Kali Purple promises to be your innovative cyber security distribution designed specifically for the defensive side of the cyber realm, offering you a comprehensive toolkit that caters to various aspects of network defense. This newly released platform is based on the NIST Cybersecurity Framework and provides you with a comprehensive suite of tools and features to bolster your security posture.
In this article, we will delve into the unique features and capabilities of Kali Purple, explore the differences between it and the traditional Kali Linux, and examine how it aligns with the NIST Cybersecurity Framework. We will also take a closer look at some of the new tools incorporated into Kali Purple, discuss the concept of SOC-in-a-box architecture, and provide guidance on obtaining and installing the distribution.
Join us as we take a first look at Kali Purple and explore the ins and outs of this impressive platform.
What Is Kali Purple?
Kali Purple represents a novel addition to the Kali Linux ecosystem, creatively tailored for cyber security professionals and ethical hackers who focus on defensive security strategies. As an extension to the renowned Kali Linux platform, Kali Purple seems uniquely positioned to address the needs of its target audience by leveraging the NIST Cybersecurity Framework.
The NIST Cybersecurity Framework 1.1 comprises five core domains that provide a high-level, strategic approach to managing cyber security risk:
- Identify: Recognize the organization's assets, systems, and data, and understand the associated cyber security risks.
- Protect: Implement safeguards to ensure the delivery of critical infrastructure services, including access control and data security.
- Detect: Emphasize timely detection of cyber security events through continuous monitoring and anomaly reporting.
- Respond: Take appropriate actions upon detecting a cyber security event involving response planning, communication, and mitigation.
- Recover: Restore services and operations affected by a cyber security event, focusing on recovery planning and continuous improvement.
Unlike traditional Kali Linux, which you may know for its use in offensive security, Kali Purple expands the platform's capabilities by integrating an array of defensive tools and resources designed to equip you with the ability to proactively identify, respond to, and mitigate cyber security threats. This strategic approach should allow Kali Purple to function as a complementary solution within the Kali Linux family rather than replacing the existing platform.
Despite being in its early stages of development, Kali Purple has already garnered interest from the cyber security community, with anticipation building around future updates and enhancements that could further refine and expand its feature set and demonstrate clearer use cases. As the platform continues to evolve, Kali Purple could prove to become a valuable resource to help you strengthen your defensive posture.
How Is Kali Purple Different?
Kali Purple distinguishes itself from its Kali Linux counterpart by offering a distinct and innovative set of tools and layouts tailored to meet your specific demands as a defensive cyber security practitioner. This divergence is evident not only in the tools and resources provided but also in the platform's overall architecture and design philosophy.
One of the most striking differences between Kali Purple and traditional Kali Linux is the inclusion of new categories of tools specifically curated to bolster defensive security capabilities. These tools, which will be explored in greater detail in subsequent sections, represent a significant departure from the predominantly offensive-oriented toolset found in standard Kali Linux distributions.
Additionally, Kali Purple is built upon the latest Debian kernel, ensuring optimal performance, security, and compatibility with modern hardware. It also incorporates the most up-to-date desktop environments that offer a more refined and user-friendly experience.
Desktop Environments included with Kali 2023.1:
- Xfce 4.18 - With big changes to Thunar file management and panel management.
- KDE Plasma 5.27 - With window tiling, widgets, and adding LTS for this version.
- GNOME - Expecting a major update soon, but some tweaks have been made by Kali within this build. Such as using F4 to open the terminal from the Nautilus file manager.
Another key differentiator is the introduction of the SOC-in-a-box architecture. This innovative design integrates a diverse suite of security operations center (SOC) components into a modular, connected platform, streamlining workflows and facilitating improved collaboration between security professionals.
The intent behind using Kali Purple as a SOC In-A-Box can be described as setting up multiple machines that monitor a network in various ways. Additionally, you could use them to connect as a red team/blue team exercise. One thing that seems to point to this is the way the tools are broken out during the installation process. More on that later.
Kali Purple also features Kali Autopilot, a powerful attack script-building capability that allows you to automate various tasks and processes, further enhancing the platform's versatility and adaptability.
Kali Purple Hub
Also introduced is Kali Purple Hub, which is designed to allow the community to upload practice pcap files and your own custom Kali Autopilot scripts.
Moreover, Kali Purple boasts the latest Python release, ensuring compatibility with contemporary Python-based tools and libraries. The new Python 3.11.2 implements many updates ahead of the next stable version. Here are a few of the changes in this version:
Python 3.11.2
- Fine-grained error location in tracebacks.
- Speed increases of between 10-60%.
- New standard library modules (tomllib).
- Interpreter improvements.
- New typing features.
You can read more on the Python Release Notes.
It is worth noting that as package maintainers work on updating their packages to the latest version, there are some notable behavior changes in Python. Namely, installing older packages with pip may not always function properly. Kali's recommended method during this time is to use apt install python3-<package>. When 2023.4 comes out towards the end of the year, this may be the only method supported.
By embracing these advancements and strategically expanding its focus to encompass both offensive and defensive security, Kali Purple has demonstrated a commitment to developing a formidable addition to the Kali Linux ecosystem, further solidifying its position as a comprehensive and versatile solution for cyber security professionals.
What New Tools Come With Kali Purple?
Kali Purple introduces a suite of new tools that align with the five domains of the NIST Cybersecurity Framework (CSF) 1.1: Identify, Protect, Detect, Respond, and Recover. This alignment ensures that the tools provided cater to a broad range of defensive cyber security tasks, further pointing to Kali Purple's future potential as a comprehensive solution for security professionals.
As a note, we found that many of these newly announced tools weren't available by default in this first release. Instead, many of them needed to be downloaded and installed by following the directions in the Community Wiki. Even more, at the time of writing, a few of the tools have challenges with regard to executing them on the device. This is perhaps continued evidence that this is an early distribution that will require regular updates.
Identify
In this domain, tools such as GVM (Greenbone Vulnerability Management) are crucial in assessing and identifying potential vulnerabilities within an organization's infrastructure. By continuously scanning systems and networks, GVM enables security teams to stay ahead of potential threats and maintain a strong security posture.
Needs to be installed
- Installation instructions: https://gitlab.com/kalilinux/kali-purple/documentation/-/wikis/101_30:-GVM
Protect
Kali Purple includes a variety of tools aimed at bolstering an organization's protective measures. For example, Elastic Security, a powerful Security Information and Event Management (SIEM) solution, consolidates and analyzes security data from various sources, facilitating rapid detection and mitigation of potential threats. However, it's worth noting that some users have reported issues with setting up Elastic Security in Kali Purple.
Needs to be installed
- Installation instructions: https://gitlab.com/kalilinux/kali-purple/documentation/-/wikis/101_40:-Elastic-Agent
As noted above, there are known issues with getting all the dependencies installed.
Detect
The Detect domain focuses on monitoring and analyzing network activity to identify potential security incidents. Tools such as Arkime, a network forensics platform, excel in this area, providing detailed insights into network traffic and enabling the early detection of malicious activity. Malcolm, another network monitoring and analysis tool, complements Arkime, though it is known to have setup issues in Kali Purple.

Needs to be installed
- Installation instructions: https://github.com/arkime/arkime
Needs to be installed
- Installation instructions: https://gitlab.com/kalilinux/kali-purple/documentation/-/wikis/401_20:-Malcolm-Installation
As noted above, there are known issues with getting all the dependencies installed.
Respond
In the event of a security incident, efficient response is crucial. Kali Purple offers TheHive, an incident response and forensic tool, to aid security teams in managing and coordinating their response efforts. TheHive provides a collaborative environment where team members can share information, track progress, and streamline the incident response process.
Needs to be installed
- Installation instructions: https://github.com/TheHive-Project/TheHive
Recover
The final domain of the NIST CSF 1.1 involves restoring systems and services to normal operation after a security incident. While Kali Purple does not explicitly introduce tools focused on recovery, the integration of incident response and forensics tools, such as TheHive, can aid you in the development of effective recovery strategies and ensures a swift return to normal operations.
Kali Purple's new tools are intended to provide comprehensive coverage across the five domains of the NIST Cybersecurity Framework, enabling security professionals to effectively identify, protect against, detect, respond to, and recover from cyber threats. With its design to provide a powerful and specialized toolset, Kali Purple aims to enhance how you approach defensive cyber security.
If you want to learn about other tools that come with Kali Purple as part of the core Kali Linux suite, take a look at our article on the 25 Top Penetration Testing Tools for Kali Linux.

What is SOC In-A-Box
In today's rapidly evolving cyber security landscape, the need for a holistic, integrated approach to security operations has never been more crucial. SOC In-A-Box, a key feature of Kali Purple, addresses this need by offering a streamlined, centralized solution for managing security operations and incident response.
SOC In-A-Box, or Security Operations Center In-A-Box, is an innovative architecture that aims to consolidate essential defensive cyber security tools and processes into a single, cohesive platform. This integrated approach allows you to efficiently monitor, analyze, and respond to threats, vulnerabilities, and incidents in real time.
By bringing together disparate tools and capabilities, SOC In-A-Box empowers you with a unified view of your security posture, thereby enabling you to make informed decisions and take swift, decisive action in response to emerging threats.
Kali Purple's SOC In-A-Box offers you several advantages. It will simplify deployment and configuration, making it easier for you to get up and running with minimal effort. Additionally, the platform's modular design facilitates the seamless integration of various tools and technologies, ensuring you can tailor your security operations center to meet your unique requirements. More on this in the next section.
Furthermore, SOC In-A-Box can foster collaboration and information sharing among your team members, promoting a more effective and efficient approach to incident response and threat mitigation. It could also help you reduce reliance on multiple, disparate solutions, streamlining your security infrastructure and reducing the complexity of managing a comprehensive cyber security program.
Although, a real decision on this may need to wait for the future development of Kali Purple.
How Do I Get Kali Purple?
Getting your hands on Kali Purple is pretty much like getting any other Kali distro. Head over to their website and go to downloads.
One thing you'll notice right away is the limited options compared to what we're used to seeing on Kali. There are no pre-built VM images, no ARM images, nor any of the rest. While it could be that customs images do come out, we believe that the presence of only the ISO file indicates what we've mentioned earlier in this article.
The intent of Kali Purple seems to be focused being on configurable on-the-fly, so you only install the specific defensive toolsets that you want the machine to focus on.
Let's speed through the installation for an example. While everything else appears exactly like any other Kali or Linux install, our first sense of the changes in Kali Purple occurs on the page where desktop environment selections are made.
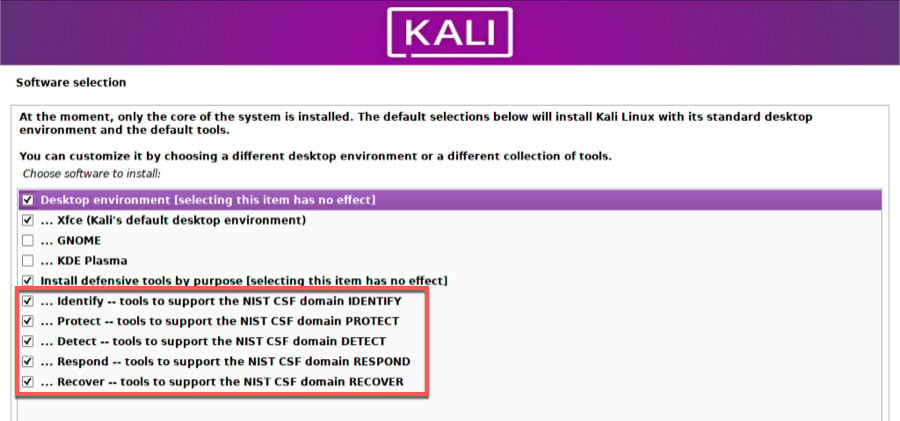
Here you can see the options for the categories of tools that we discussed above. All are aligned with the NIST Cybersecurity Framework domains. While at first, it may not seem like a huge shift, the implication is that you could mix and match these tools in various ways.
Kali Purple offers numerous tools for various defense tasks, including network monitoring, threat intelligence, incident response, and forensics, so the possibilities for device configuration are numerous. This could be why Kali hasn't released the VM images yet, and it's unclear if they intend to.
However, you can come up with particular builds that work for your unique use cases and create your own snapshot inventory for ready setup later. We cover all the steps you need to take in a straightforward manner in our article How to Install Kali Linux on VirtualBox & Start Hacking Now.
Conclusion
Kali Purple represents a significant leap forward for defensive cyber security, offering a powerful and versatile suite of tools that cater to each of the five domains of the NIST Cybersecurity Framework. By addressing the diverse needs of security professionals, Kali Purple equips you with the means to effectively identify potential threats, implement robust protection measures, detect malicious activity, respond swiftly to security incidents, and recover from cyber attacks.
Kali Purple's holistic approach to cyber security, in combination with its continued commitment to incorporating cutting-edge tools and features, makes it an indispensable asset for security professionals and organizations seeking to bolster their security posture.
As the landscape of cyber security threats continues to evolve, Kali Purple's focus on defensive measures and alignment with the NIST CSF 1.1 should allow it to remain at the forefront of the industry, providing you with the tools and resources necessary to navigate the increasingly complex world of cyber threats.
To develop blue team and SOC skills yourself, take a look at the below courses available in our Member Section.
Level Up in Cyber Security: Join Our Membership Today!









