Typosquatting is one of the most common URL hijacking methods.
A typosquatting website has a URL that almost matches another website’s, so you might accidentally visit it if you make a typo or spelling mistake when entering the real site’s URL.
While typosquatting can be used for relatively benign purposes, it can also be used for phishing and other serious cyber security attacks. For instance, it can lend a domain name seeming credibility when an internet user visits a malicious website designed to hijack their browser.
Read on to learn about typosquatting, how it works, what it can be used for, and how to protect yourself.
Let’s begin.
Typosquatting Definition
Typosquatting might not be the first technique that comes to mind when thinking of a cyber security attack, but it’s a prevalent one. Here’s everything you need to know about it.
What Is Typosquatting?
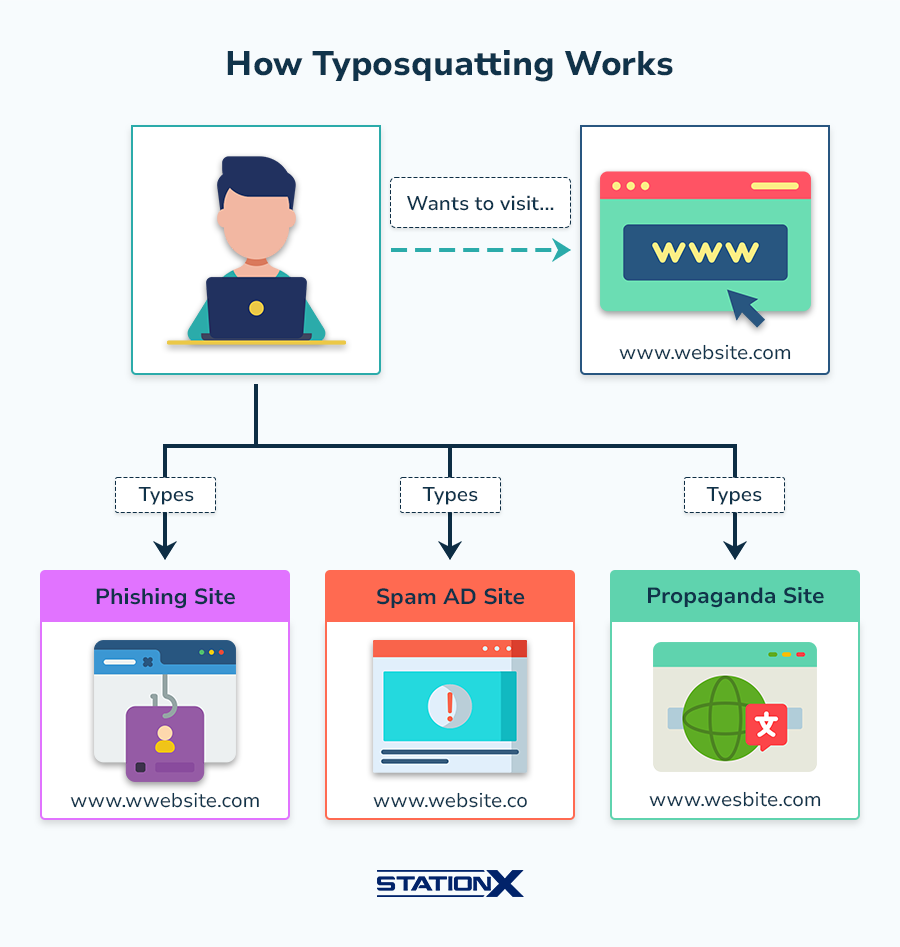
The term “typosquatting” combines “typo” and “squatting” and refers to a cyber security attack that tricks a user into visiting a site other than the one they intended by setting up a site with a similar URL.
A typo is a spelling mistake caused by inaccurate typing. In this context, squatting refers to secretly living in a place you’re not allowed to. A site set up for typosquatting usually relies on typos for visits and squats in the digital shadow of the site its URL is copying.
When someone makes a mistake while typing the website address they intend to visit, such as “ggoogle.com” instead of “google.com,” they get sent to the website the attacker set up.
Why is Typosquatting Used?
Typosquatting can be used for many reasons, most of which are nefarious.
It might be used to set up a phishing scam by making a replica of the site the user intends to visit.
For example, an attacker might register a domain under a misspelling of facebook.com (such as “faceboook.com”) and clone the real facebook.com. When someone visits it by accident, they’ll think they’re on the real Facebook, but they’ll be on a fake copy.
Such a phishing website could be used to steal your personal information or download malware to your device that later steals your information. For example, any username and password you enter on the site could be sent to the attacker.
Are you curious about the most common malware threats right now? Check out our guide, +65 Malware Statistics.
Or, if you enter your banking information on the site, the attacker could access your bank account and steal your money. They could also collect your personal information to commit identity theft by fraudulently opening credit accounts in your name.
Another reason someone might use this technique is to gain ad or affiliate revenue.
For instance, they might count on internet users making a typo in the URL they enter and being directed to their site, which they can fill with ads or affiliate links. They can then collect revenue from the ads or from revenue generated whenever users buy something after clicking an affiliate link.
A typosquatter might also intend to steal business from competitors.
Their website could redirect users to a competitor site instead of the one they intended to visit. Sites that get more visits tend to rank higher in Google search results, boosting the typosquatter’s search rankings and revenue.
Typosquatting might also spread propaganda or damage the legitimate site’s reputation.
For instance, someone could create a site with a URL that misspells a competitor’s and fill it with offensive material, hoping that people will think it’s the real site. They might also use the site to spread political, social, or other propaganda.
Finally, a typosquatter might set up a domain just to sell it to a legitimate site whose URL the typosquatter’s site mimics. The legitimate site might buy the fake site to keep its good reputation by preventing legitimate visitors from accidentally visiting it. A typosquatter that does this is called a cybersquatter.
What Harm Can Typosquatting Cause?
The damage that can be done by typosquatting depends on why the typosquatter made the site and claimed the domain in the first place.
As we’ve seen, these reasons can range from ploys for ad revenue to serious cyber security attacks that use malicious websites to steal your personal information.
Here are a few of the more dangerous consequences of typosquatting:
- Hacked social media accounts
- Malware infection
- Stolen money
- Identity theft
- Damaged reputation
- Misinformation or propaganda
Since typosquatting is a method rather than a goal, the sky is the limit regarding consequences. How harmful it is depends on how nefarious the website is and how often people accidentally visit it.
Typosquatting Methods
While typosquatting is simple to understand, it can take time to implement effectively. Apart from choosing a good URL likely to get accidental visits, typosquatters must also consider different methods for getting users to visit the link.
Information Security Courses Bundles
Want lifetime access to expert-led cyber security training? Explore our Information Security Course Bundles — one-time purchase packages covering top topics like Ethical Hacking, Cloud, Linux, DevSecOps, and CompTIA certifications.
Here are some of the most common typosquatting methods.
Common Typosquatting URLs
First, a typosquatter picks a target website and registers a similar but different URL; typically something a user might accidentally search themselves due to a typo or spelling mistake.
For example, a typosquatting URL might:
- Add another letter that sits next to one of the site’s actual letters on the keyboard (for example, “qamazon.com”)
- Add a repeated letter (for example, “aamazon.com”)
- Change British to American English spelling, or vice versa (for example, changing “colorhunt.co” to “colourhunt.co”)
- Change the top-level domain (TLD), AKA the URL suffix (for example, changing “google.com” to “google.co”)
However, some typosquatting websites don’t rely on the user attempting to type the legitimate domain names and making a mistake. Some rely on the user clicking a link, for example, in a phishing email.
In these cases, the attacker’s domain names might:
- Use hyphens to seem like the URL is related to the legitimate site (for instance, “facebook-social.com”)
- Be hidden under a hyperlink in the hopes that the user won’t check the URL underlying the linked text
- Use a character from a non-English alphabet that looks similar to a character in the legitimate URL (for example, using a Cyrillic letter that looks exactly like the English letter “a” but is made with the Unicode U+0430)
Can you tell which of these URLs is legitimate?
- www.amazon.com
- www.аmazon.com
- www.google.com
- www.gооgle.com
Once the attacker has picked a target website and URL, they register this domain.
Website Cloning
If they try to set up a phishing site, the typosquatter might clone the target website after picking a URL and registering the domain name.
An attacker can use many simple tools to clone a legitimate website (such as the Social Engineer Toolkit).
Once the website is set up, the typosquatter needs people to visit it. Depending on what URL they picked, they might wait for users to mistype the URL of the legitimate target website and be directed to their fake site.
However, if they picked a URL that requires the victim to visit the site by clicking on a link, they might attempt to get the victim to do so in the following ways.
Phishing Emails
One of the most common methods hackers and cyber criminals use to get victims to visit a link is phishing.
With this method, an attacker uses a pretext to try and trick users into clicking a link to a malicious website and divulging their personal information, which is then sent back to the attacker.
For example, they might send many people an email pretending to be a popular bank, claiming they’ve spotted unauthorized bank activity and requesting they verify their accounts by clicking a link.
If someone finds the phishing attempt credible and clicks the link, they might be presented with a cloned bank’s website and asked for their banking information, which, if entered, will be sent back to the attacker.
Spear Phishing and Social Engineering
Social engineering is a broad term that covers all methods of manipulating people into doing what you want. Phishing is an example of social engineering because it uses trust to manipulate someone into clicking a sketchy link.
Most phishing attempts are generic and don’t target a specific individual. Spear phishing is different because it uses a more sophisticated and personalized pretext to target a person or group.
A typosquatter who uses a URL mimicking a local sports group forum, for example, might target only those who are members of the legitimate forum with an email purporting to be from the forum. It might address them by name and tell them they must verify their forum account by clicking the link.
Pharming
Pharming is a sophisticated URL redirection hack that redirects users to a different website whenever they enter a legitimate URL.
This fake website is usually a clone of the legitimate one they were trying to visit, and when they enter their personal information, this is sent back to the attacker.
An attacker might accomplish this pharming attack by hacking your machine or the domain name server (DNS) of your ISP or another company hosting DNS records.
Typosquatting might be used in conjunction with pharming to make it less likely you spot the attack.
For example, if your URL entries are redirected by having your host file hacked or being a victim of an ARP poisoning attack, you get redirected to an alternative website. In that case, you might not notice the different URL once you arrive there if it’s a typosquatted URL.
Bitsquatting
Bitsquatting is a typosquatting technique that relies on low-chance bit-flip errors occurring after you enter a URL and your device submits a DNS request.
These errors, where single bits erroneously switch from 0 to 1 or from 1 to 0, are rare, but when they occur, they can change certain letters of certain URLs for websites when you try to visit them.
Bitsquatting also happens when someone makes a URL that is a single bit-flip away from being the same as a popular legitimate URL.
For example, in the Def Con 25 video above, Sam Erb demonstrates how a website he set up received traffic caused by single bit-flips during DNS requests.
CompTIA Security+ Voucher
Prepare to validate your security skills for less. Grab a CompTIA Security+ Voucher and save up to 30% on your exam through StationX’s authorized CompTIA partnership.
How to Defend Against Typosquatting
If you’re an individual, the best thing you can do to guard against typosquatting is to practice safe browsing. This means a few things:
- Check URLs
- Use an ad-blocker
- Avoid clicking links in emails, social media pages, and unknown senders
- Ensure websites have SSL certificates
- Learn to spot phishing attempts
Avoid clicking links whenever possible, especially when unsure of the source's credibility.
This partly means learning to spot phishing attempts, which often use generic greetings and try to generate a sense of urgency. You should also use an ad blocker because this can prevent typosquatting attacks that use malvertising.
Also, all legitimate sites should have a valid SSL or TLS certificate, which validates that all interactions on the website are encrypted.
If your browser warns you that this certificate is missing—perhaps by saying that “your connection isn’t private”—you should avoid entering any personal information on the site and even avoid it altogether.
If you’re an organization looking to stop your website from being cloned by a typosquatter, you should be proactive and register any potentially misspelled domains before a typosquatter could.
You can also use ICANN’s Trademark Clearing House to check whether your site’s being typosquatted. If you spot any sites, try to get them removed through legal action.
Typosquatting for Ethical Hacking and Red Team Engagements
Ethical hackers and penetration testers might not use typosquatting because it’s a social engineering attack that, to be successful, requires employees to remain unaware of it.
Pentesters and ethical hackers usually run their simulation attacks with the knowledge of the company or at least of the blue team.
Red teams, however, who can act without most of the company’s knowledge, might decide to use this attack method as part of their simulated attacks.
Are you curious about how red teams differ from penetration testers? Read our guide
A red team might send a spear phishing email to employees pretending to be their boss who’s emailing them from a personal account.
The email might request employees to log into the company’s internal website to make some changes and then provide a typosquatting link to a cloned version of the company’s website.
A red team might use such an attack not to assess whether stealing the employee’s information is possible but to see if they can “hook” (gain control of) the user’s browser.
They might use the Browser Exploitation Framework (BeEF) to hide malicious JavaScript code in the website’s header, which will hook the browser when the user visits the site. Then, they can perform any number of attacks and access much of the employee’s personal information.
If a real attacker managed to hook an employee’s browser, this could put the entire organization at risk, so if a red team achieves this, it’s a sign that organizational security and employee training need to be improved.
Want to learn more about the Browser Exploitation Framework (BeEF)? Check out our guide: How to Use the BeEF Hacking Tool
Conclusion
On its own, typosquatting isn’t necessarily harmful.
However, because it makes a website URL seem legitimate, it’s usually used for nefarious purposes such as phishing. It can even aid attacks that hook victims’ browsers, infect their devices, or create malicious sites.
Whether you’re an individual or an organization, if you’re looking to protect yourself from typosquatting, there’s no better way to do so than by understanding it and the methods used to do it, as well as the methods used to stop it.
Joining the StationX Master's Program will give you resources to understand how these social engineering techniques work and how to prevent them. It’ll also provide you with access to a community where you can ask questions to ensure you’re protecting yourself in the most effective way possible.
You can also dive deep into Kali Linux and Penetration Testing with our Ethical Hacking Course Bundle. Just click the banner below to start your hacking journey.




