Perhaps you’re here because you’ve found the term “Google dorking” or “Google hacking” in cyber security and want to learn more. Or perhaps you want to save time on web searches and improve your OSINT abilities. But do you find yourself overwhelmed with commands when you review all the search results on this hot-button topic?
Don’t worry, we’ve got you covered. With this Google dorking commands list, beginners can finally apply Google dorking straightaway. At the same time, advanced users can use this as a handy guide to pull down publicly available sensitive information from their servers before they could cause further damage.
Abusing Google dorks can get you in trouble legally and otherwise. See the difference between “reconnaissance” and “scanning” in the next section. When in doubt, skip the dork.
When you’re ready, let’s dive into these Google dorking commands.
What Is a Google Dork?
Most people know what a Google search is. A Google dork is an advanced Google search using only the search box. Combining Google dorks in a single query helps you filter out irrelevant content.
To understand how to Google dork, you need to grasp several essential points:
The Anatomy of a Successful Hack
Five phases characterize a successful hack into a target, such as a website or a server:
- Reconnaissance: Gathering intelligence about the target.
- Scanning: Exploring the target, clicking links, using remote scanning tools.
- Gaining access: Actively exploiting the target to get access.
- Maintaining access: Establishing a way to easily reconnect to the target if your connection breaks or you wish to return later.
- Clearing tracks: Exiting the target without a trace, removing all exploits and back doors, clearing logs.
You can use Google dorking to conduct step 1 above, but once you click on the search results, submit data, or access links without proper permissions, you enter step 2 and may be accountable for computer crimes punishable by law. Click with caution.
To Google dork, you include dork commands and operators in a Google query and interpret the search results as you see fit.
Google Dorking Command Generator
Say goodbye to the hassle of trying to remember the exact syntax for your Google Dorking commands! With our Google Dorking Command Generator, you can simply say what you need Google Dorking to do, and we will generate the command for you.

Top 15 Google Dorking Commands
For each of the following Google dorks, we’ll describe its function, the expected search results it returns, and why it’s useful, ending with a demonstrative screenshot.
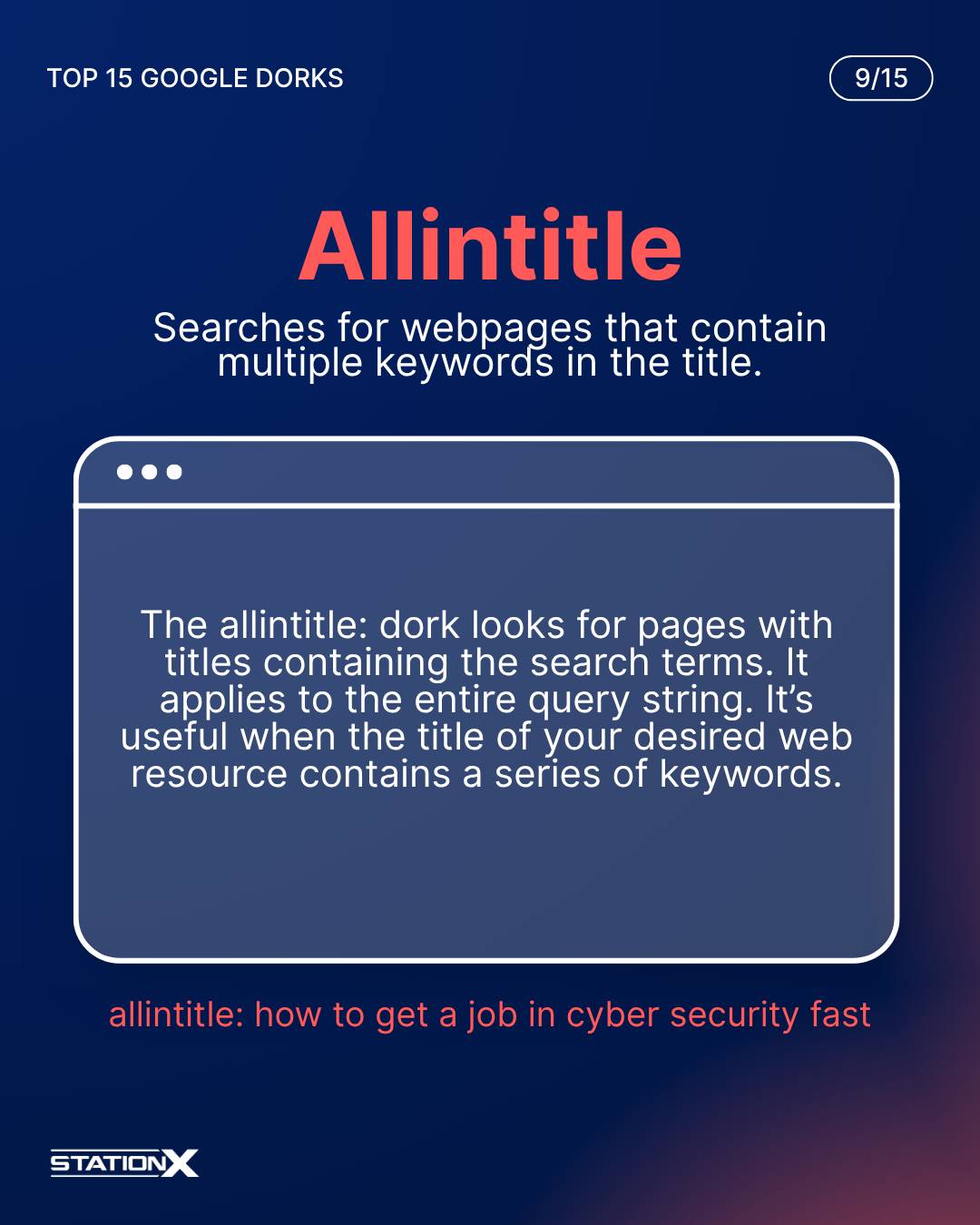
Allintitle:
The allintitle: dork looks for pages with titles containing the search terms. It applies to the entire query string. You can see each word in the query string in the title of each search engine result returned. It’s useful when the title of your desired web resource contains a series of keywords.
allintitle:cyber security essentials

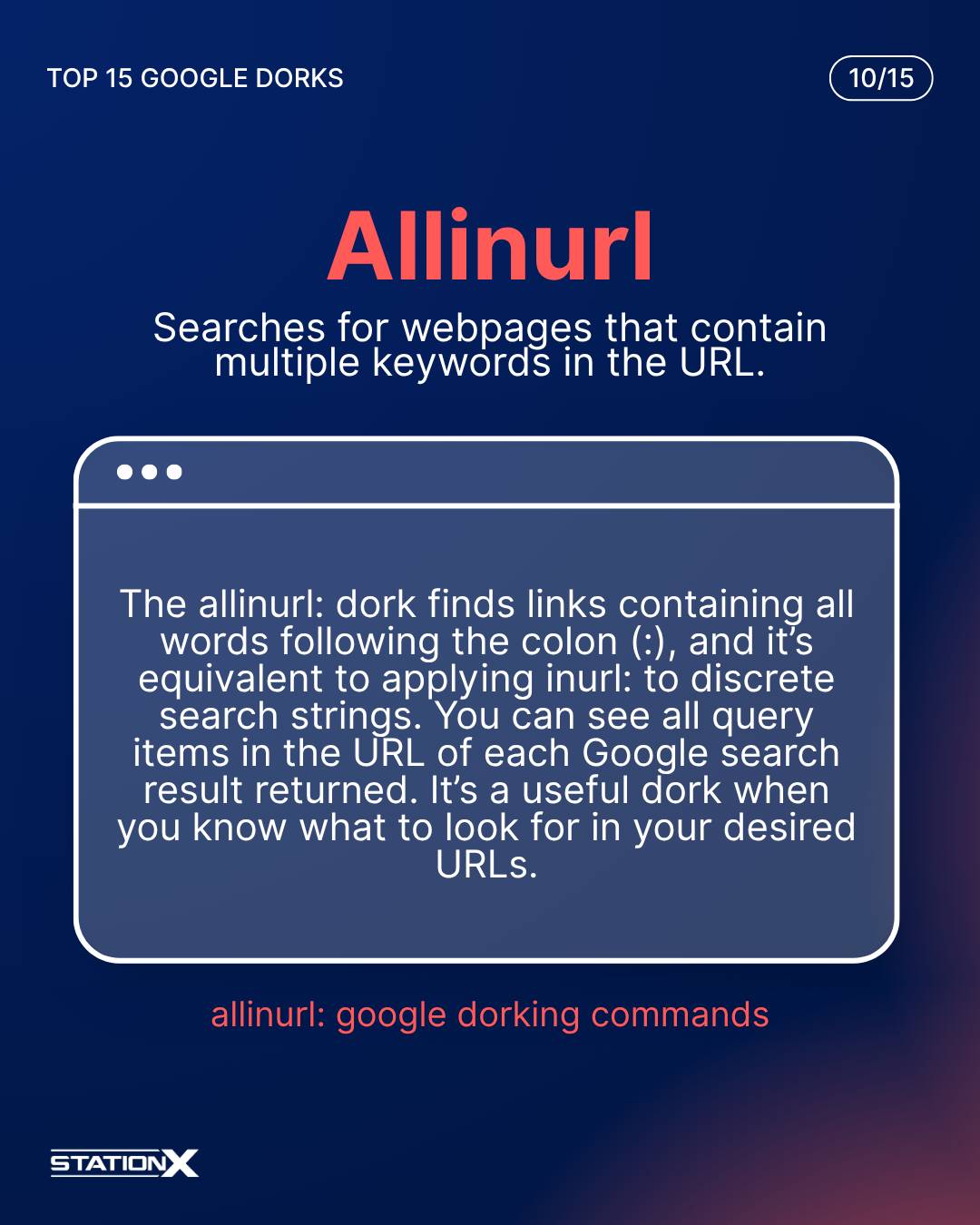
Allinurl:
The allinurl: dork finds links containing all words following the colon (:), and it’s equivalent to applying inurl: to discrete search strings. You can see all query items in the URL of each Google search result returned. It’s a useful dork when you know what to look for in your desired URLs.
allinurl:cyber security hacker

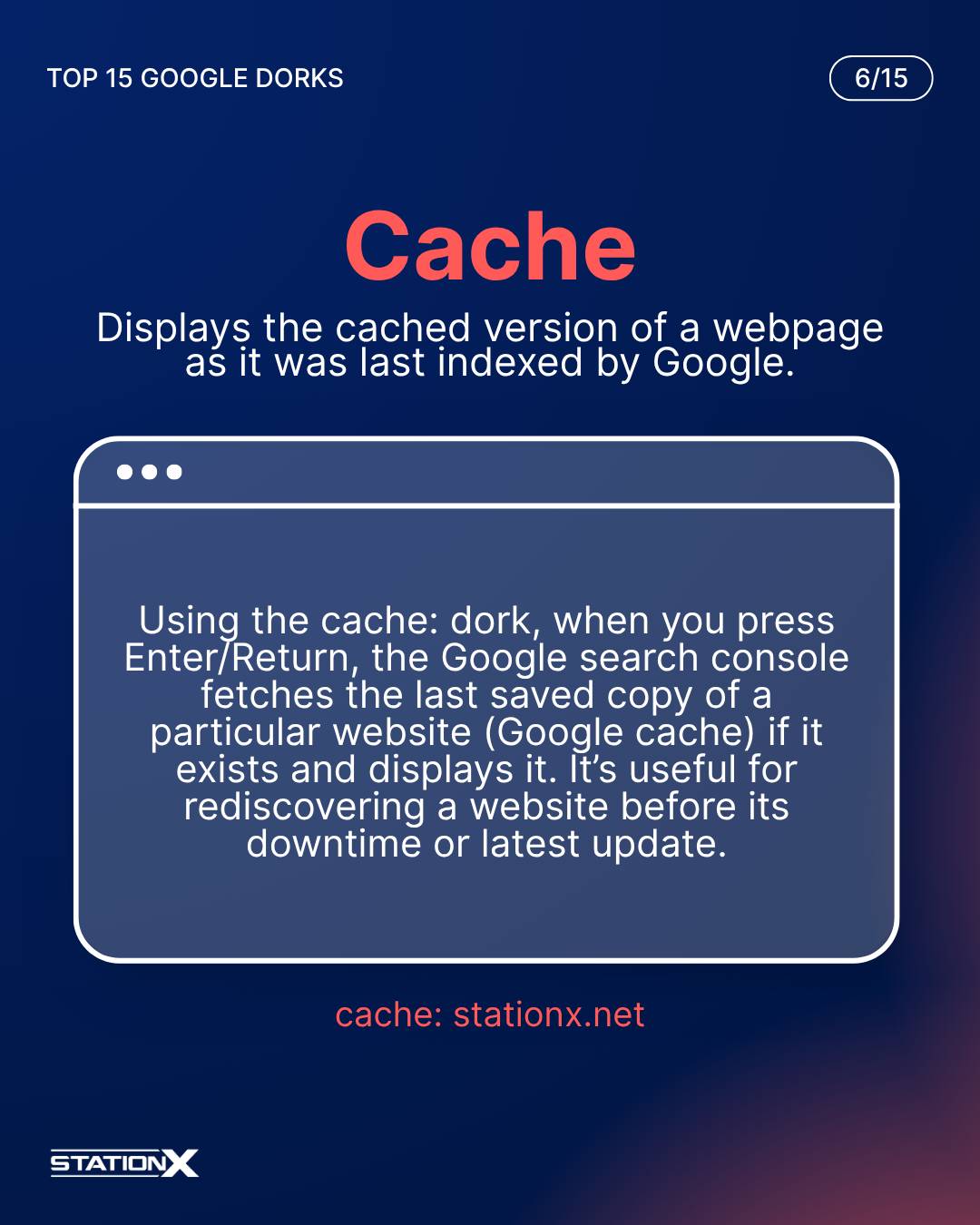
Cache:
Using the cache: dork, when you press Enter/Return, the Google search console fetches the last saved copy of a particular website (Google cache) if it exists and displays it. It’s useful for rediscovering a website before its downtime or latest update.
cache:courses.stationx.net


Define:
The define: dork returns definitions of a word or phrase. The Google search results are various dictionary definitions of the query item. It’s useful when you want to find a word or phrase’s meaning conveniently.
define:reconnaissance

Ext:
The ext: dork restricts the returned web addresses to the designated extension, such as PDF or XLS. Unlike most other dorks, it requires additional keywords/dorks in the search bar, or it’ll return no results. The Google search results have the designated file extensions. You can use it to find leaked passwords and cameras in penetration testing (pentesting).
ext:php site:microsoft.com

Filetype:
The filetype: dork restricts the returned web addresses to the designated file type, such as PDF or XLS. Unlike most other dorks, it requires additional keywords/dorks in the search bar, or it’ll return no results. The Google search results have the designated file type. It’s necessary for pentests such as bypassing paywalls to access resources.
filetype:pdf site:apple.com

Info:
The info: dork returns pages that convey information about a website. The Google search engine results are the website’s cache, similar pages, and pages that link to it. It’s useful when you want to find third-party resources about a web page.
info:www.stationx.net -site:www.stationx.net

Intext:
The intext: dork finds websites containing the query string. You can see the query string in the text body of each Google search result returned. It’s useful when the content body of your desired web page contains a certain keyword. In the demonstration below, we’re looking for web pages of books with “munira” in the body but include “tom” anywhere.
intext:munira tom site:goodreads.com

Intitle:
The intitle: dork looks for pages with titles containing the search terms. You can see the query string in the title of each Google search result returned. It’s useful when the title of your desired web resource contains a certain keyword. In the example below, we look for all our pages containing “google” in the title.
intitle:google site:www.stationx.net

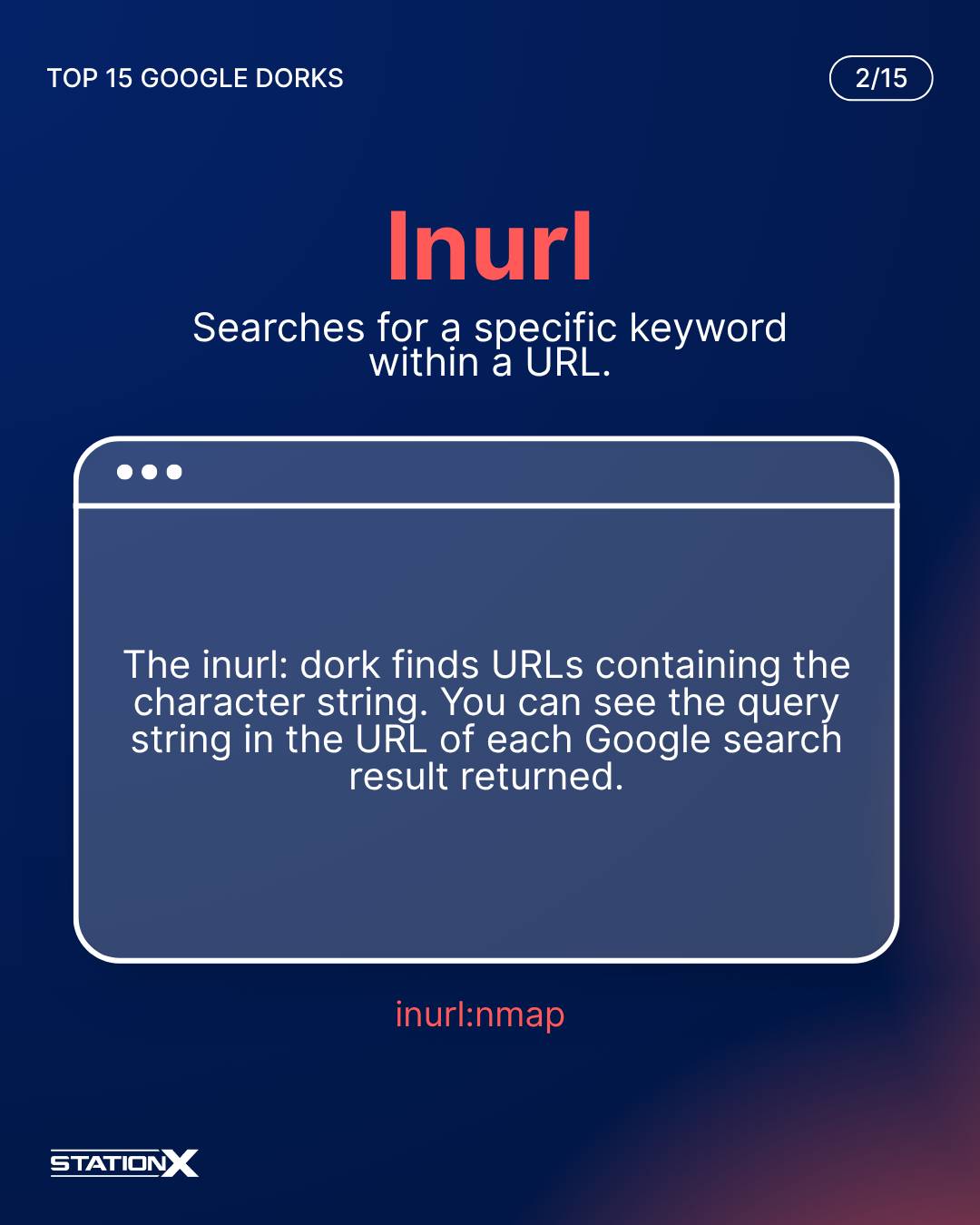
Inurl:
The inurl: dork finds URLs containing the character string. You can see the query string in the URL of each Google search result returned. In the example below, the additional dork is to exclude search results from our website. It’s a handy dork when your desired URLs follow a certain pattern.
inurl:stationx -site:www.stationx.net

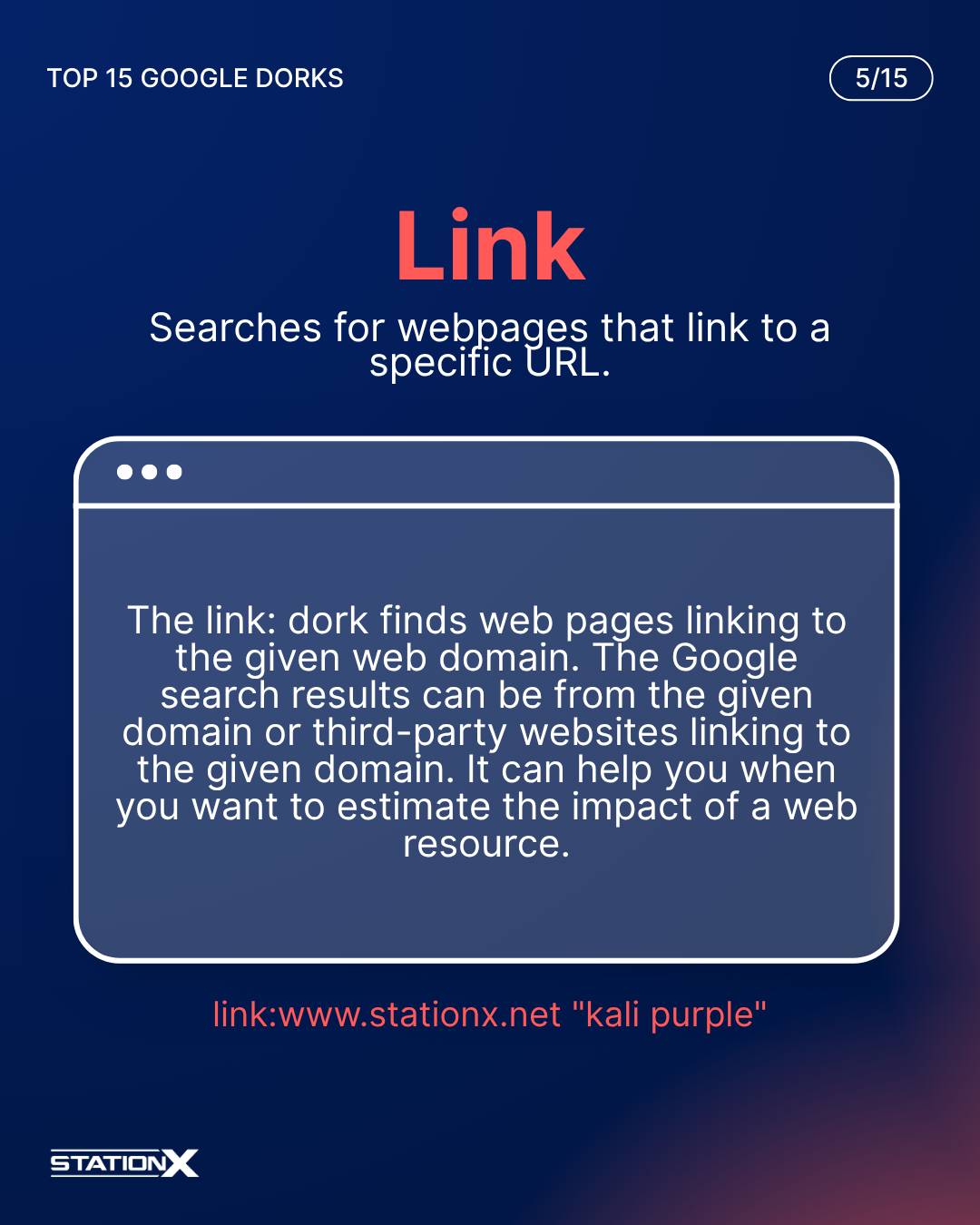
Link:
The link: dork finds web pages linking to the given web domain. The Google search results can be from the given domain or third-party websites linking to the given domain. It can help you when you want to estimate the impact of a web resource.
link:www.stationx.net "kali purple"

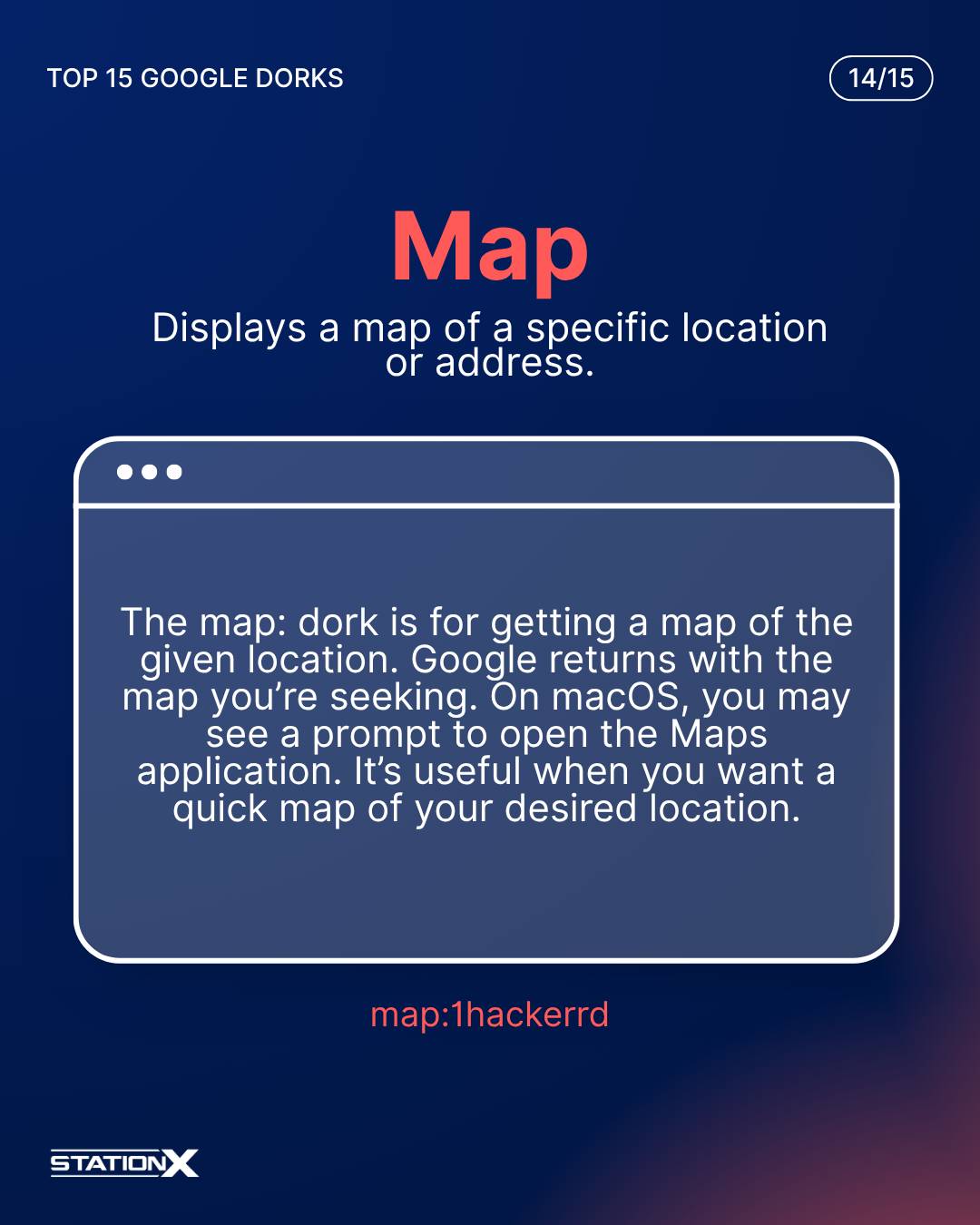
Map:
The map: dork is for getting a map of the given location. Google returns with the map you’re seeking. On macOS, you may see a prompt to open the Maps application. It’s useful when you want a quick map of your desired location.
map:1hackerrd

Phonebook:
The phonebook: dork is for getting a specific person or business’s phone numbers and contact information. The Google search may return no results or several. The screenshot demonstration below has to do with fictional US phone numbers. This command is helpful when you want to look up caller IDs.
phonebook:555-555-5555

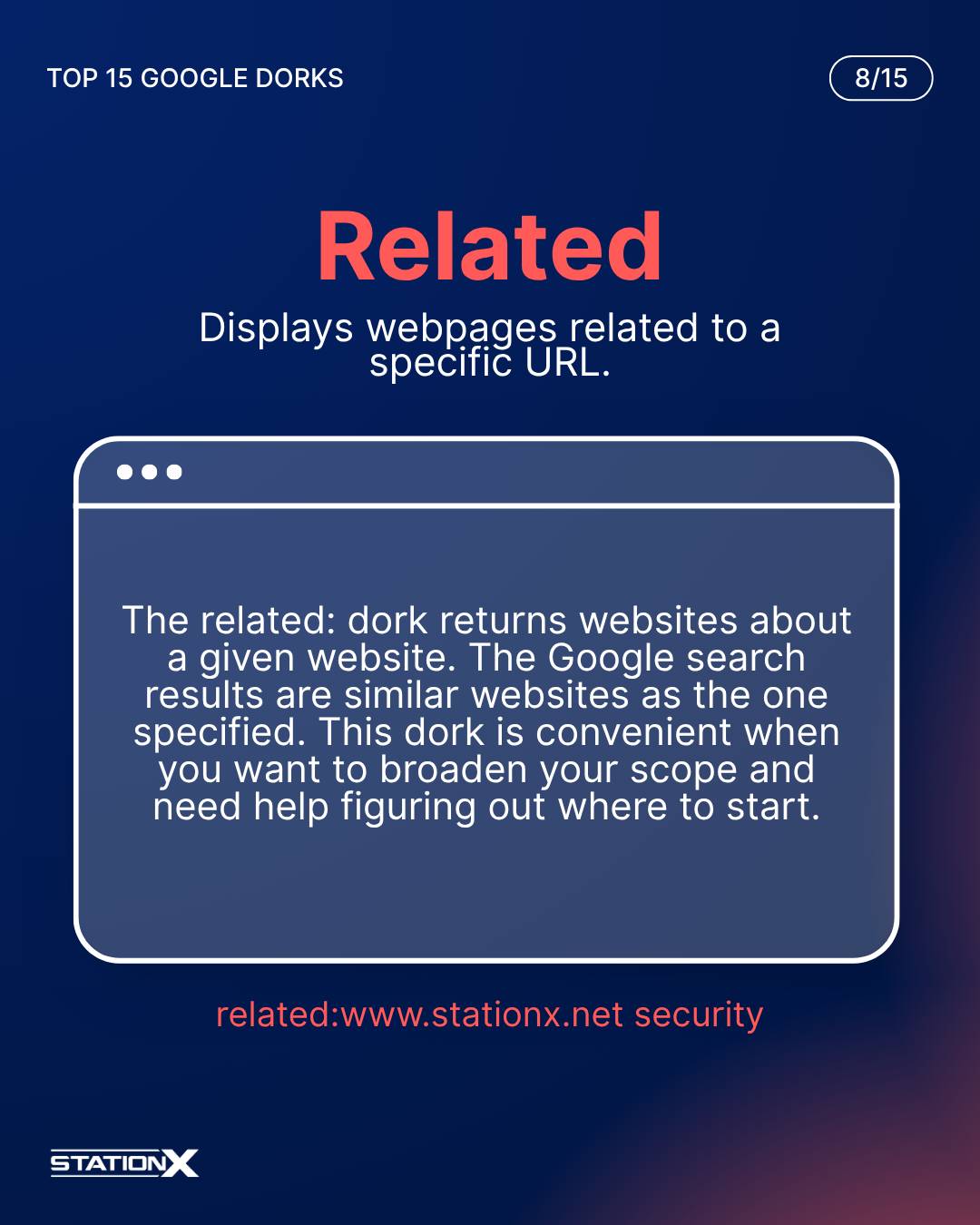
Related:
The related: dork returns websites about a given website. The Google search results are similar websites as the one specified. This dork is convenient when you want to broaden your scope and need help figuring out where to start.
related:www.stationx.net security

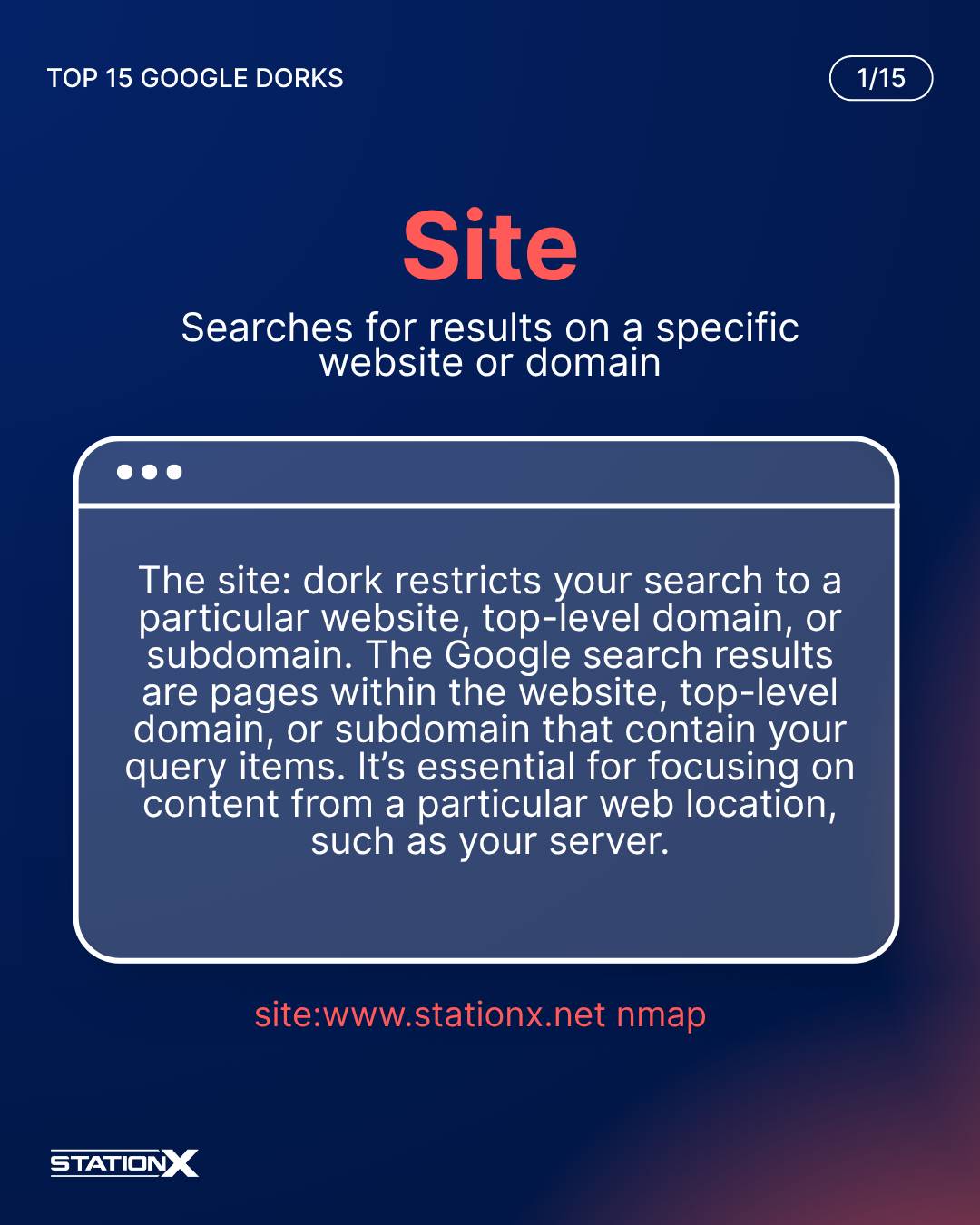
Site:
The site: dork restricts your search to a particular website, top-level domain, or subdomain. Additional query items are optional. The Google search results are pages within the website, top-level domain, or subdomain that contain your query items. It’s essential for focusing on content from a particular web location, such as your server.
site:www.stationx.net nmap

Conclusion
We hope this top 15 list of Google dorking commands helps you finish your work quickly, efficiently, and ethically. For more resources on Google dorking, check out our Google Dorking Cheat Sheet, How to Google Dork a Specific Website for Hacking, and our Google Dorking Course Bundle below, available at discount below. You can also consider our StationX Master's Program for complete cyber security training.
The Google Dorking Course Bundle includes:
- Learn OSINT Techniques From Scratch & OSINT Certification
- What Is Open Source Intelligence: OSINT Tools
- Top 5 Bug Bounty Tools and Tricks Course