and industry standards because cyber threats have consequences. Governance, risk management, and compliance (GRC) characterize this domain.
You must know about effective security GRC, third-party risk assessment and management, audits, and assessments. Scenario-based questions will ask you how to implement security awareness practices.
Cyber security and risk management go hand in hand. We rely on security frameworks such as NIST or ISO 27001 to communicate security policies to other members of their respective teams at work and amongst other cyber security professionals in the industry.
From these policies, we derive procedures to deal with cyber threats.
Business continuity planning (BCP) is a system of prevention and recovery from potential threats to a company. The goal is to protect personnel and assets and quickly resume their functions in a disaster.
Disaster recovery planning (DRP) ensures businesses are prepared to face different cyber threats, including malware attacks, power outages, and natural disasters. A good DRP swiftly and effectively restores operations in an enterprise environment.
Standards like GDPR, HIPAA, and PCI-DSS impose standardized procedures on data ownership. Regulatory compliance with them respects the data privacy rights of individuals and groups involved, defiance of which may have severe legal and reputational consequences.
Some key terms/acronyms to remember:
- AUP: Acceptable Use Policy
- ALE: Annualized Loss Expectancy
- RPO: Recovery Point Objective
- SDLC: Software development lifecycle
- SLA: Service Level Agreement
Example questions from this domain: (answer key follows)
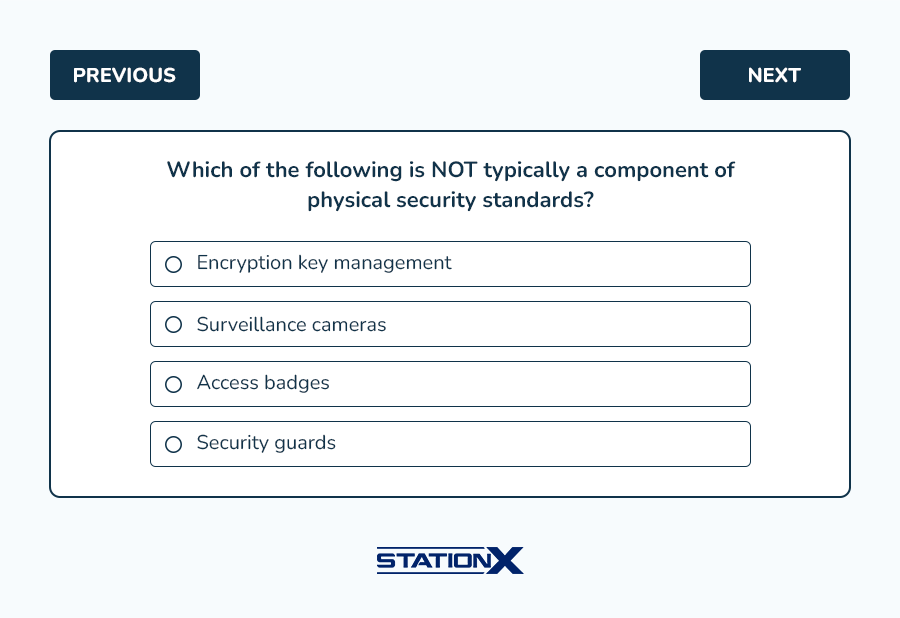
Expand for answer key
Answers:
- A. While surveillance cameras, access badges, and security guards are components of physical security standards, encryption key management pertains to encryption standards.
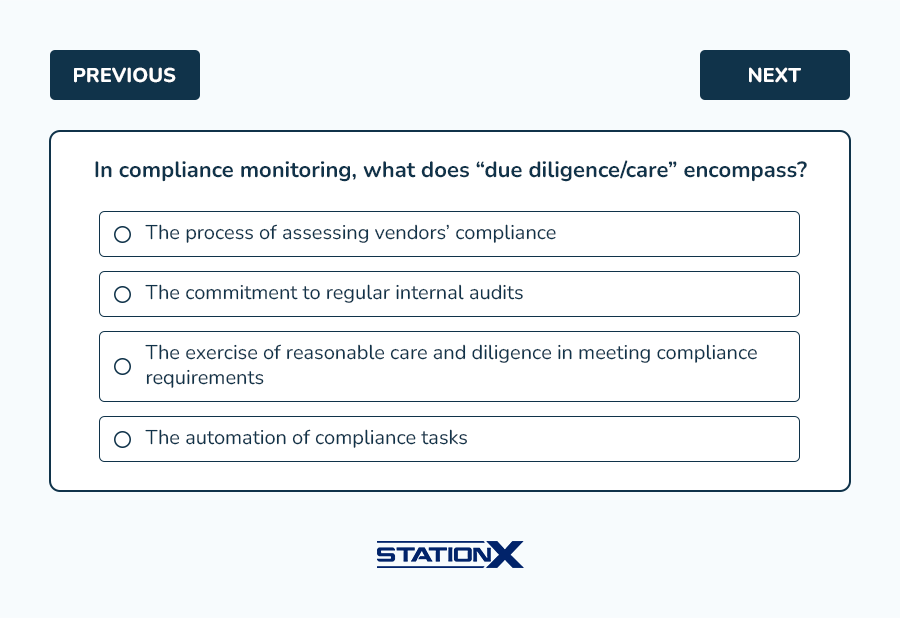
- C. “Due diligence/care” in compliance monitoring refers to the exercise of reasonable care and diligence in meeting compliance requirements, both internally and externally.
Conclusion
We hope this brief article on Security+ domains helps you plan your studies for this in-demand entry-level cyber security certification.
Security+ isn’t an easy exam, but with proper planning, practice, and perseverance, you can enter the field of cyber security and gain valuable work experience there for further career opportunities.
If you’re preparing for your Security+ certification, we have two great options to help your success. You can buy our CompTIA Security+ Course & SY0-701 Practice Test Bundle as a one-time purchase and get lifetime access to over 20 hours of on-demand video training, three full-length practice exams, and flashcards.
You can also join the StationX Master’s Program for access to over 30,000 courses and hands-on labs, covering all aspects of cyber security.
Lastly, you can save big by purchasing your Security+ exam voucher directly from StationX! We offer vouchers for all CompTIA certification exams, with discounts reaching 30% off CompTIA’s price.
The CompTIA Security+ Course & SY0-701 Practice Test Bundle includes:
- CompTIA Security+ Study Guide: SY0-701 Total Course
- CompTIA Security+ Training: Self-Paced Course
- CompTIA Security+ SY0-701 Exam Questions and Answers
- CompTIA Security+ Practice Test Series: Ace the SY0-701
- CompTIA Security+ Exam Objectives Flash Cards: SY0-701 Prep




