You’ve undoubtedly seen the SOC analyst position pop up when investigating common entry-level cyber security jobs, and perhaps you’re wondering: are SOC analysts in demand?
After all, lower-level positions are only worth fighting for if there are enough positions to go around.
Before investing time and money into becoming a SOC analyst, you should understand what a SOC analyst does, the role's professional outlook, how much it makes, and what certifications you’ll need to make your application stand out to employers.
Scoring a SOC analyst position is how many aspiring cyber security professionals break into the industry. To get there, you'll need a clear plan—and the best time to start planning is right now.
Are you ready? Let's start.
What Does a SOC Analyst Do?
Security Operations Center (SOC) analysts are on the first line of a company’s IT defense. They’re first to respond when a bad actor attempts to penetrate a company’s defenses. These analysts are in the trenches, getting their hands dirty as they work to protect digital assets.
Their most common responsibilities include:
- Identity and access management
- Monitoring security alerts and incidents in real-time
- Analyzing and triaging security events to determine the severity of a threat or incident
- Responding to security incidents to mitigate immediate and advanced persistent threats
- Conducting root cause analysis to prevent future occurrences
- Maintaining and updating security tools and technologies
- Conducting security audits to identify vulnerabilities and prevent exploits
A typical day as a SOC analyst looks like investigating alerts based on priority using SIEMs, EDRs, and IPS/IDS. This often involves looking at minor incidents as well as false positives. While no one day will look alike, working as the first line of defense frequently means examining logs and investigating incidents.
While these responsibilities are carried out by the security operations center and its analysts, day-to-day tasks will depend on whether you are a Tier 1, 2, or 3 SOC analyst.
Tier 1 analysts truly are the first line of defense. They’re asked to monitor the network through the SIEM and triage alerts as they come in.
Tier 2 analysts perform more in-depth analysis, focusing on better understanding the root cause of security alerts and how systems are impacted.
Tier 3 analysts perform the most advanced type of investigations. These veterans have highly technical skills such as malware analysis and threat hunting, which are used to track complex security threats.
How quickly you advance up the tiers isn’t as much about experience as it is about mastering the skills and having the passion to move up the ranks. You can expect to spend a couple of years at each tier before moving on to the next one.
Are SOC Analysts in Demand?
According to the U.S. Bureau of Labor Statistics, from 2023 to 2033, information security analyst positions are expected to grow by 33%.
To put that into perspective, the average growth rate for all professions is just four percent. All other computer-related occupations are expected to grow by just 12%.
So, what’s causing this rapid rise in demand for cyber security analysts? Let's take a look.
Industry Trends
The consistent rise in cyber attacks drives the increase in cyber security roles, particularly SOC analyst roles.
As the chart below indicates, we see an increase in data breaches almost every year. So long as companies continue to be hacked, they'll continue to bolster their defenses by beefing up their security operations centers with analysts such as yourself.
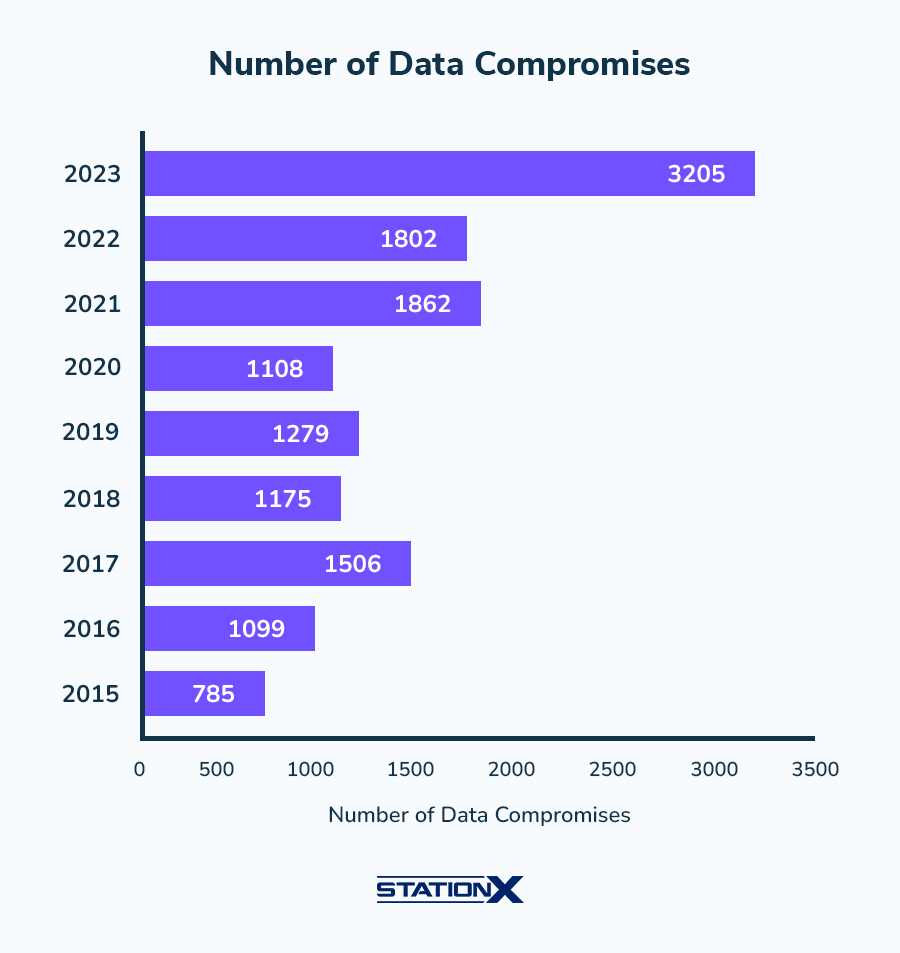
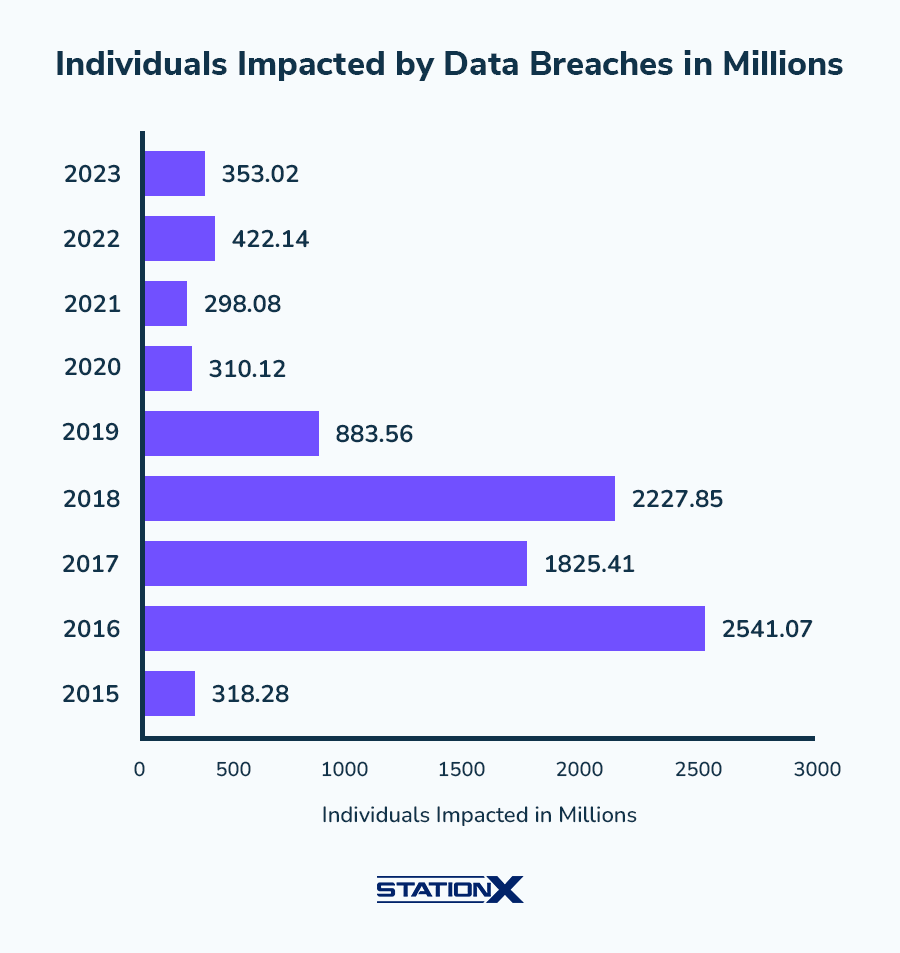
Employers are keenly aware of the prevalence of digital crime and the financial havoc it can cause.
It’s not just major companies that want to protect their assets; it's also mid-size and small ones. As many as 60% of small companies close shop within six months of a data breach, so companies of all sizes are investing more in online security.
Today, and more than ever, big and small companies are keenly aware of the impact of digital threats. But companies of all sizes have also been known to cut corners and save a buck where they can. With respect to investing in their cyber security infrastructure, this may have been easier than it is now.
In the past decade or so, several regulations surrounding how our digital information is protected have been signed into law. Acts such as Gramm-Leach-Billey, PCI DSS, GDPR, and many others now require companies to keep their client's information safe properly. Doing so means allotting an ever-growing budget into their cyber defenses.
While SOC analyst and cyber security analyst are different positions, many companies conflate the two. For the purpose of collecting stats in this article, we will use statistics that speak to both terms.
Employment Statistics
Millions of new job postings for cyber security-related positions like SOC analyst are posted yearly.
While there is an ever-growing demand, companies are struggling to find the right candidates to fill them. Globally, there are 3.5 million unfilled cyber security positions. In the US alone, there are 750,000 unfilled positions. The demand is there, but talented cyber professionals are tough to come by, leading to a global talent shortage.
67% of organizations worldwide have reported staffing shortages. While these shortages lead to an inability to prevent and respond to threats, they also represent an opportunity for aspiring cyber professionals.
As of this article, over 7,000 cyber security analyst roles are open in the US alone. As previously mentioned, SOC analyst positions are expected to grow by 332% from 2023 to 2033, compared to only a 12% growth rate for computer-related occupations overall.

Key Industries Hiring SOC Analysts
When it comes to who is hiring these analysts, not all industries are created equal. As you’ll see, the more sensitive the information an industry handles, the more digital security analysts they’ll want to hire.
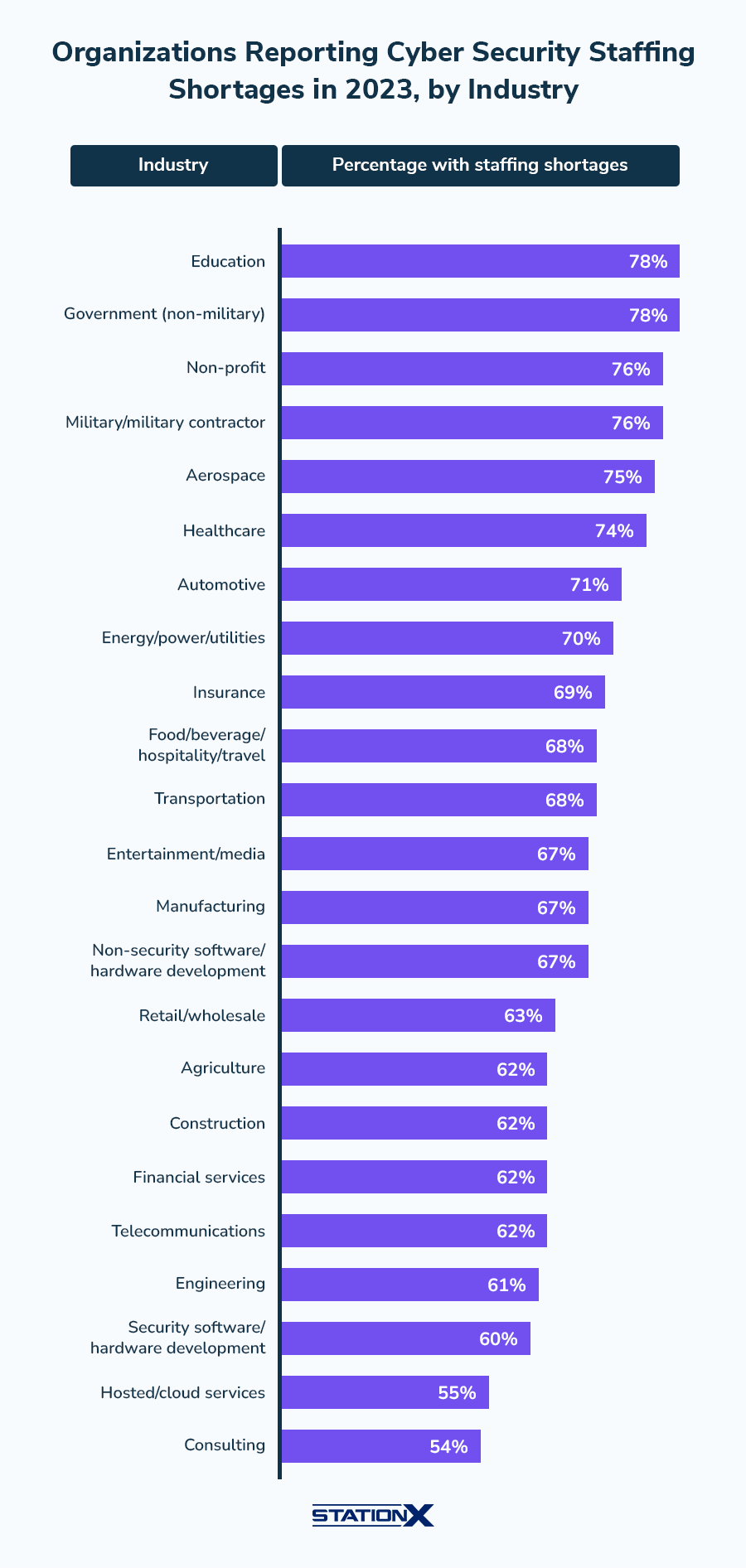
Financial Services
When it comes to financial data, it’s paramount that it’s protected. This data is so valuable that governments almost always step in to impose regulations.
In the US, one of the most stringent regulations is the Payment Card Industry Data Security Standard (PCI DSS), which ensures that companies working with financial data are implementing the following security measures:
- Restricting access to physical and digital assets
- Training employees on how to handle sensitive information properly
- Updating soft and hardware
- Using the most secure encryption to ensure data is protected
- Create secure networks
- Regular vulnerability testing
Companies that breach compliance can face millions in fines—so there's a huge financial incentive to strengthen digital security and avoid these costly penalties.
Information Security Courses Bundles
Want lifetime access to expert-led cyber security training? Explore our Information Security Course Bundles — one-time purchase packages covering top topics like Ethical Hacking, Cloud, Linux, DevSecOps, and CompTIA certifications.
Healthcare
Like financial institutions, the healthcare industry must also abide by regulations such as HIPPA and HITECH.
Our health information is extremely sensitive and private. Recognizing this, the government requires healthcare providers to meet strict standards, compelling hospitals to either hire third-party cybersecurity firms or build their own dedicated cybersecurity departments.
Despite their efforts, hospitals and healthcare providers are prime candidates for being hacked. Not only is the data valuable and will always find a buyer on the dark net, but taking down a hospital or provider can result in millions of dollars in lost revenue and even a loss of lives.
In early 2024, Change Healthcare experienced one of the most significant cyberattacks in U.S. healthcare history. Criminals gained access to personal information, payment details, and insurance records, ultimately causing the company a projected loss of over a billion dollars.
Government and Defense
Governments are prime targets for cyber gangs and nation-state cyber actors. They’re a treasure trove of data that can put an entire nation at risk if in the wrong hands. Governments must secure national security information and critical infrastructure to mitigate cyber espionage and attack risks.
While some governments may be late to realize the importance of protecting digital assets, it looks like they’ve finally come around. In 2018, the US created the Cybersecurity and Infrastructure Security Agency (CISA).
According to CyberSeek, between May 2022 and April 2023, the federal government had 8,376 cyber security job openings. You can expect this number to rise as countries continue to grasp the importance of shoring up their digital assets.
Technology and Telecommunications
Stealing trade secrets is a big business, so much so that IP theft increased from $822.3 million to $1.12 billion from 2022 to 2023. Companies big and small are targeted for their proprietary information that, if stolen, can give malicious companies a major edge. China, in particular, is the main culprit for intellectual theft.
Recently, the US government put a man colluding with the Chinese government behind bars after he stole sensitive files from GE. He sent the stolen information to an accomplice working for China, aiming to provide the Chinese government with a competitive advantage in designing and manufacturing gas and steam turbines.
In a recent case of cyber espionage, Chinese hackers infiltrated several major U.S. telecommunications companies—including AT&T and Verizon—and reportedly targeted phone calls involving President Donald Trump and Vice President J.D. Vance.
Tech and telecommunication companies are under constant threat of attack. This threat landscape means companies are always looking for top talent and are willing to pay handsomely to find it.
Manufacturing
At first thought, you may not consider the manufacturing industry to be a major target of hacks, but in 2023, it suffered more hacks than any other industry.
Many reasons make manufacturing a prime target, including its use of dated software and hardware and its importance to society. For this reason, many hacking groups target manufacturing companies for ransomware attacks.
While manufacturers may not directly hire cyber security professionals, they will hire third parties to protect their assets.
Driving Factors
As these industries continue to rely on digital systems, the attack surface expands, making them even bigger targets for cybercriminals. Pair this with the ever-growing cybercrime business carried out by gangs with the financial backing of some of the world’s most powerful governments, and it’s no surprise that hacks continue to rise.
How Much Does a SOC Analyst Make?
How much you can make as a SOC analyst depends on several factors, including your skills, experience, where you live, and even the hours you work.
Many companies have a follow-the-sun model that may require some analysts to work nights. If you’re one of these night owl analysts, you can expect your compensation to be adjusted accordingly.
There are also different types of SOC analyst roles, including a SOC 1, 2, and 3 analyst and a SOC manager.
Salary Overview:
Entry Level Positions:
Lower-level SOC analysts with less than one year of experience can expect to make an average of $65,841 in total compensation—including bonuses and overtime pay.
Cyber security analysts with one to four years of experience make an average of $73,009. This average is based on salaries culled from over 1,920 early career SOC analyst positions.
Mid-Career:
Between five to nine years of experience, you can expect to make around $89,533. By this time, you would most likely be considered a SOC 2 or 3 analyst, or you may be working in a managerial capacity.
Senior-Level Positions:
Experienced SOC analyst are highly coveted, and their compensation reflects this. Those who have 10-15 years of experience as analysts make an average of $102,914.
Those that have 20 or more years of experience have an average salary of $110,623.
Factors Influencing Salary:
As mentioned, there are a number of factors that influence the size of your paycheck.
For instance, the more expensive the area the company is based in, the higher your salary will be. You’ll notice this when applying to remote digital analyst roles that offer different salaries based on your location.
The experience you bring to the table is the most impactful variable of all. If you have years of experience and have mastered tools and knowledge you’ll be using on a daily basis, you can command a higher salary compared to those applying for the same role but who lack experience.
The sector in which you work also impacts your salary. Those working for tech companies, in the banking industry, or in healthcare will typically make more than, say, government employees.
Lastly, even if you don’t have hands-on experience, you can still negotiate a higher salary if you have a number of certifications to your name. We’ll go over SOC-related certifications later, but certifications such as CySA+, CISSP, and GSOC will help you stand out.
Becoming a SOC Analyst
Even if you have little to no experience in IT, you can still acquire the skills necessary to become an entry-level SOC analyst in a short amount of time. By obtaining the right knowledge and certifications, you can apply for SOC positions.
Key Knowledge and Skills
By identifying and learning the most common SOC analyst tools and skills, you can quickly put yourself in a prime position to land a SOC analyst job.
Some of these tools and skills include:
- SIEM: A security information and event management system is a tool you’ll be using every day to collect and analyze logs.
- Log analysis: Most of your day will be spent sifting through logs to identify threats.
- Firewalls: One of the best ways to prevent malevolent actors from accessing your network is to learn how to use a firewall.
- Vulnerability scanner: These scanners look through your network to find vulnerabilities before the bad guys do.
- Incident handling and documentation: Much of this position revolves around handling and properly documenting incidents. Understanding how to respond to an incident and effectively document it is a must.
- Programming skills: While not a must, employers like to see that you have an understanding of languages such as Python, PowerShell, Bash, and SQL.
Employers also want to see that you have a firm understanding of network security protocols and architecture, communication skills, and problem-solving skills.
Tech & Cyber Security Resume Writing Services
Ready to land your dream cybersecurity job? Our Resume Writing Services apply ATS-optimized, industry-specific expertise to boost your interview rate by an average of 60% — trusted by thousands of tech professionals worldwide.
SOC Analyst Certifications
If you don’t have Bonafide hands-on experience as a SOC analyst, you can still prove your prowess to employers by gaining certifications pertinent to the role. There are a number of certifications companies find valuable. However, some are more authoritative than others.
We’ll divide these certifications into two categories: entry-level and intermediate, and advanced and specialized.
Group One: Foot in the Door Certifications
These are the SOC-related certifications you’ll need to secure a SOC 1 analyst position:
- Sec+: Most employers will expect to see this entry-level certification on applicant resumes.
- CySA+: CompTIA’s Cybersecurity Analyst certificate tests you on an array of skills you’ll need as a SOC analyst.
- GSEC: The GIAC Security Essentials Certification tests you on network security, incident handling and response, exploit mitigation, and web communication security.
- CSA: One of the most in-depth exams, obtaining the Certified SOC Analyst certification proves to employers that you can handle the responsibilities of a Tier 1 or Tier 2 SOC analyst.
- BTL 1: Blue Team Level 1 is part exam and part course. To obtain the certification, you must pass both. While not as popular as other certifications, earning it still shows that you have the necessary skills to be a SOC 1 analyst.
You can save up to 30% on CompTIA exam vouchers, including Security+ and CySA+.
Group Two: Advanced and Specialist Certifications:
You’ll want to acquire these certifications as you progress from Tier 1 to Tier 2 and even 3.
- CISSP: The Certified Information Systems Security Professional certification will test you on your ability to design, implement, and manage an organization's cyber security needs.
- GCIH: GIAC Certified Incident Handler is a specialist certification that will test your ability to respond, detect, and resolve security incidents.
- Azure Security Operations Analyst: This certification tests how skilled you are at using Microsoft’s tools to address and mitigate threats.
Are SOC Analyst Jobs Remote?
A few years ago, the answer to this question would have been a resounding yes. However, with more companies now calling employees back to the office, remote positions have become less common—though plenty of remote SOC analyst roles are still available.
Current Job Market Trends
While the move towards remote work may have lost steam since 2020, many companies are still allowing employees to work from home. This is especially true in industries experiencing talent shortages, such as cyber security.
When searching for remote US-based SOC analyst roles on Indeed, we found more than 300 fully remote roles. Remote work used to be more pervasive, especially during and just after the pandemic. However, there has been a shift towards onsite and hybrid work.
Remote jobs are still available but are most often aimed at senior SOC analysts, so the odds of you scoring a remote cyber security analyst role increase as you gain experience. That being said, plenty of companies are still willing to hire remote workers in any position.
Considerations for Remote SOC Analysts
If you want to secure a remote role, you’ll need to ensure you’re using a secure home office environment with reliable internet access that adheres to organization security policies and protocols. If you can’t adhere to the aforementioned, you likely won’t be offered a remote position.
Conclusion
There is currently a talent shortage for SOC analysts.
The SOC analyst role is one of the fastest-growing cyber security roles. Research from ManageEngine even shows that more than four in five companies admit they have five or fewer security analysts or don’t have enough analysts to run a SOC efficiently.
The time is ripe to pursue a cyber analyst role. Even if you lack the experience, you can quickly use online resources and pursue certifications that will make your resume stand out to employers.
To learn the skills you need to begin your new SOC analyst role confidently, we encourage you to join the StationX Master’s Program. With access to over 30,000 courses and labs, career guidance, mentorship, and much more, it’s the best way to pursue your future cyber security career.
To get started learning about this complex and changing field, take The Complete Cyber Security Course Bundle. Containing five courses and over 50 hours of on-demand video, this bundle will lay the foundation for all your cyber security training.
The Complete Cyber Security Course Bundle includes:
- The Complete Cyber Security Course! Volume 1: Hackers Exposed
- The Complete Cyber Security Course! Volume 2: Network Security
- The Complete Cyber Security Course! Volume 3: Anonymous Browsing
- The Complete Cyber Security Course! Volume 4: End Point Protection
- The Complete Cyber Security Course Practice Test - Volume 1




