If you want to know the difference between WPA2 and WPA3, you’ve come to the right place.
Over the past couple of decades, WiFi security protocols have gone through several iterations, evolving quickly to counter ever-increasing vulnerabilities and providing enhanced defenses against attacks.
Today, the most widely used and modern security protocols are WPA2 (WiFi Protected Access 2) and WPA3 (WiFi Protected Access 3).
In this article, you’ll learn everything you need to know about WPA2 vs WPA3 configurations and their key differences, including technical specifications, security implications, and the ongoing relevance of these protocols in secured wireless networks.
So, without further ado, let's try to understand them better.
A Brief History of WiFi Security Protocols
The first widely adopted WiFi security protocol was WEP (Wired Equivalent Privacy). However, it had significant vulnerabilities that made it susceptible to various attacks, such as packet sniffing and key recovery attacks.
The weaknesses in WEP's encryption methods led to the development of WPA (WiFi Protected Access) as a more secure alternative.
WPA was developed as a short-term emergency patch that addressed major vulnerabilities in WEP by incorporating TKIP (Temporal Key Integrity Protocol), which improved the encryption over WEP.
WPA2 (Wi-Fi Protected Access 2) became mandatory in 2004, and it required the use of the CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol) algorithm, which is based on the AES encryption algorithm.
Despite WPA2's improvements over WPA, new vulnerabilities and sophisticated attack methods brought about further enhancements in WiFi security.
WPA3, introduced in 2018, addresses these issues by providing more robust protections against attacks and offering stronger encryption mechanisms to ensure the confidentiality and integrity of data transmitted over wireless networks.
WPA2 vs WPA3
Now, let’s dig deeper to understand the technical differences and commonalities between WPA2 and WPA3.
Technical Overview of WPA2
As previously mentioned, WPA2 utilizes the AES encryption standard with CCMP for data confidentiality and integrity. It operates in two modes: “Personal” (pre-shared key) and “Enterprise” (using 802.1X authentication).
In Personal mode, users share a common passphrase, while in Enterprise mode, an authentication server manages individual user credentials.
Common Vulnerabilities in WPA2
While WPA2 significantly improved security over WEP and WPA, it still has vulnerabilities. One of the most notable ones is KRACK (Key Reinstallation Attack), which exploits weaknesses in the WPA2 handshake process, allowing attackers to decrypt traffic.
What is KRACK (Key Reinstallation Attacks)?
KRACK targets the four-way handshake used in WPA2 to confirm that the client and access point have the correct credentials. Attackers can reset encryption keys and decrypt data by manipulating and replaying handshake messages. Although patches have been released to mitigate KRACK, this has highlighted the need for more secure protocols.
Technical Overview of WPA3
Due to the severe vulnerabilities in WPA2, WPA3 was developed, introducing several new security features to address its shortcomings.
Individualized Data Encryption
WPA3 provides individualized data encryption, ensuring that data traffic between each device and the access point is encrypted separately. This prevents eavesdropping and enhances privacy, especially in public WiFi networks.
Information Security Courses Bundles
Want lifetime access to expert-led cyber security training? Explore our Information Security Course Bundles — one-time purchase packages covering top topics like Ethical Hacking, Cloud, Linux, DevSecOps, and CompTIA certifications.
Protection Against Brute-Force Attacks (SAE)
Simultaneous Authentication of Equals (SAE) is a secure key exchange method used in WPA3 to enhance security during the authentication process by making it resistant to offline brute-force attacks.
SAE replaces the pre-shared key (PSK) method used in WPA2, providing a more secure way to authenticate wireless devices. SAE resists offline brute-force attacks and makes it significantly harder for attackers to guess passwords.
Performance and Security Improvements
WPA3 also includes performance improvements that make it more efficient, especially in handling modern wireless networks. In fact, enhanced encryption methods provide better security without significantly impacting network performance.
Here’s a detailed comparison table highlighting the key differences between WPA2 and WPA3.
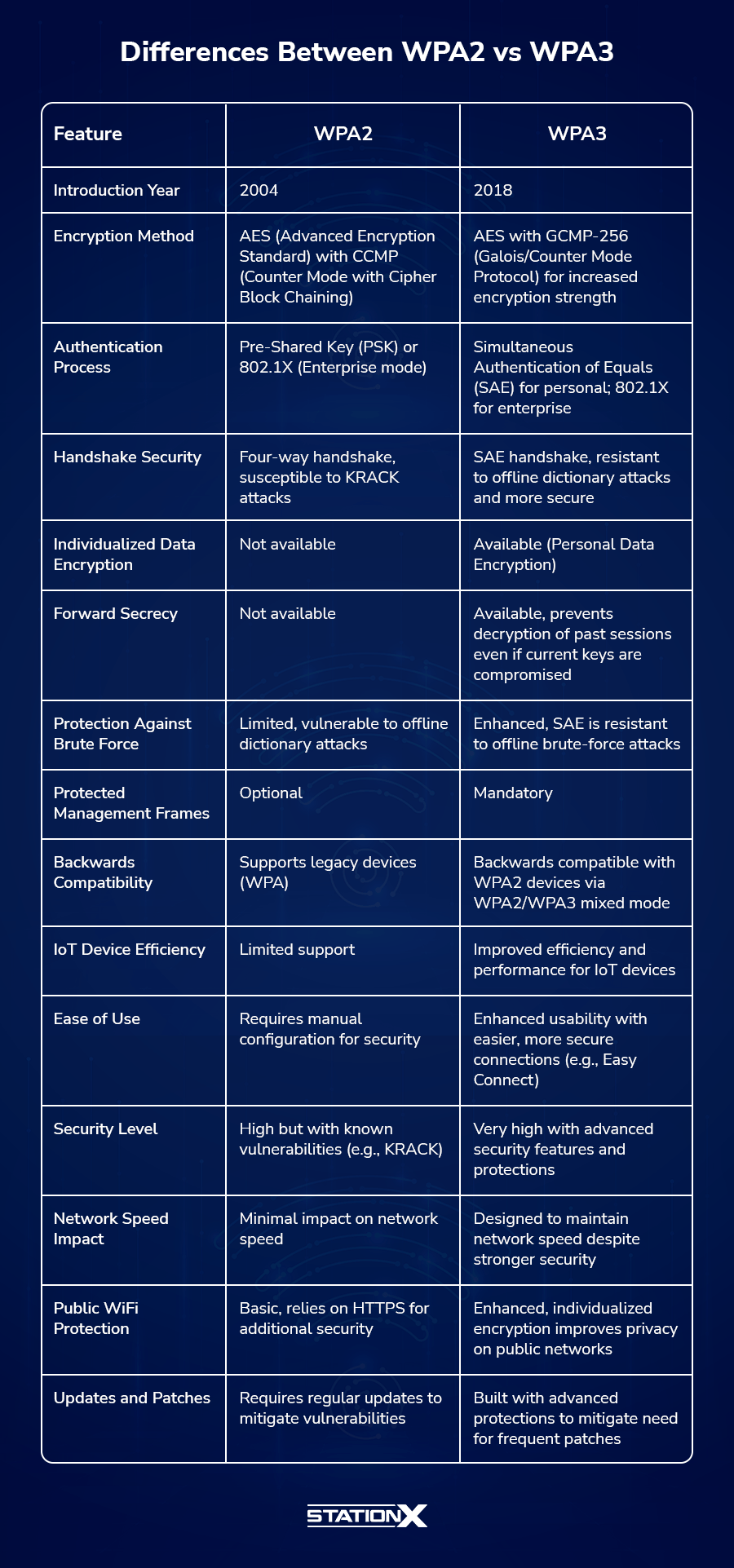
WPA2 vs WPA3 Security Implications
Understanding the security implications of different WiFi protocols is crucial, as both WPA2 and WPA3 offer robust security features. However, WPA3 includes enhancements that address vulnerabilities present in WPA2. Now, let’s see the security implications for both.
How WPA3 Mitigates Common WPA2 Attacks
Let’s now understand the key characteristics of how WPA3 mitigates common WPA2 vulnerabilities.
Cryptographic SAE
Another major enhancement for WPA3 is the use of cryptographic SAE, which means that data transmitted between a device and the access point can be intercepted and monitored by one or more other devices on the network.
Under WPA3, individual data encryption ensures that traffic between each device and the access point is uniquely protected from malicious eavesdroppers.
The use of individual data encryption also prevents the leakage of user data so that it can be read or monitored by malicious eavesdroppers.
Forward Secrecy
WPA3 can use forward secrecy, which keeps past sessions safe from attacks even if the current session key is compromised. This is provided by using ephemeral keys thrown away after each session.
With forward secrecy, an attacker who can see the current encryption key can’t decrypt past communication.
Protected Management Frames
WPA3 requires that all network devices support Protected Management Frames (PMF), providing additional protection for management frames.
These frames are important for network control and, if left unprotected in WPA2, can be used to carry a variety of attacks, including de-authentication and disassociation attacks. Securing management frames can increase a network's stability.
Security for IoT
IoT is an emerging field, and WiFi plays a very important role in building IoT networks. These devices are one of the biggest areas for concern, and new aspects of WPA3 facilitate security.
It provides better handling of IoT devices, which are some of the biggest security problems of our time.
By making the key-handling and encryption operations much more efficient, judicious WPA3 constrained-device implementations can achieve a very high level of security without penalizing performance.
Public WiFi Network Security
Security in public WiFi networks has been significantly improved because of WPA3. By introducing individual data encryption and forward secrecy, WPA3 ensures the traffic of users remains private and protected even when connected to open networks.
Regular Updates and Patches
Manufacturers must release regular updates and patches to mitigate potential vulnerabilities in the WPA implementations.
Additionally, network and security administrators should ensure that all corresponding WPA2/WPA3 devices are updated with the latest vendor-recommended firmware to protect against newly discovered threats.
What WPA2 Attacks Are Addressed in WPA3
WPA3 offers protection from various attacks when compared to WPA2, and here are some offensive security implications:
KRACK (Key Reinstallation Attack)
As mentioned earlier, the KRACK vulnerability in WPA2 exploits weaknesses in the four-way handshake process.
It allows attackers to eavesdrop on the handshaking between a client and a WiFi access point, inject their own modified frames, reset encryption keys, and decrypt traffic. With this vulnerability, hackers can sniff passwords, recover old data, and log into websites without authentication.
WPA3 addresses this issue by using the Simultaneous Authentication of Equals (SAE) handshake, which is resistant to offline dictionary attacks and prevents the key reinstallation that KRACK exploits.
Offline Brute-Force Attacks
WPA2 is vulnerable to attacks in which a malicious actor captures the traffic and uses computational power to guess the passphrase.
For this reason, one of the new features of WPA3 is an encryption scheme called SAE. This scheme is designed to resist brute-force attacks by requiring real-time interactions for each attempt to guess the passphrase rather than allowing attempts to be performed offline.
Additionally, it uses stronger data encryption algorithms than in WPA2.
Side-Channel Attacks
These attacks exploit devices' physical or timing characteristics to gain information about the encryption keys. For example, power consumption or electromagnetic emissions could be analyzed to extract cryptographic keys.
While side-channel attacks are generally sophisticated and require physical proximity, they threaten WPA3 security.
Advanced Cryptographic Attacks
Cryptographic research continually evolves, and new attack methods that could weaken the security of WPA3 may emerge.
For instance, weaknesses in the underlying algorithms or how keys are generated and managed might be discovered. Continuous research and updates are necessary to address such potential vulnerabilities.
Vulnerabilities Affecting WPA3
While WPA3 significantly improves security and performance compared to WPA2, it’s not entirely without vulnerabilities. Yet, WPA3's use of AES-GCMP for encryption and the SAE handshake significantly improves over WPA2. It even makes these attacks highly complex to perform.
For example, SAE is designed to be more resistant to offline dictionary attacks, ensuring that even if an attacker captures encrypted data, it would be infeasible to crack the key without direct interaction with the network.
Let’s see some of the vulnerabilities that impact WPA3 implementation.
Dragonblood Vulnerabilities
Security researchers identified a group of vulnerabilities that they collectively called Dragonblood vulnerabilities.
These are multiple vulnerabilities that exploit weaknesses in the WPA3 handshake process (SAE—Simultaneous Authentication of Equals). Attackers could potentially carry out many attacks exploiting these dragonblood vulnerabilities, including side-channel attacks to recover passwords, performing downgrade attacks that force a network to revert to less secure WPA2 protocols, and more.
Downgrade Attacks
This attack tricks a device into using an older, weaker WPA2 connection instead of the more secure WPA3. This can be achieved by targeting devices that support both WPA3 and WPA2.
Once a downgrade is achieved, hackers can crack the password using brute-force methods.
CompTIA Network+ Voucher
Prepare to validate your networking skills for less. Grab a CompTIA Network+ Voucher and save up to 30% on your exam through StationX’s authorized CompTIA partnership.
Side-Channel Attacks
These attacks exploit subtle variations in a device's processing time while handling WPA3 handshakes. By analyzing these variations, attackers can gather or crack the information about the underlying password.
However, these attacks are complex and require the attacker to be within proximity of the target device.
Misconfigurations
One of WPA3's main vulnerabilities is its implementation. Poor coding practices, incorrect configurations, or inadequate testing can introduce security gaps that attackers might exploit.
For example, a misconfigured device might not properly enforce the robust protections WPA3 is designed to provide.
Wireless Hacking Tools
While WPA3 is designed to thwart many known attack vectors, security professionals, ethical hackers, and penetration testers use wireless hacking tools to test its resilience.
These tools can analyze network traffic and attempt to crack weaker WEP/WPA/WPA2 networks. Understanding them can help you better secure WPA3 deployments by anticipating and defending against potential attack strategies.
| Wireless Hacking Tool | Purpose |
|---|---|
| Aircrack-ng | A suite of tools for monitoring, attacking, testing, and cracking WiFi networks. Used for WEP and WPA/WPA2 cracking. |
| Cowpatty | A tool used for brute-force attacks on WPA-PSK (Pre-Shared Key) networks. Used to crack WPA/WPA2 passphrases. |
| Reaver | An open-source tool for performing brute-force attacks against WiFi Protected Setup (WPS) PINs. Used to gain access to WPA/WPA2 networks with WPS enabled. |
| Wireshark | A network protocol analyzer that captures and displays data packets in real-time. Used for network troubleshooting and analysis. |
| Fern WiFi Cracker | A GUI-based tool used for network security auditing and penetration testing on wireless networks. Supports WEP, WPA, and WPA2. |
| Wifite | An automated wireless attack tool that can target multiple WEP, WPA, and WPS networks in succession. Used for automated WiFi hacking. |
| Kismet | A wireless network detector, sniffer, and intrusion detection system. Used to detect and analyze WiFi networks and devices. |
| Wifiphisher | A security tool used to launch phishing attacks on WiFi networks. Can create fake access points to capture credentials. |
| Bettercap | A powerful, flexible tool to perform various types of network attacks and monitoring. A modern alternative to Ettercap. |
| Hashcat | A fast and versatile password-cracking tool. Often used in combination with Aircrack-ng to crack WPA/WPA2 hashes. |
Conclusion
Evolving from WPA2 to WPA3 marks a significant advancement in the establishment of secure wireless networks. WPA3 addresses many vulnerabilities in WPA2, offering stronger encryption, better protection against brute-force attacks, and enhanced privacy features and performance.
While WPA2 remains widely used and secure with proper updates, WPA3 provides a more robust solution for modern wireless networks.
As WPA3 is a comparatively new standard, cybercriminals, ethical hackers, penetration testers, and security researchers are actively exploring ways to exploit security flaws in its implementation during various social events, forums, and capture-the-flag competitions.
Learn more about the ethical hacking and penetration testing career by joining our StationX Master's Program. The tailored learning experience through this program helps you improve your practical skills and provides vibrant community connections to accelerate your journey in cyber security.
You can get lifetime access to the CompTIA Network+ Training Bundle (N10-009): 4 Courses for a one-time purchase. This bundle includes everything you need to study effectively and prepare with confidence: 35 hours of on-demand video, 5 full-length practice exams, 19 quizzes, 300+ flashcards, mobile access, and a certificate of completion.
This CompTIA Network+ Training Bundle (N10-009): 4 Courses contains:




