Lost the TAR flags again? Or maybe you’re new to Linux and need the top terminal commands for files, folders, networking, and security. With so many utilities, it’s easy to feel overwhelmed.
This Linux Commands Cheat Sheet article serves both as a complete Linux cheat sheet and a practical study guide for CompTIA Linux+ and LPIC-1. We’ve organized the essentials by task - file and archive management (yes, all the TAR basics), permissions & ownership, processes & services, networking & troubleshooting, package management, and common security commands, so you can find what you need fast and build real command-line confidence. Download the cheat sheet here, keep it by your terminal, and scroll below to jump straight to the commands you need today.
Linux Command Line Cheat Sheet Search
Search our Linux Command Line cheat sheet to find the right cheat for the term you're looking for. Simply enter the term in the search bar and you'll receive the matching cheats available.
- Linux Command Line Cheat Sheet Search
- Essential Commands
- Shells and Environment
- Printing
- Text Processing
- File Transfer
- File Permissions
- System Information
- Process Management and Performance Monitoring
- Job Control
- User Management
- Networking
- Installing New Programs
- Security Tools
- Containers
- Scripting and Automation
- vi Editor Basics
- Linux Commands Cheat Sheet Conclusion
- Frequently Asked Questions
Essential Commands
We recommend that you memorize these commands. You’ll need them the most when operating Linux.
Shells and Environment
The shell controls how users interact with Linux. These commands manage environment variables, aliases, and the way the system interprets commands.
| Command | Description |
echo $SHELL | Display the current user’s shell. |
env | Show current environment variables. |
set | Display all shell variables and functions. |
export VAR=value | Set an environment variable for child processes. |
alias ll='ls -la' | Create an alias (example: ll for ls -la). |
unalias ll | Remove an alias. |
which command | Show the path to an executable. |
type command | Display how the shell interprets a command (alias, function, builtin, or file). |

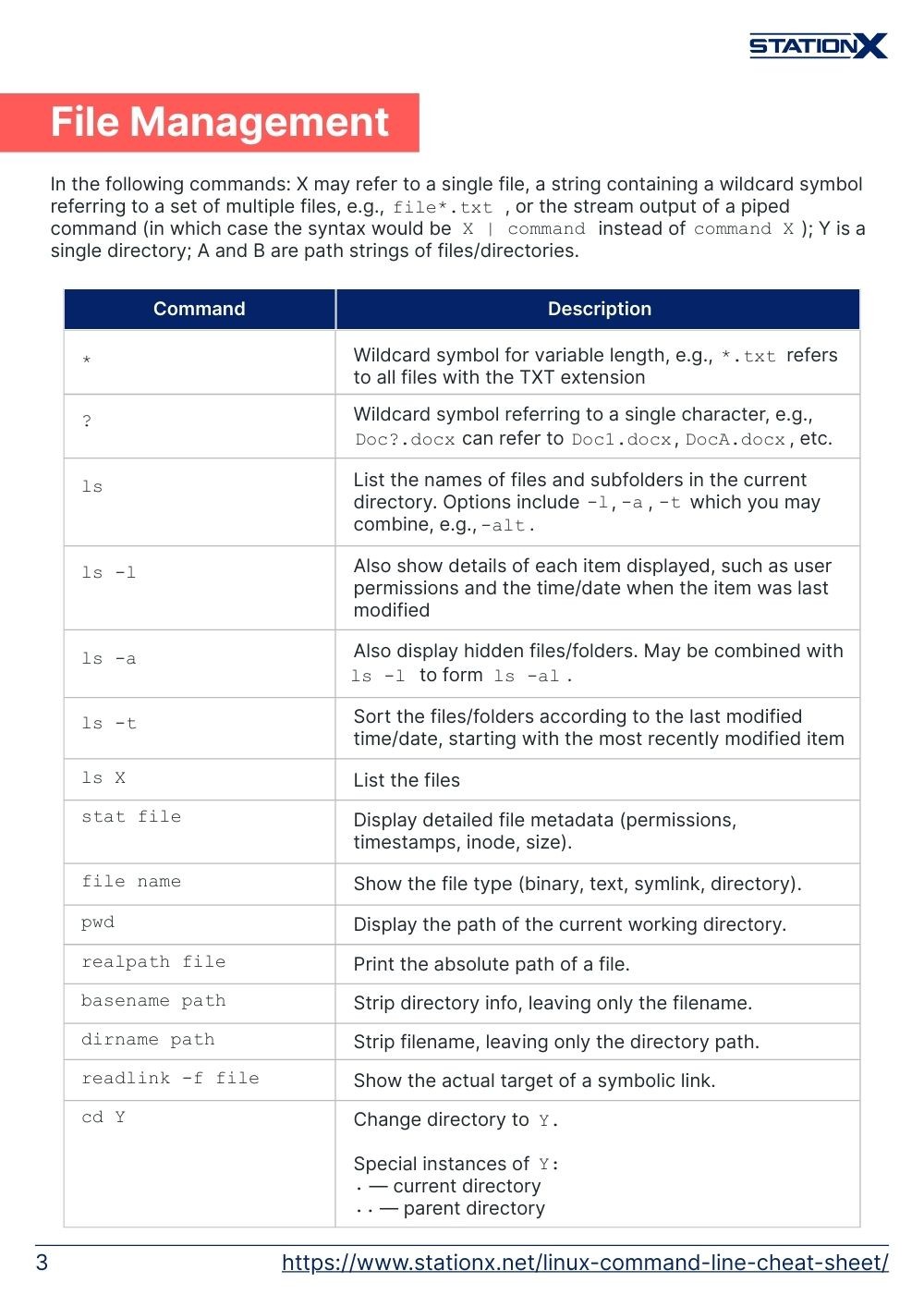
File Management
In the following commands: X may refer to a single file, a string containing a wildcard symbol referring to a set of multiple files, e.g., file*.txt, or the stream output of a piped command (in which case the syntax would be X | command instead of command X); Y is a single directory; A and B are path strings of files/directories.
| Command | Description |
|---|---|
* | Wildcard symbol for variable length, e.g., *.txt refers to all files with the TXT extension |
? | Wildcard symbol referring to a single character, e.g., Doc?.docx can refer to Doc1.docx, DocA.docx, etc. |
ls | List the names of files and subfolders in the current directory. Options include -l, -a, -t which you may combine, e.g., -alt. |
ls -l | Also show details of each item displayed, such as user permissions and the time/date when the item was last modified |
ls -a | Also display hidden files/folders. May be combined with ls -l to form ls -al. |
ls -t | Sort the files/folders according to the last modified time/date, starting with the most recently modified item |
ls X | List the files |
stat file | Display detailed file metadata (permissions, timestamps, inode, size). |
file name | Show the file type (binary, text, symlink, directory). |
pwd | Display the path of the current working directory. |
realpath file | Print the absolute path of a file. |
basename path | Strip directory info, leaving only the filename. |
dirname path | Strip filename, leaving only the directory path. |
readlink -f file | Show the actual target of a symbolic link. |
cd Y | Change directory to Y.Special instances of Y:. — current directory.. — parent directory |
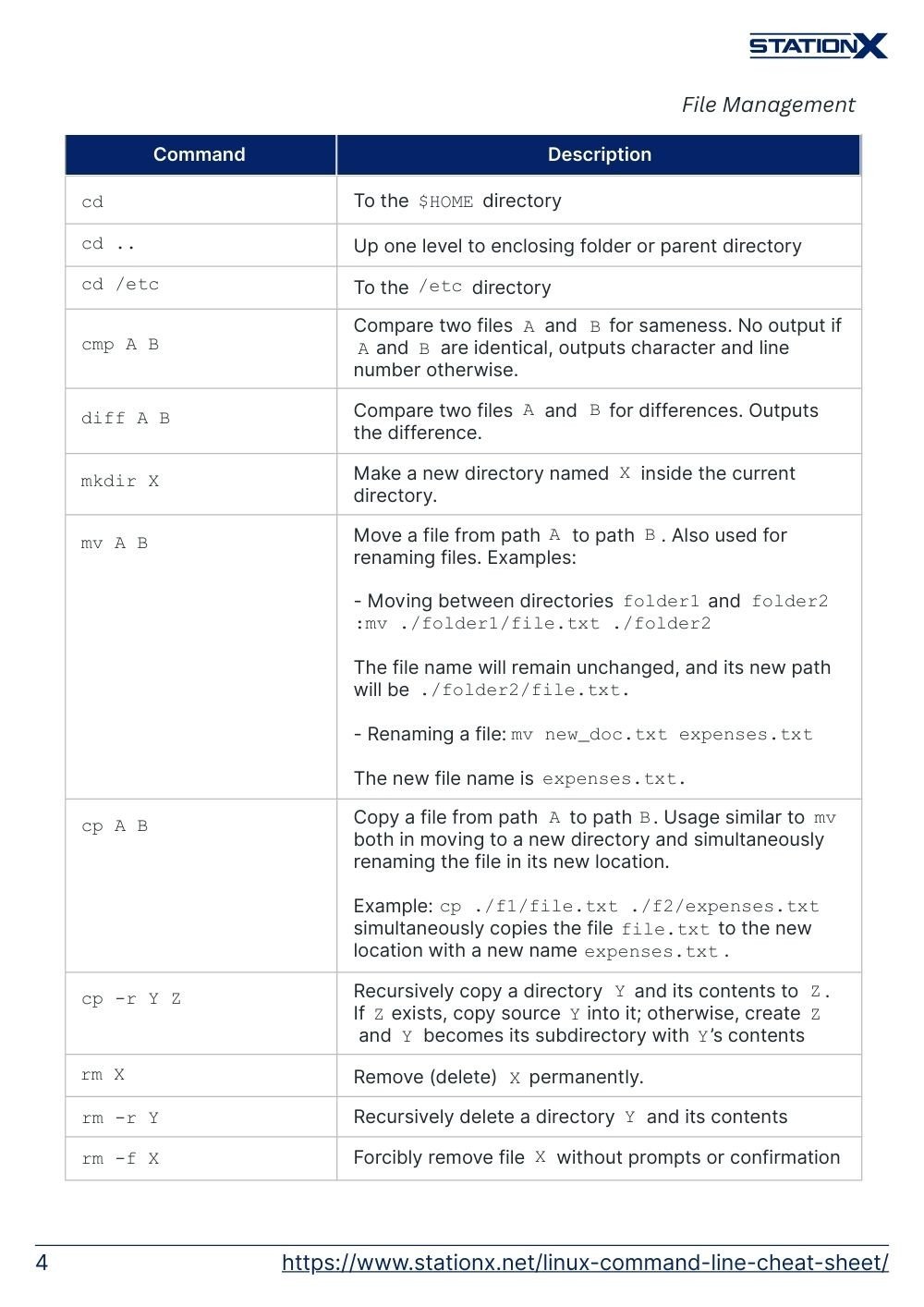
cd | To the $HOME directory |
cd .. | Up one level to enclosing folder or parent directory |
cd /etc | To the /etc directory |
cmp A B | Compare two files A and B for sameness. No output if A and B are identical, outputs character and line number otherwise. |
diff A B | Compare two files A and B for differences. Outputs the difference. |
mkdir X | Make a new directory named X inside the current directory. |
mv A B | Move a file from path A to path B. Also used for renaming files.Examples: - Moving between directories folder1 and folder2:mv ./folder1/file.txt ./folder2The file name will remain unchanged, and its new path will be ./folder2/file.txt.- Renaming a file: mv new_doc.txt expenses.txtThe new file name is expenses.txt. |
cp A B | Copy a file from path A to path B. Usage similar to mv both in moving to a new directory and simultaneously renaming the file in its new location.Example: cp ./f1/file.txt ./f2/expenses.txt simultaneously copies the file file.txt to the new location with a new name expenses.txt. |
cp -r Y Z | Recursively copy a directory Y and its contents to Z. If Z exists, copy source Y into it; otherwise, create Z and Y becomes its subdirectory with Y’s contents |
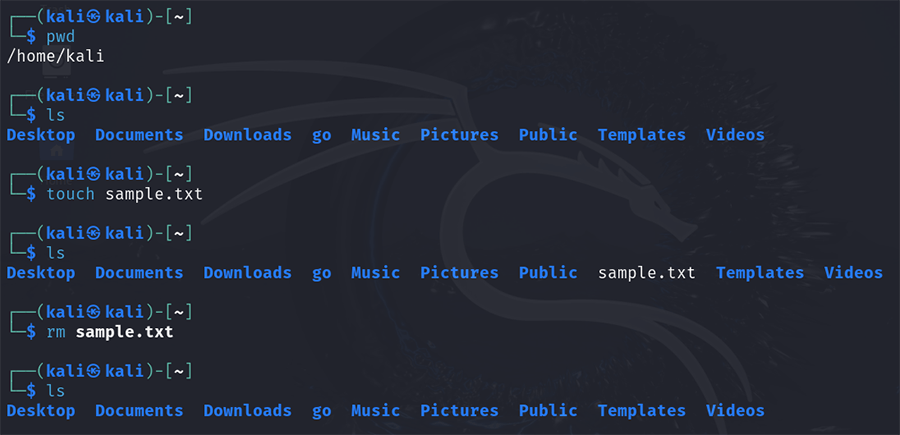
rm X | Remove (delete) X permanently. |
rm -r Y | Recursively delete a directory Y and its contents |
rm -f X | Forcibly remove file |
rm -rf Y | Forcibly remove directory Y and its contents recursively |
rmdir Y | Remove a directory Y permanently, provided Y is empty. |
open X | Open X in its default program. |
open -e X | Opens X in the default text editor (macOS: TextEdit) |
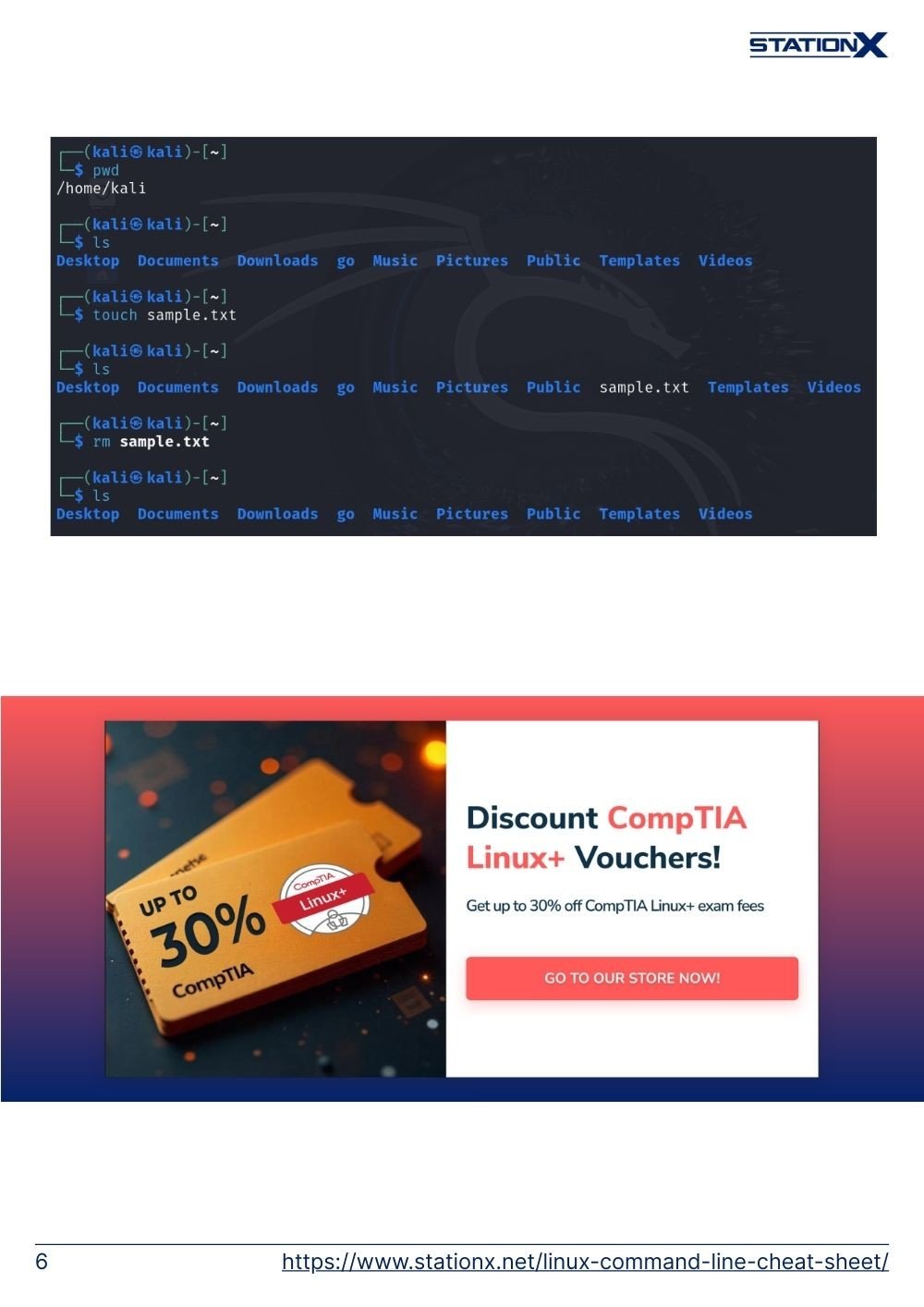
touch X | Create an empty file X or update the access and modification times of X. |
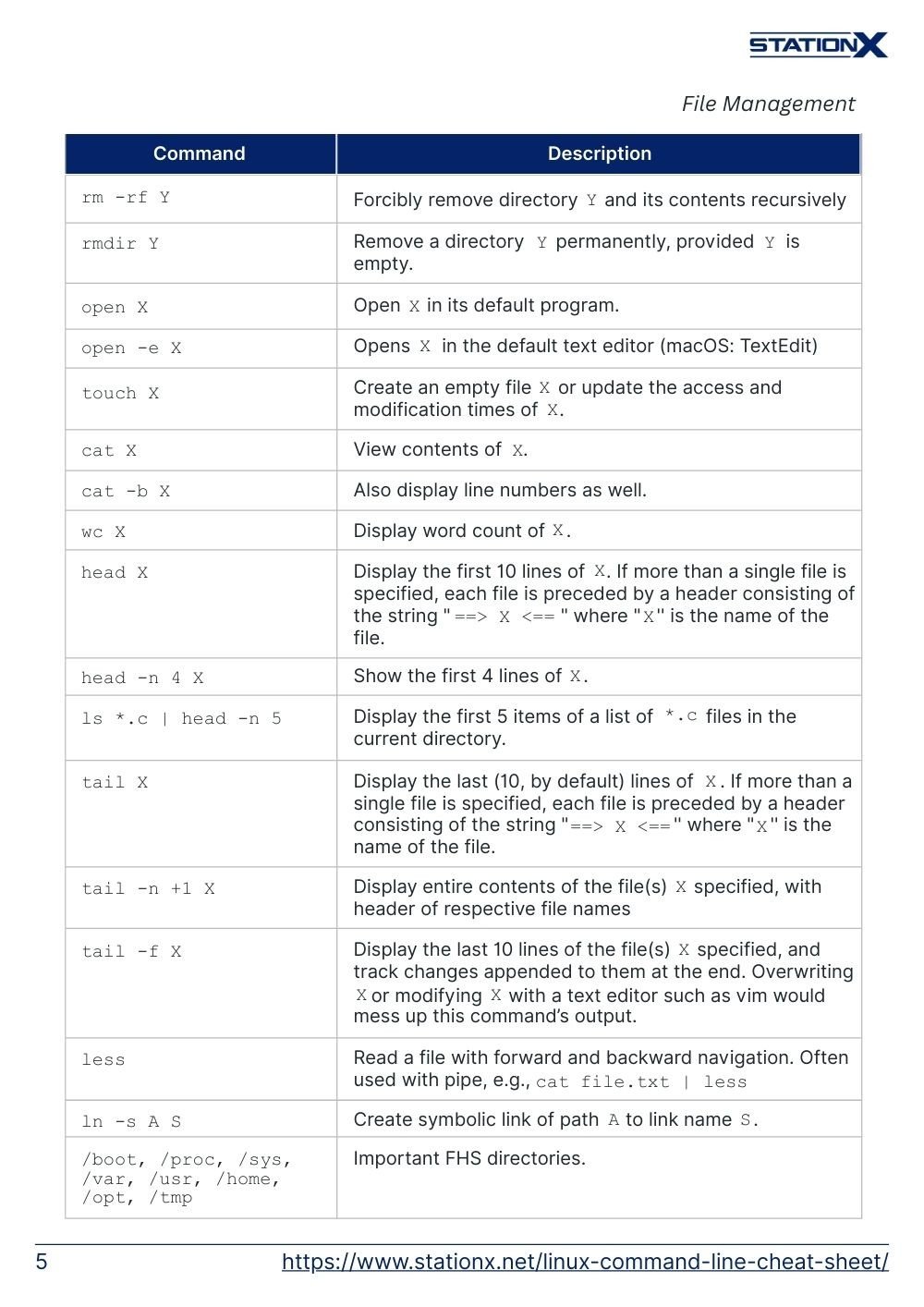
cat X | View contents of X. |
cat -b X | Also display line numbers as well. |
wc X | Display word count of X. |
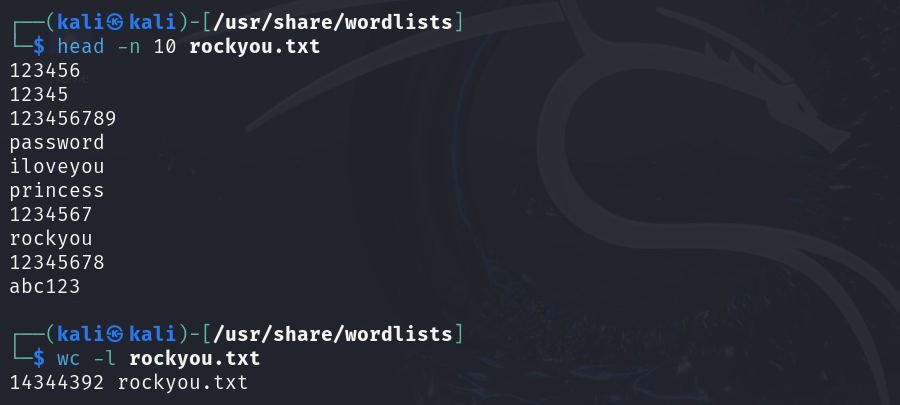
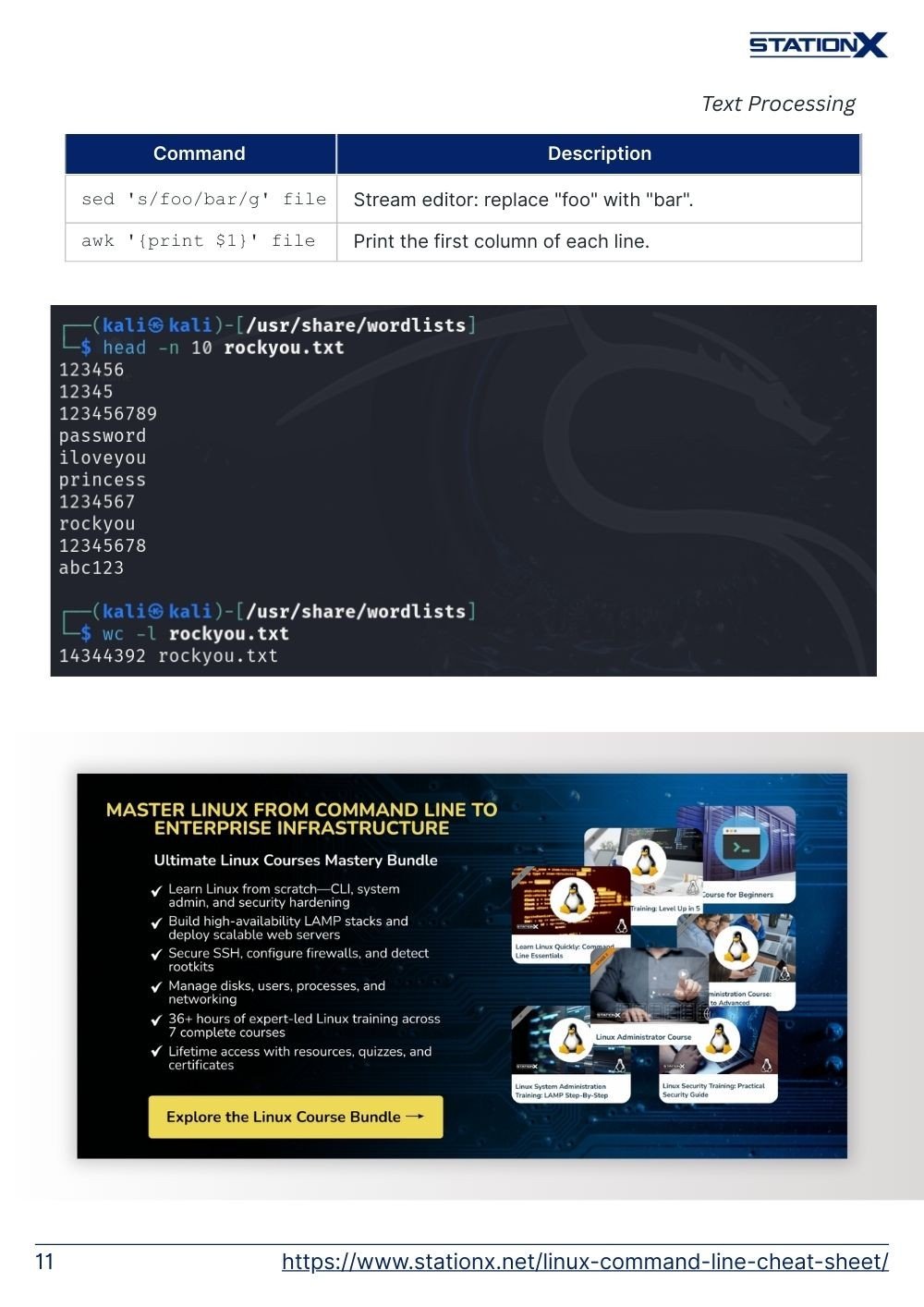
head X | Display the first 10 lines of X. If more than a single file is specified, each file is preceded by a header consisting of the string "==> X <=='' where "X'' is the name of the file. |
head -n 4 X | Show the first 4 lines of X. |
ls *.c | head -n 5 | Display the first 5 items of a list of *.c files in the current directory. |
tail X | Display the last (10, by default) lines of X. If more than a single file is specified, each file is preceded by a header consisting of the string "==> X <=='' where "X'' is the name of the file. |
tail -n +1 X | Display entire contents of the file(s) X specified, with header of respective file names |
tail -f X | Display the last 10 lines of the file(s) X specified, and track changes appended to them at the end. Overwriting X or modifying X with a text editor such as vim would mess up this command’s output. |
less | Read a file with forward and backward navigation. Often used with pipe, e.g., cat file.txt | less |
ln -s A S | Create symbolic link of path A to link name S. |
/boot, /proc, /sys, /var, /usr, /home, /opt, /tmp | Important FHS directories. |
Printing
Linux supports printing through various commands to send files to printers, check queues, and manage print jobs.
| Command | Description |
lp file | Print a file using the default printer. |
lpr file | Print a file (alternative command). |
lpq | Show print queue status. |
lprm job-id | Remove a job from the print queue. |
Input/Output Redirection
These are helpful for logging program output and error messages, and are essential topics in CompTIA Linux+ and LPIC-1.
| Command | Description |
|---|---|
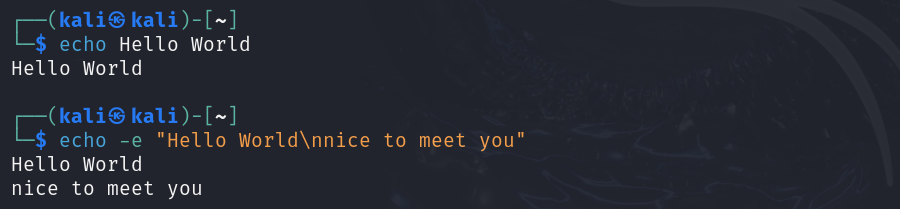
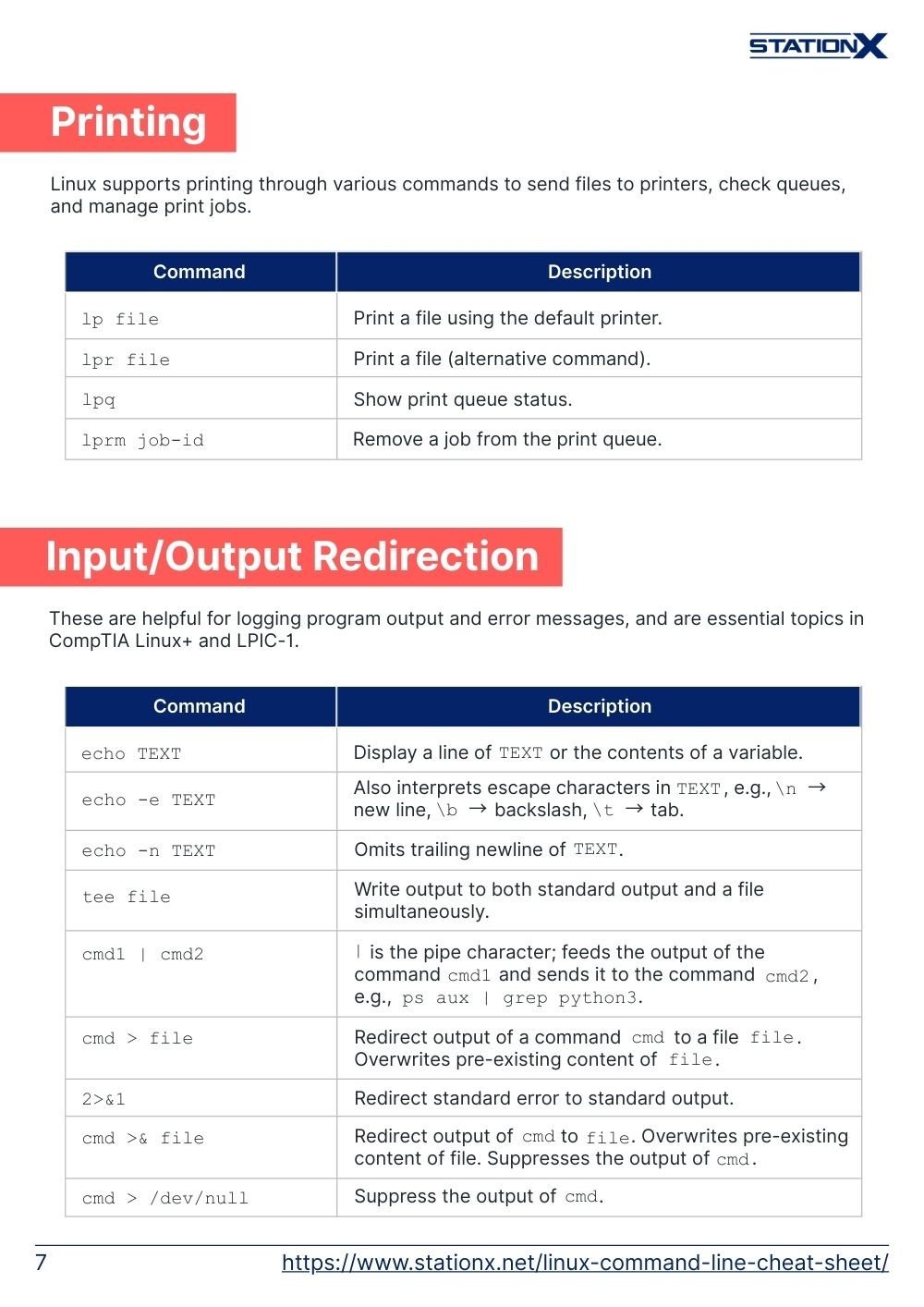
echo TEXT | Display a line of TEXT or the contents of a variable. |
echo -e TEXT | Also interprets escape characters in TEXT, e.g., \n → new line, \b → backslash, \t → tab. |
echo -n TEXT | Omits trailing newline of TEXT. |
tee file | Write output to both standard output and a file simultaneously. |
cmd1 | cmd2 | | is the pipe character; feeds the output of the command cmd1 and sends it to the command cmd2, e.g., ps aux | grep python3. |
cmd > file | Redirect output of a command cmd to a file file. Overwrites pre-existing content of file. |
2>&1 | Redirect standard error to standard output. |
cmd >& file | Redirect output of cmd to file. Overwrites pre-existing content of file. Suppresses the output of cmd. |
cmd > /dev/null | Suppress the output of cmd. |
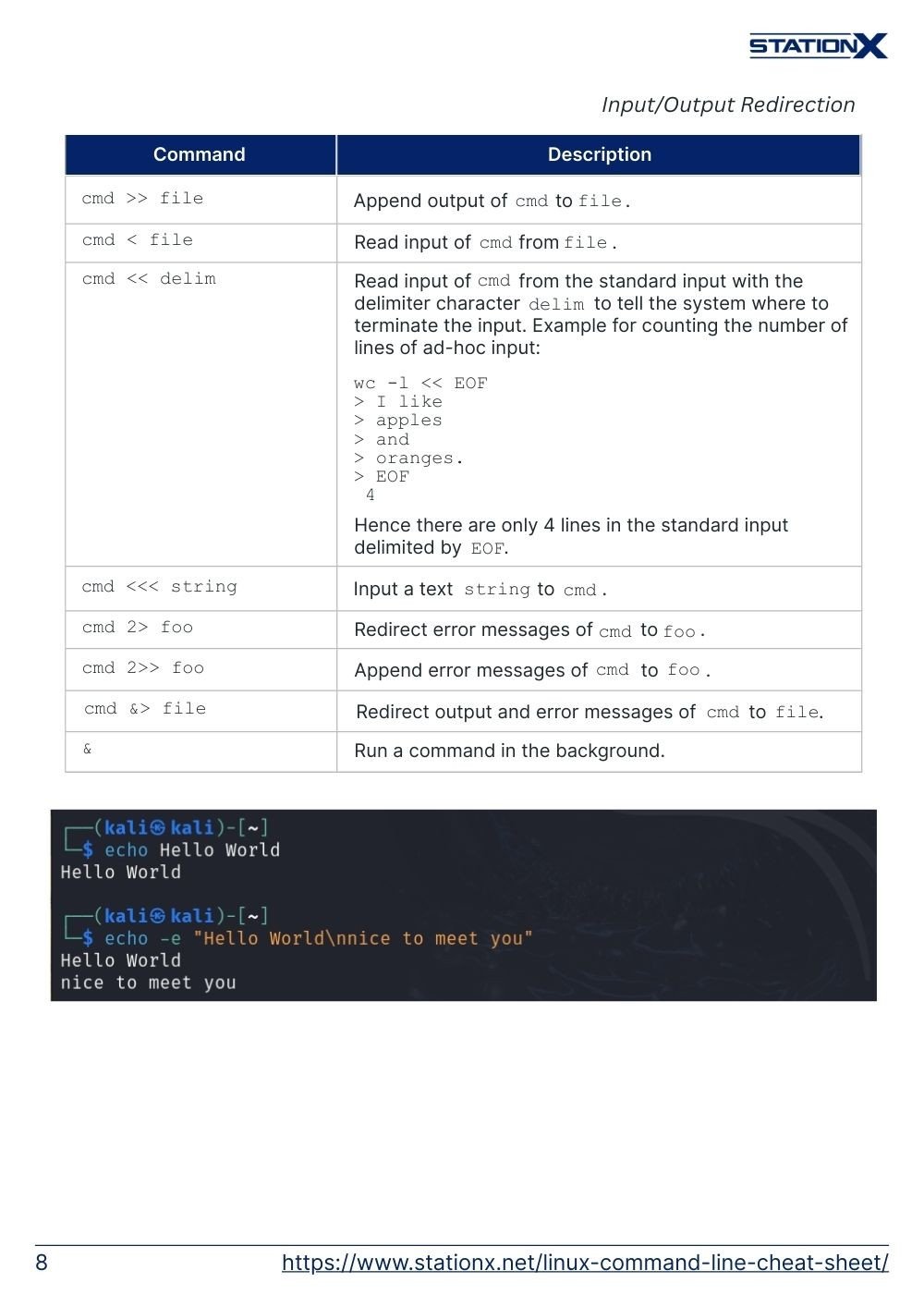
cmd >> file | Append output of cmd to file. |
cmd < file | Read input of cmd from file. |
cmd << delim | Read input of cmd from the standard input with the delimiter character delim to tell the system where to terminate the input. Example for counting the number of lines of ad-hoc input:wc -l << EOF> I like 4Hence there are only 4 lines in the standard input delimited by EOF. |
cmd <<< string | Input a text string to cmd. |
cmd 2> foo | Redirect error messages of cmd to foo. |
cmd 2>> foo | Append error messages of cmd to foo. |
cmd &> file | Redirect output and error messages of cmd to file. |
& | Run a command in the background. |
Search and Filter
These commands help you find the files you want.
| Command | Description |
|---|---|
grep patt /path/to/src | Search for a text pattern patt in X. Commonly used with pipe e.g., ps aux | grep python3 filters out the processes containing python3 from all running processes of all users. |
grep -r patt /path/to/src | Search recursively (the target directory /path/to/src and its subdirectories) for a text pattern patt. |
grep -v patt X | Return lines in X not matching the specified patt. |
grep -l patt X | Write to standard output the names of files containing patt. |
grep -i patt X | Perform case-insensitive matching on X. Ignore the case of patt. |
grep -A n / grep -B n / grep -C n | Show lines After, Before, or Context around a match. |
grep -E | Use extended regular expressions for more complex searches. |
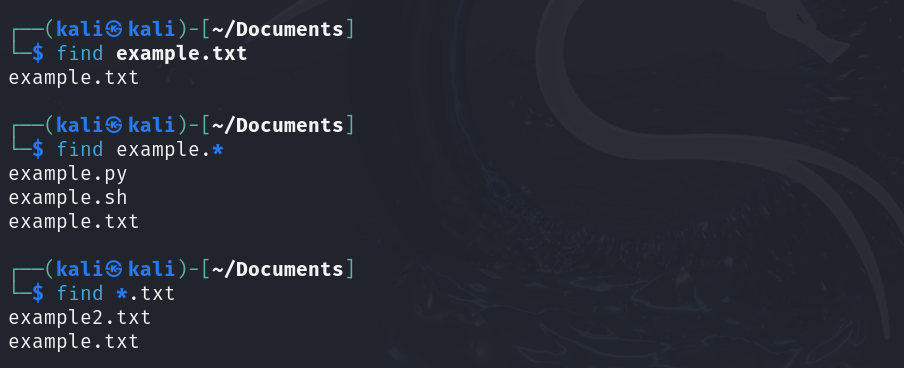
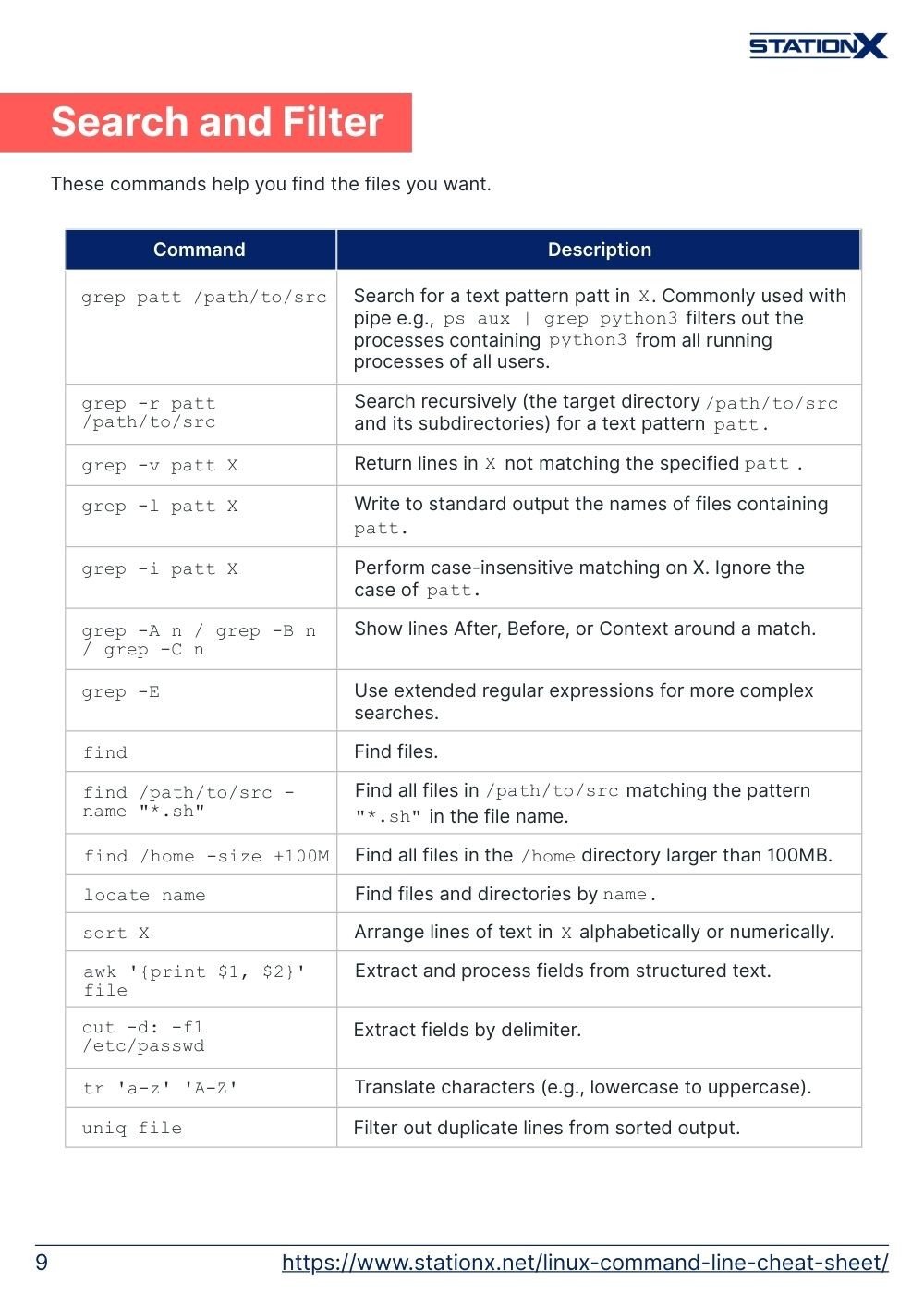
find | Find files. |
find /path/to/src -name "*.sh" | Find all files in /path/to/src matching the pattern "*.sh" in the file name. |
find /home -size +100M | Find all files in the /home directory larger than 100MB. |
locate name | Find files and directories by name. |
sort X | Arrange lines of text in X alphabetically or numerically. |
awk '{print $1, $2}' file | Extract and process fields from structured text. |
cut -d: -f1 /etc/passwd | Extract fields by delimiter. |
tr 'a-z' 'A-Z' | Translate characters (e.g., lowercase to uppercase). |
uniq file | Filter out duplicate lines from sorted output. |
Text Processing
Working with text files is a core part of Linux administration. These commands let you view, edit, sort, search, and transform text efficiently.
| Command | Description |
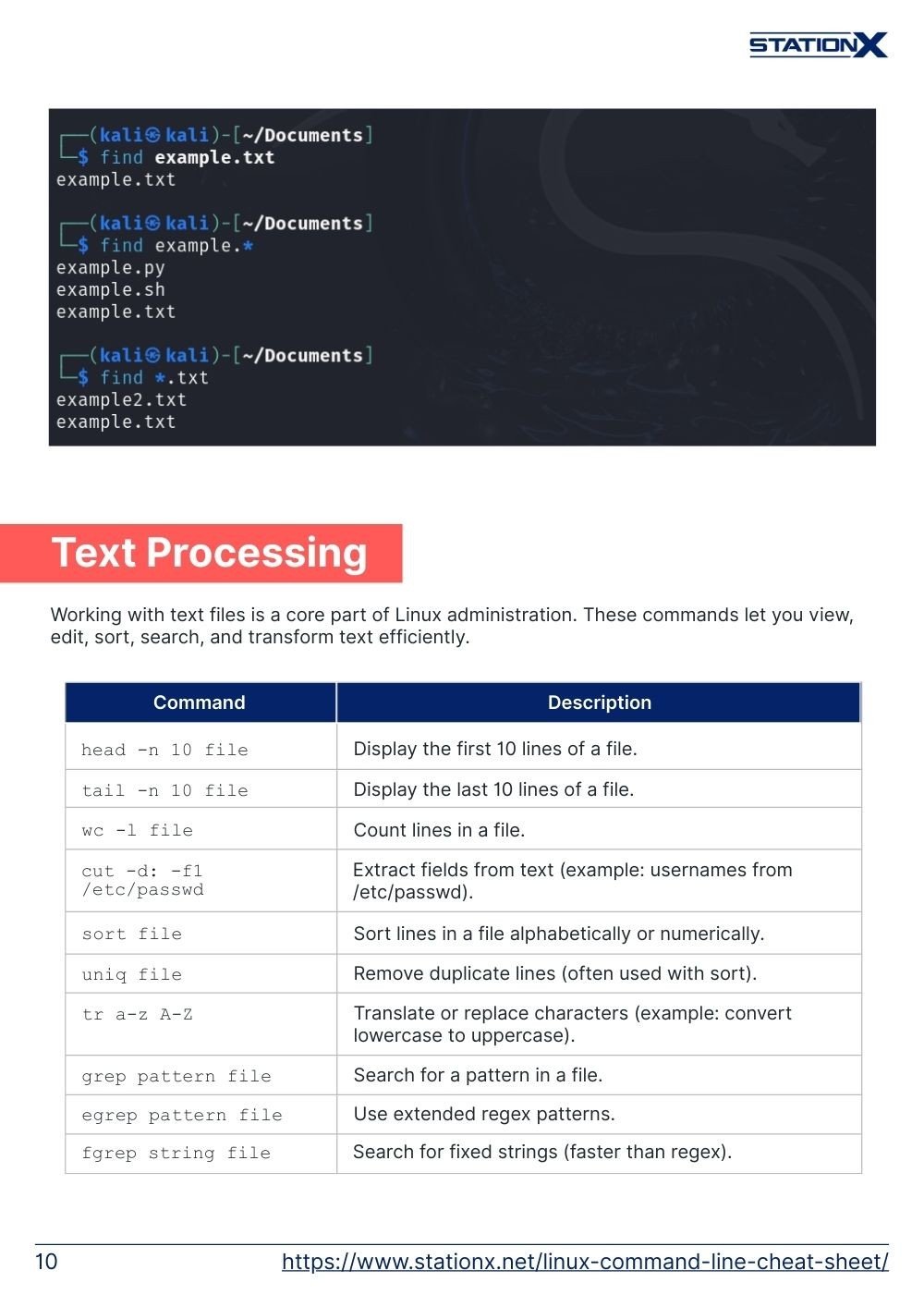
head -n 10 file | Display the first 10 lines of a file. |
tail -n 10 file | Display the last 10 lines of a file. |
wc -l file | Count lines in a file. |
cut -d: -f1 /etc/passwd | Extract fields from text (example: usernames from /etc/passwd). |
sort file | Sort lines in a file alphabetically or numerically. |
uniq file | Remove duplicate lines (often used with sort). |
tr a-z A-Z | Translate or replace characters (example: convert lowercase to uppercase). |
grep pattern file | Search for a pattern in a file. |
egrep pattern file | Use extended regex patterns. |
fgrep string file | Search for fixed strings (faster than regex). |
sed 's/foo/bar/g' file | Stream editor: replace "foo" with "bar". |
awk '{print $1}' file | Print the first column of each line. |
Archives
These commands are for unpacking compressed files (.zip, .gz, .bz2, .tar, etc.) with large or complex contents, such as programs. TAR commands, in particular, can be tricky to remember.
| Command | Description |
|---|---|
tar | Manipulate archives with .tar extension. |
tar -v | Get verbose output while manipulating TAR archives. May combine this option with others, e.g., tar -tvf. |
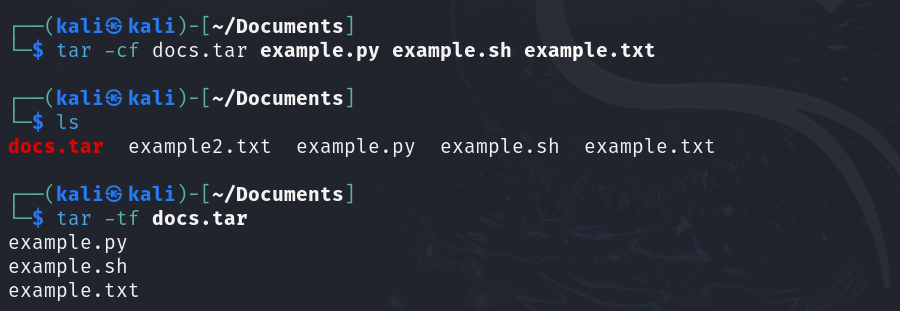
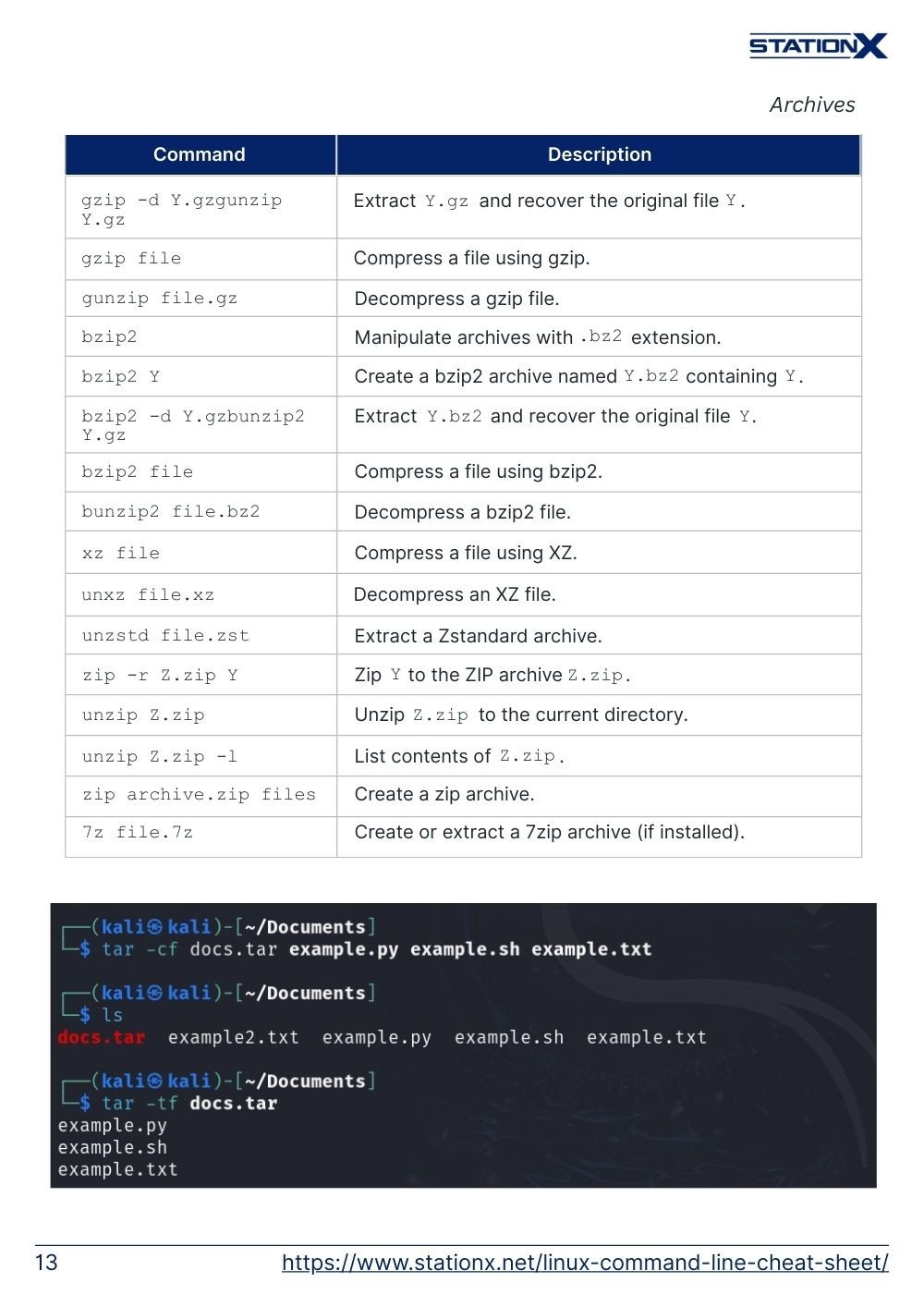
tar -cf archive.tar Y | Create a TAR archive named archive.tar containing Y. |
tar -xf archive.tar | Extract the TAR archive named archive.tar. |
tar -tf archive.tar | List contents of the TAR archive named archive.tar. |
tar -czf archive.tar.gz Y | Create a gzip-compressed TAR archive named archive.tar.gz containing Y. |
tar -xzf archive.tar.gz | Extract the gzip-compressed TAR archive named archive.tar.gz. |
tar -cjf archiave.tar.bz2 Y | Create a bzip2-compressed TAR archive named archive.tar.bz2 containing Y. |
tar -xjf archive.tar.bz2 | Extract the bzip2-compressed TAR archive named archive.tar.bz2. |
tar -cJf archive.tar.xz dir | Create an XZ-compressed tar archive. |
tar -xJf archive.tar.xz | Extract an XZ-compressed tar archive. |
tar --zstd -cf archive.tar.zst dir | Create a Zstandard-compressed tar archive |
tar --zstd -xf archive.tar.zst | Extract a Zstandard-compressed tar archive. |
tar --exclude=pattern | Exclude files from an archive. |
gzip | Manipulate archives with .gz extension. |
gzip Y | Create a gzip archive named Y.gz containing Y. |
gzip -l Y.gz | List contents of gzip archive Y.gz. |
gzip -d Y.gzgunzip Y.gz | Extract Y.gz and recover the original file Y. |
gzip file | Compress a file using gzip. |
gunzip file.gz | Decompress a gzip file. |
bzip2 | Manipulate archives with .bz2 extension. |
bzip2 Y | Create a bzip2 archive named Y.bz2 containing Y. |
bzip2 -d Y.gzbunzip2 Y.gz | Extract Y.bz2 and recover the original file Y. |
bzip2 file | Compress a file using bzip2. |
bunzip2 file.bz2 | Decompress a bzip2 file. |
xz file | Compress a file using XZ. |
unxz file.xz | Decompress an XZ file. |
zstd file | Compress a file using Zstandard. |
unzstd file.zst | Extract a Zstandard archive. |
zip -r Z.zip Y | Zip Y to the ZIP archive Z.zip. |
unzip Z.zip | Unzip Z.zip to the current directory. |
unzip Z.zip | List contents of Z.zip. |
zip archive.zip files | Create a zip archive. |
7z file.7z | Create or extract a 7zip archive (if installed). |
File Transfer
These commands are for logging in to local and remote hosts, and for uploading and downloading files, transferring them between devices. Remember to omit the square brackets "[" and "]" when you input the optional parameters they enclose.
| Command | Description |
|---|---|
ssh user@access | Connect to access as user. |
ssh access | Connect to access as your local username. |
ssh -p port user@access | Connect to access as user using port. |
ssh-copy-id user@host | Copy public key to a server for passwordless SSH login. |
ssh -L local:remote:port user@host | Create a local port forwarding tunnel over SSH. |
ssh -D port user@host | Create a dynamic SOCKS proxy over SSH. |
scp [user1@]host1:[path1] [user2@]host2:[path2] | Login to hostN as userN via secure copy protocol for N=1,2.Example usage: scp alice@pi:/home/source bob@arduino:/destinationpath1 and path2 may be local or remote, but ensure they’re absolute rather than relative paths, e.g., /var/www/*.html, /usr/bin.If user1 and user2 are not specified, scp will use your local username. |
scp -P port [user1@]host1:[path1] [user2@]host2:[path2] | Connect to hostN as userN using port for N=1,2. |
scp -r [user1@]host1:[path1] [user2@]host2:[path2] | Recursively copy all files and directories from path1 to path2. |
scp -C file user@host:/path | Copy files over SSH with compression. |
sftp [user@]access | Login to access as user via secure file transfer protocol. If user is not specified, your local username will be used. |
sftp access | Connect to access as your local username. |
sftp -P port user@access | Connect to access as user using port. |
rsync -a [path1] [path2] | Synchronize [path1] to [path2], preserving symbolic links, attributes, permissions, ownerships, and other settings. |
rsync -avz host1:[path1] [path2] | Synchronize [path1] on the remote host host1 to the local path [path2], preserving symbolic links, attributes, permissions, ownerships, and other settings. It also compresses the data involved during the transfer. |
rsync --delete src dst | Remove extraneous files in the destination to mirror source. |
rsync --progress src dst | Show transfer progress during sync. |
wget url | Download a file from the web. |
curl ‑O url | Download a file keeping original filename. |
curl ‑L url | Follow redirects when downloading. |
File Permissions
Not all files are equally accessible. To prevent unwanted tampering, some files on your device may be read-only. For more information about file permissions on Linux, refer to our Linux File Permissions Cheat Sheet.
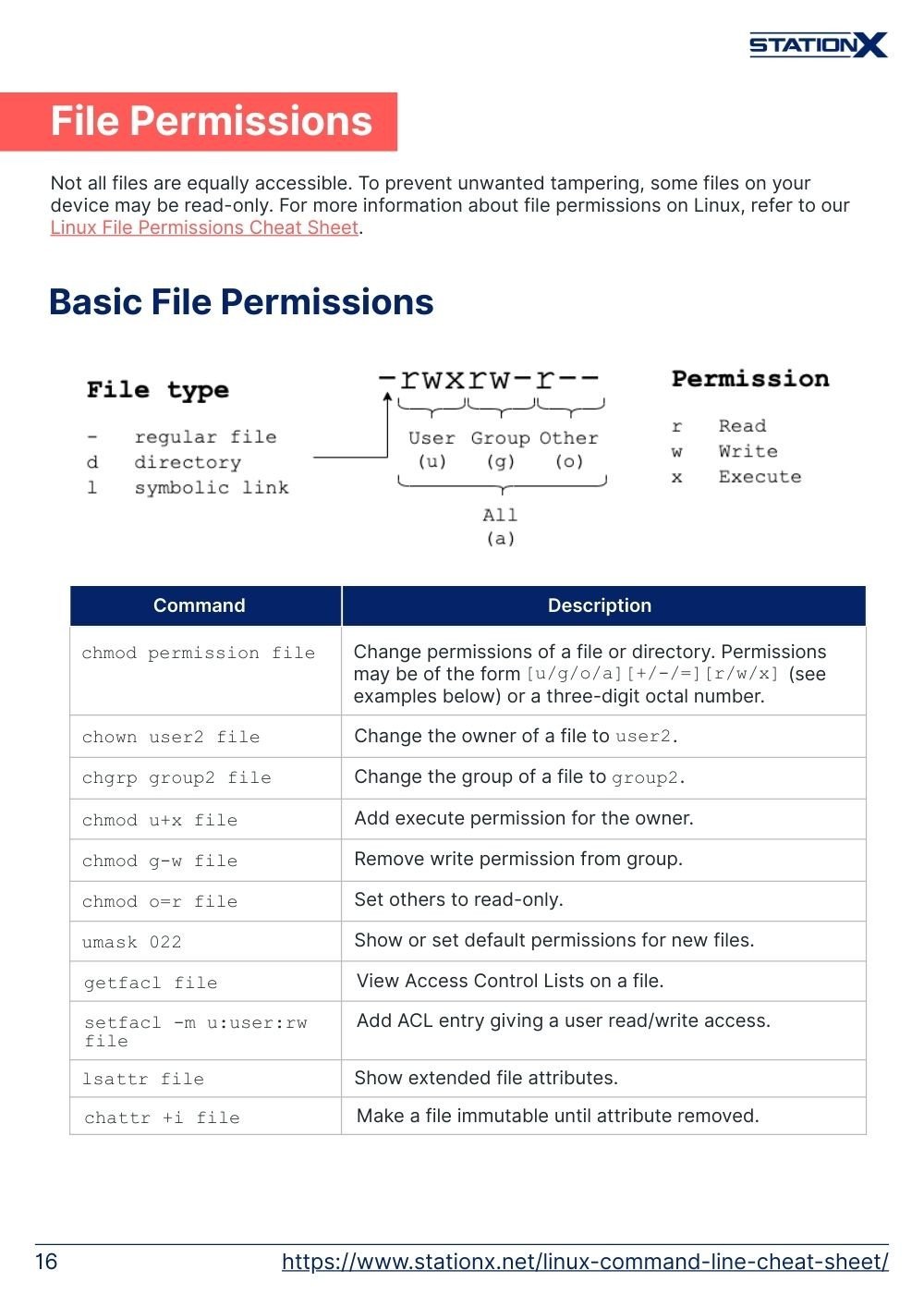
Basic File Permissions

| Command | Description |
|---|---|
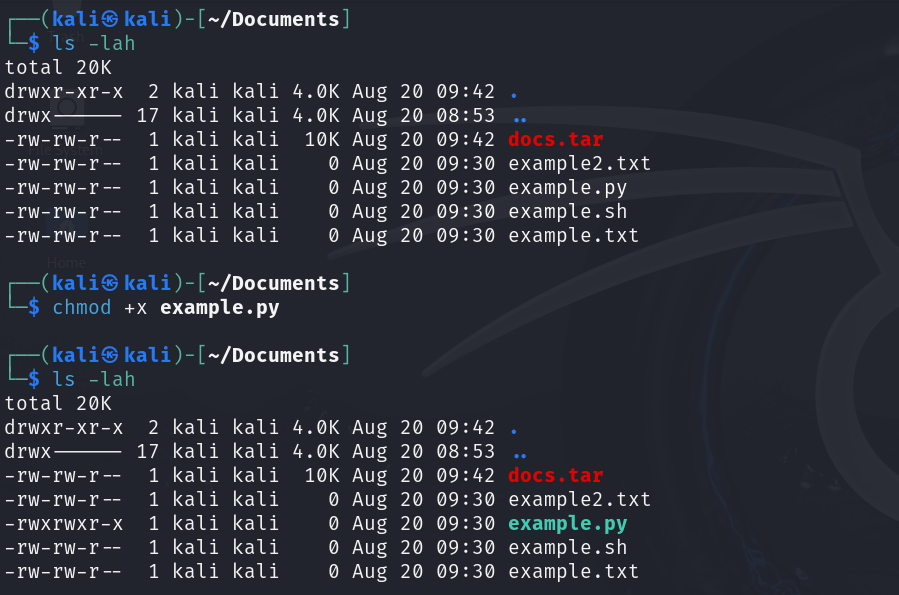
chmod permission file | Change permissions of a file or directory. Permissions may be of the form [u/g/o/a][+/-/=][r/w/x] (see examples below) or a three-digit octal number. |
chown user2 file | Change the owner of a file to user2. |
chgrp group2 file | Change the group of a file to group2. |
chmod u+x file | Add execute permission for the owner. |
chmod g-w file | Remove write permission from group. |
chmod o=r file | Set others to read-only. |
umask 022 | Show or set default permissions for new files. |
getfacl file | View Access Control Lists on a file. |
setfacl -m u:user:rw file | Add ACL entry giving a user read/write access. |
lsattr file | Show extended file attributes. |
chattr +i file | Make a file immutable until attribute removed. |
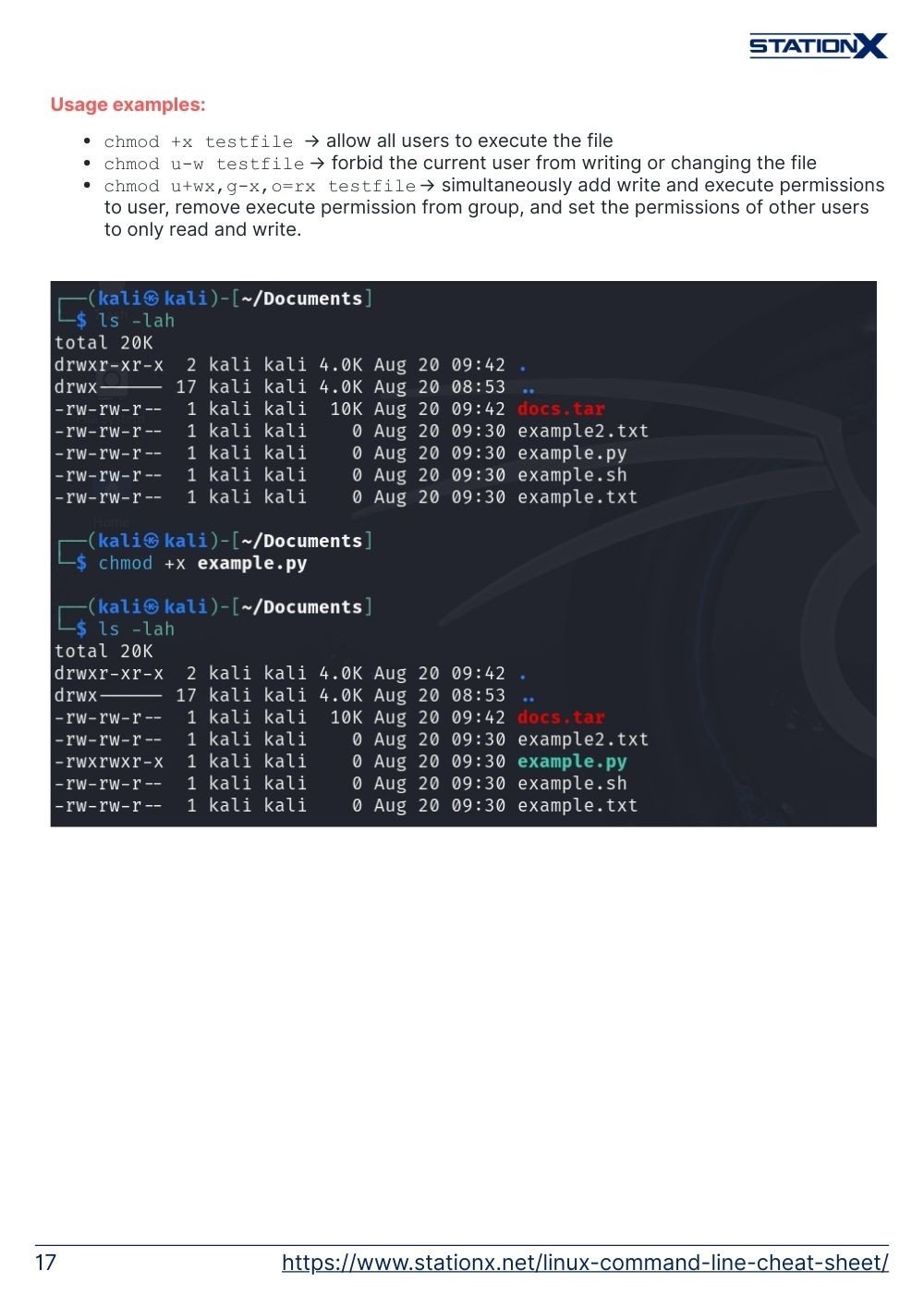
Usage examples:
chmod +x testfile→ allow all users to execute the filechmod u-w testfile→ forbid the current user from writing or changing the filechmod u+wx,g-x,o=rx testfile→ simultaneously add write and execute permissions to user, remove execute permission from group, and set the permissions of other users to only read and write.
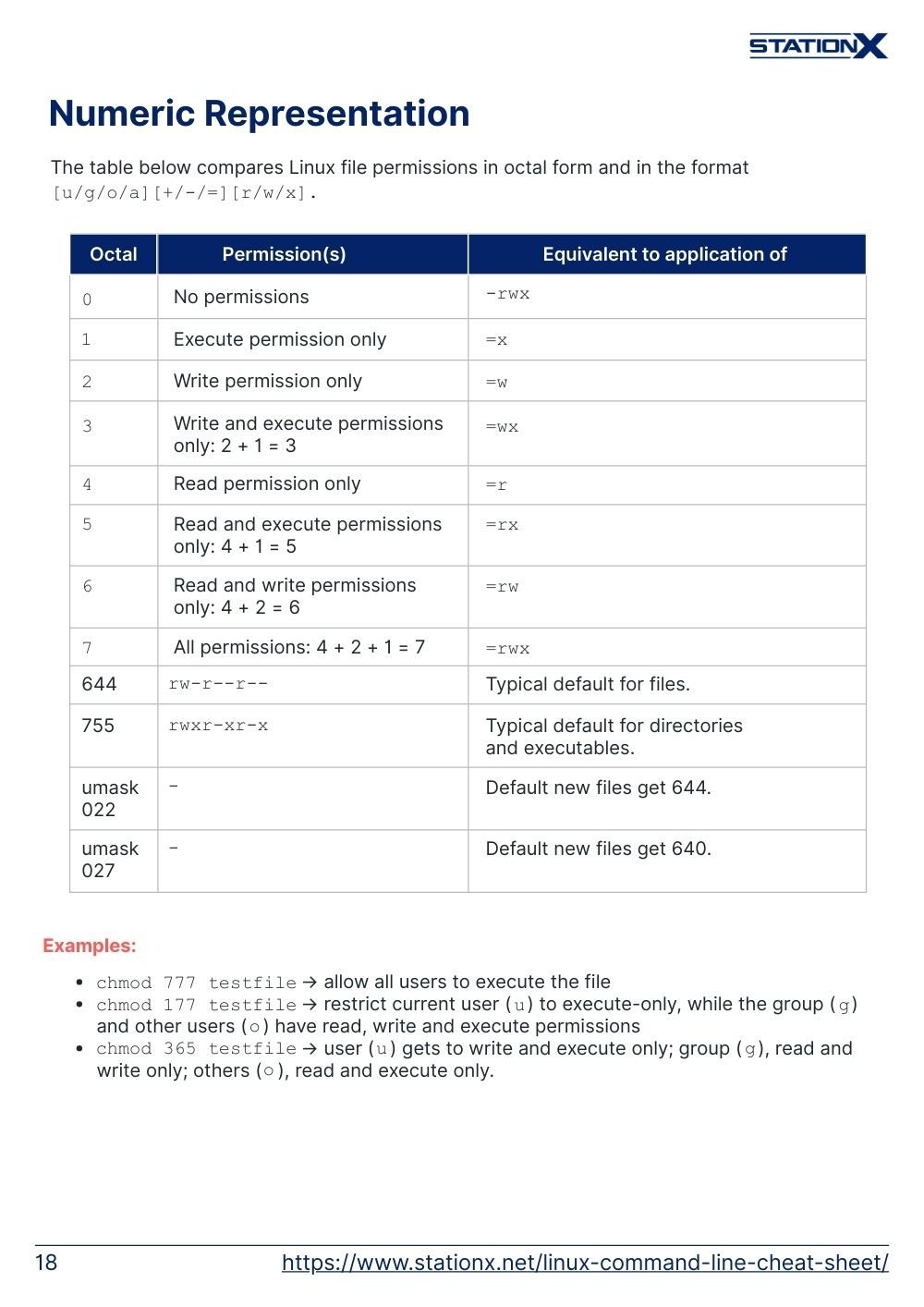
Numeric Representation
The table below compares Linux file permissions in octal form and in the format [u/g/o/a][+/-/=][r/w/x].
| Octal | Permission(s) | Equivalent to application of |
|---|---|---|
0 | No permissions | -rwx |
1 | Execute permission only | =x |
2 | Write permission only | =w |
3 | Write and execute permissions only: 2 + 1 = 3 | =wx |
4 | Read permission only | =r |
5 | Read and execute permissions only: 4 + 1 = 5 | =rx |
6 | Read and write permissions only: 4 + 2 = 6 | =rw |
7 | All permissions: 4 + 2 + 1 = 7 | =rwx |
| 644 | rw-r--r-- | Typical default for files. |
| 755 | rwxr-xr-x | Typical default for directories and executables. |
| umask 022 | - | Default new files get 644. |
| umask 027 | - | Default new files get 640. |
Examples
chmod 777 testfile→ allow all users to execute the filechmod 177 testfile→ restrict current user (u) to execute-only, while the group (g) and other users (o) have read, write and execute permissionschmod 365 testfile→ user (u) gets to write and execute only; group (g), read and write only; others (o), read and execute only.
Information Security Courses Bundles
Want lifetime access to expert-led cyber security training? Explore our Information Security Course Bundles — one-time purchase packages covering top topics like Ethical Hacking, Cloud, Linux, DevSecOps, and CompTIA certifications.
Special Permission Bits
SUID (Set User ID): When set on an executable file, the program runs with the permissions of the file’s owner instead of the user running it. Example: /usr/bin/passwd.
- Appears on the user/owner execute bit.
- s = SUID + execute
- S = SUID without execute
- Example: -rwsr-xr-x → SUID set, owner can execute.
Example: -rwSr-xr-x → SUID set, owner cannot execute.
SGID (Set Group ID): On executables, runs with the group’s permissions. On directories, new files inherit the group of the directory instead of the creating user’s group.
- Appears on the group execute bit.
- s = SGID + execute
- S = SGID without execute
- Example: -rwxr-sr-x → SGID set, group can execute.
- Example: -rwxr-Sr-x → SGID set, group cannot execute.
Sticky Bit: On directories (like /tmp), users can only delete or rename their own files, even if others have write access to the directory.
- Appears on the others execute bit.
- t = sticky + execute
- T = sticky without execute
- Example: drwxrwxrwt → world-writable directory with sticky bit (like /tmp).
- Example: drwxrwxrwT → sticky set, others cannot execute.
Octal permissions are 4 digits:
[special][user][group][others]
Special digit (first one):
- 4 = SUID
- 2 = SGID
- 1 = Sticky
- Add them together if you want more than one (e.g., 6 = SUID + SGID, 7 = SUID + SGID + Sticky)
| Octal | Special Bit | Placement | With Execute | Without Execute |
4xxx | SUID | User Execute | rwsr-xr-x | -rwSr-xr-x |
2xxx | SGID | Group Execute | rwxr-sr-x | rwxr-Sr-x |
1xxx | Sticky | Others Execute | drwxrwxrwt | drwxrwxrwT |
xxx = regular owner/group/others permission digits (e.g., 755, 644).
Other Links You Might Like:
System Information
These commands come in handy when you’re developing new applications for Linux or troubleshooting your Linux machine.
General
These provide information about your Linux machine and perform administrative tasks.
| Command | Description |
|---|---|
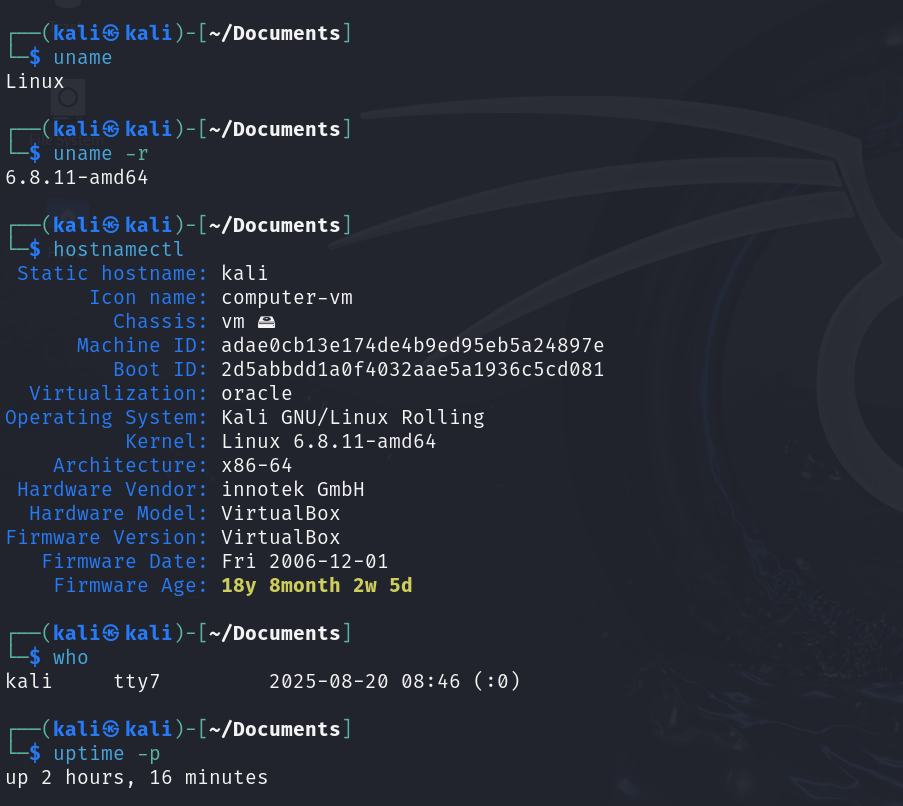
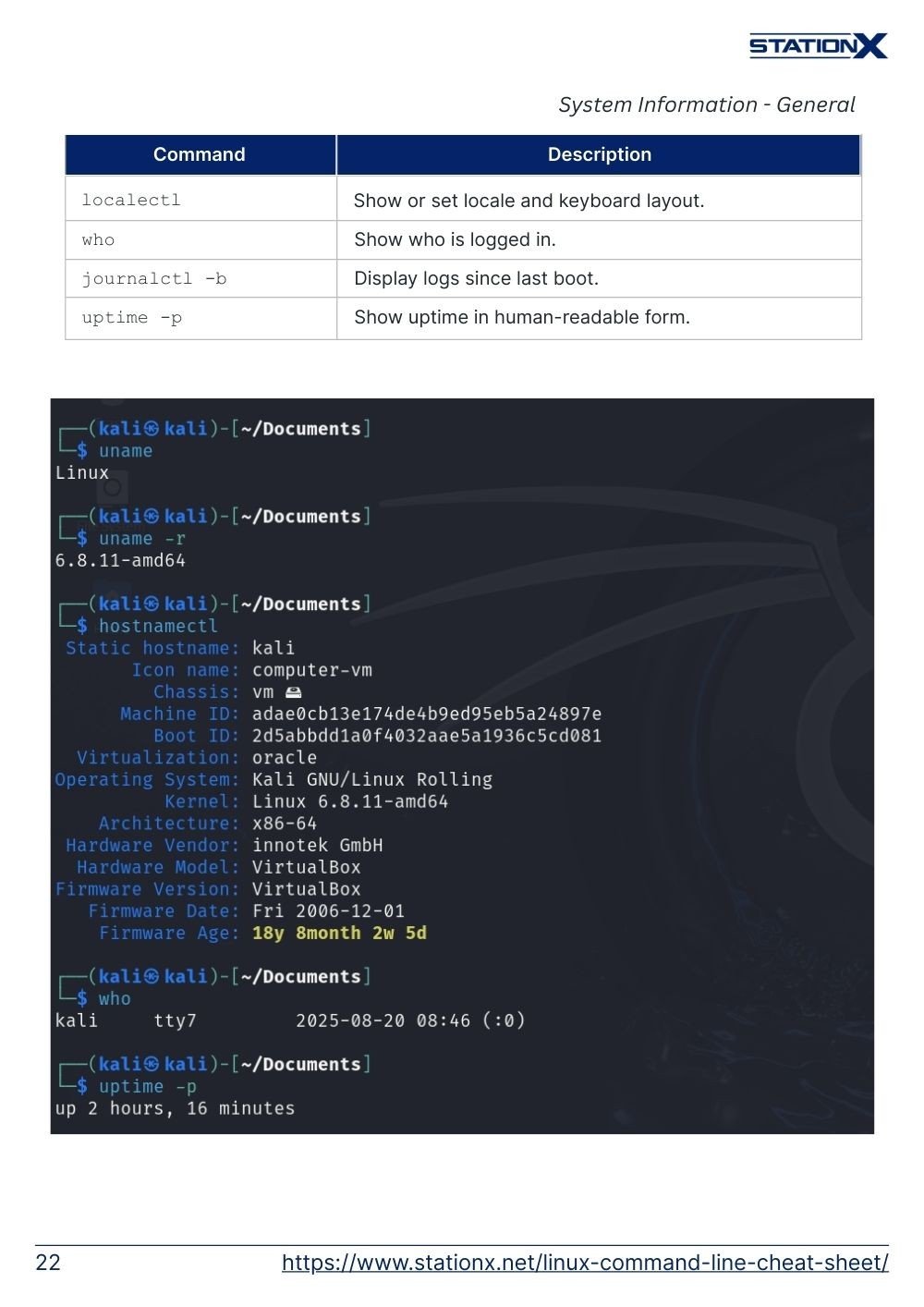
uname | Show the Linux system information. |
uname -a | Detailed Linux system information |
uname -r | Kernel release information, such as kernel version |
uptime | Show how long the system is running and load information. |
susudo | Superuser; use this before a command that requires root access e.g., su shutdown |
cal | Show calendar where the current date is highlighted. |
date | Show the current date and time of the machine. |
halt | Stop the system immediately. |
shutdown | Shut down the system. |
reboot | Restart the system. |
last reboot | Show reboot history. |
man COMMAND | Shows the manual for a given COMMAND. To exit the manual, press “q”. |
hostname | Show system host name |
hostname -I | Display IP address of host |
cat /etc/*-release | Show the version of the Linux distribution installed. For example, if you’re using Red Hat Linux, you may replace * with redhat. |
hostnamectl | Show or set the system hostname. |
timedatectl | Show or set system date, time, and NTP. |
localectl | Show or set locale and keyboard layout. |
who | Show who is logged in. |
journalctl -b | Display logs since last boot. |
uptime -p | Show uptime in human-readable form. |
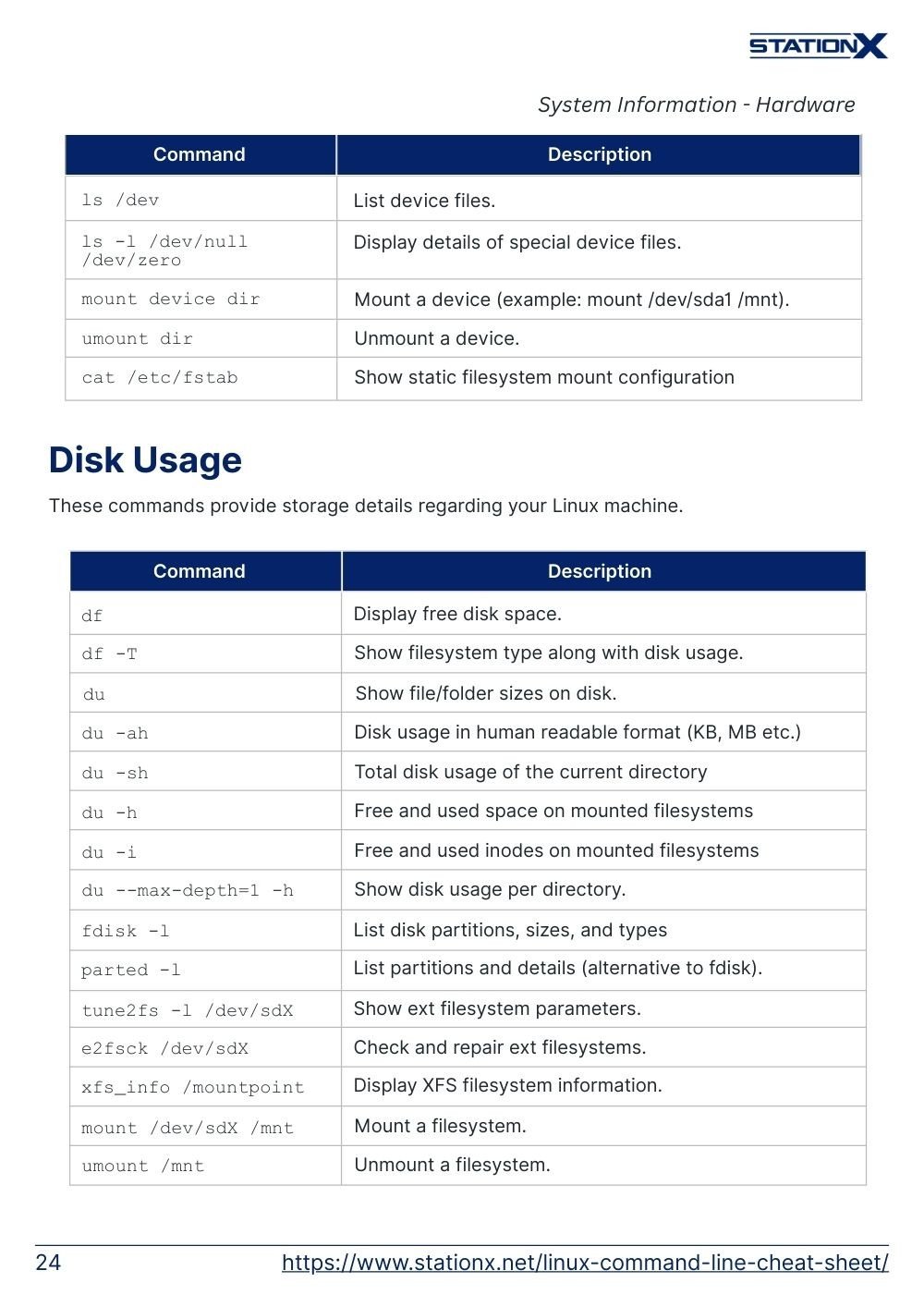
Hardware
These commands provide details about the hardware supporting your Linux machine.
| Command | Description |
|---|---|
dmesg | Display messages in kernel ring buffer (data structure that records messages related to the operation of the program running the operating system) |
cat /proc/cpuinfo | Display information about the central processing unit (CPU) |
cat /proc/meminfo | Display memory information |
lspci -tv | Displays information about each Peripheral Component Interconnect (PCI) device on your system. The option -t outputs the information as a tree diagram, and -v is for verbose output. |
lsusb -tv | Display information about Universal Serial Bus (USB) devices and the devices connected to them. The option -t outputs the information as a tree diagram, and -v is for verbose output. |
dmidecode | Display system hardware components, serial numbers, and BIOS version |
hdparm -i /dev/sda | Display information about the disk sda |
hdparm -tT /dev/sda | Perform a read speed test on the disk sda |
badblocks -s /dev/sda | Test for unreadable blocks on the disk sda |
lsblk | List block devices and mount points. |
blkid | Show UUIDs and filesystem types. |
lsscsi | Display SCSI/SATA/NVMe devices. |
lsmod | List loaded kernel modules. |
modinfo module | Show details about a kernel module. |
modprobe module | Load a kernel module. |
rmmod module | Remove a kernel module. |
sensors | Show temperature/voltage/fan readings. |
ls /dev | List device files. |
ls -l /dev/null /dev/zero | Display details of special device files. |
mount device dir | Mount a device (example: mount /dev/sda1 /mnt). |
umount dir | Unmount a device. |
cat /etc/fstab | Show static filesystem mount configuration |
Disk Usage
These commands provide storage details regarding your Linux machine.
| Command | Description |
|---|---|
df | Display free disk space. |
df -T | Show filesystem type along with disk usage. |
du | Show file/folder sizes on disk. |
du -ah | Disk usage in human readable format (KB, MB etc.) |
du -sh | Total disk usage of the current directory |
du -h | Free and used space on mounted filesystems |
du -i | Free and used inodes on mounted filesystems |
du --max-depth=1 -h | Show disk usage per directory. |
du --max-depth=1 -h | Show disk usage per directory. |
fdisk -l | List disk partitions, sizes, and types |
parted -l | List partitions and details (alternative to fdisk). |
tune2fs -l /dev/sdX | Show ext filesystem parameters. |
e2fsck /dev/sdX | Check and repair ext filesystems. |
xfs_info /mountpoint | Display XFS filesystem information. |
mount /dev/sdX /mnt | Mount a filesystem. |
umount /mnt | Unmount a filesystem. |
free -h | Display free and used memory in human readable units. |
free -m | Display free and used memory in MB. |
free -g | Display free and used memory in GB. |
swapoff / swapon | Disable or enable swap. |
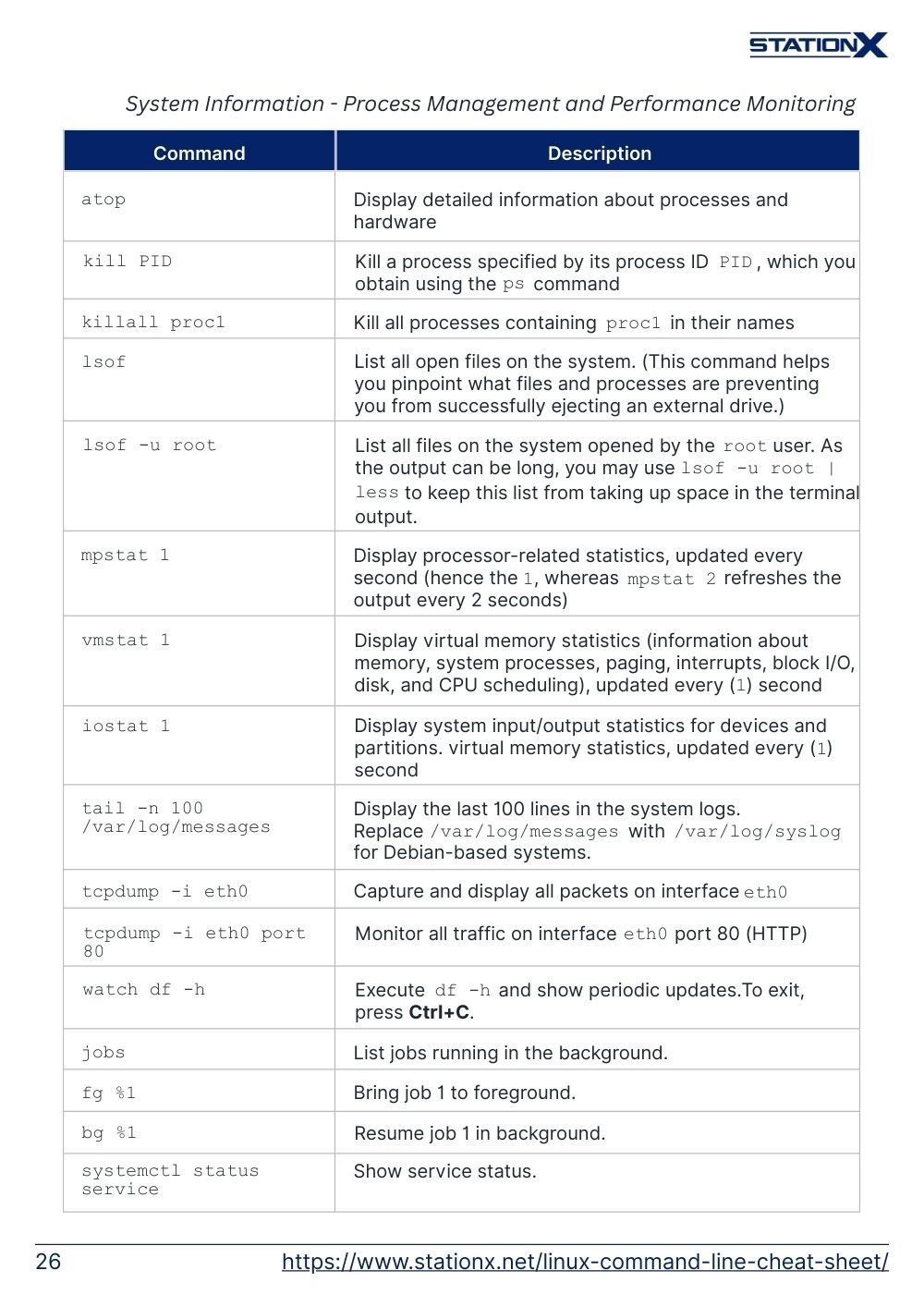
Process Management and Performance Monitoring
The following is reminiscent of functions in Windows Task Manager, but on the command line.
| Command | Description |
|---|---|
& | Add this character to the end of a command/process to run it in the background |
ps | Show process status. Often used with grep e.g., ps aux | grep python3 displays information on processes involving python3.Meaning of aux:a = show processes for all usersu = show user or owner column in outputx = show processes not attached to a terminal |
ps -eps -A | Either of these two commands prints all running processes in the system |
ps -ef | Print detailed overview |
ps -U root -u root | Display all processes running under the account root. |
ps -eo pid,user,command | Display only the columns pid, user and command in ps output |
top | Display sorted information about processes |
htop | Display sorted information about processes with visual highlights. It allows you to scroll vertically and horizontally, so you can see every process running on your system and entire commands. |
atop | Display detailed information about processes and hardware |
kill PID | Kill a process specified by its process ID PID, which you obtain using the ps command |
killall proc1 | Kill all processes containing proc1 in their names |
lsof | List all open files on the system. (This command helps you pinpoint what files and processes are preventing you from successfully ejecting an external drive.) |
lsof -u root | List all files on the system opened by the root user. As the output can be long, you may use lsof -u root | less to keep this list from taking up space in the terminal output. |
mpstat 1 | Display processor-related statistics, updated every second (hence the 1, whereas mpstat 2 refreshes the output every 2 seconds) |
vmstat 1 | Display virtual memory statistics (information about memory, system processes, paging, interrupts, block I/O, disk, and CPU scheduling), updated every (1) second |
iostat 1 | Display system input/output statistics for devices and partitions. virtual memory statistics, updated every (1) second |
tail -n 100 /var/log/messages | Display the last 100 lines in the system logs. Replace /var/log/messages with /var/log/syslog for Debian-based systems. |
tcpdump -i eth0 | Capture and display all packets on interface eth0 |
tcpdump -i eth0 port 80 | Monitor all traffic on interface eth0 port 80 (HTTP) |
watch df -h | Execute df -h and show periodic updates.To exit, press Ctrl+C. |
jobs | List jobs running in the background. |
fg %1 | Bring job 1 to foreground. |
bg %1 | Resume job 1 in background. |
systemctl status service | Show service status. |
systemctl start/stop/enable/disable service | Start, stop, enable, or disable a service. |
systemctl list-units --type=service | List active services. |
journalctl -xe | View recent logs with errors. |
journalctl -u service | View logs for a specific service. |
nice -n 10 cmd | Run a command with adjusted scheduling priority. |
renice -n -5 -p PID | Change priority of a running process. |
sar -u 1 | Display CPU usage statistics (if installed). |
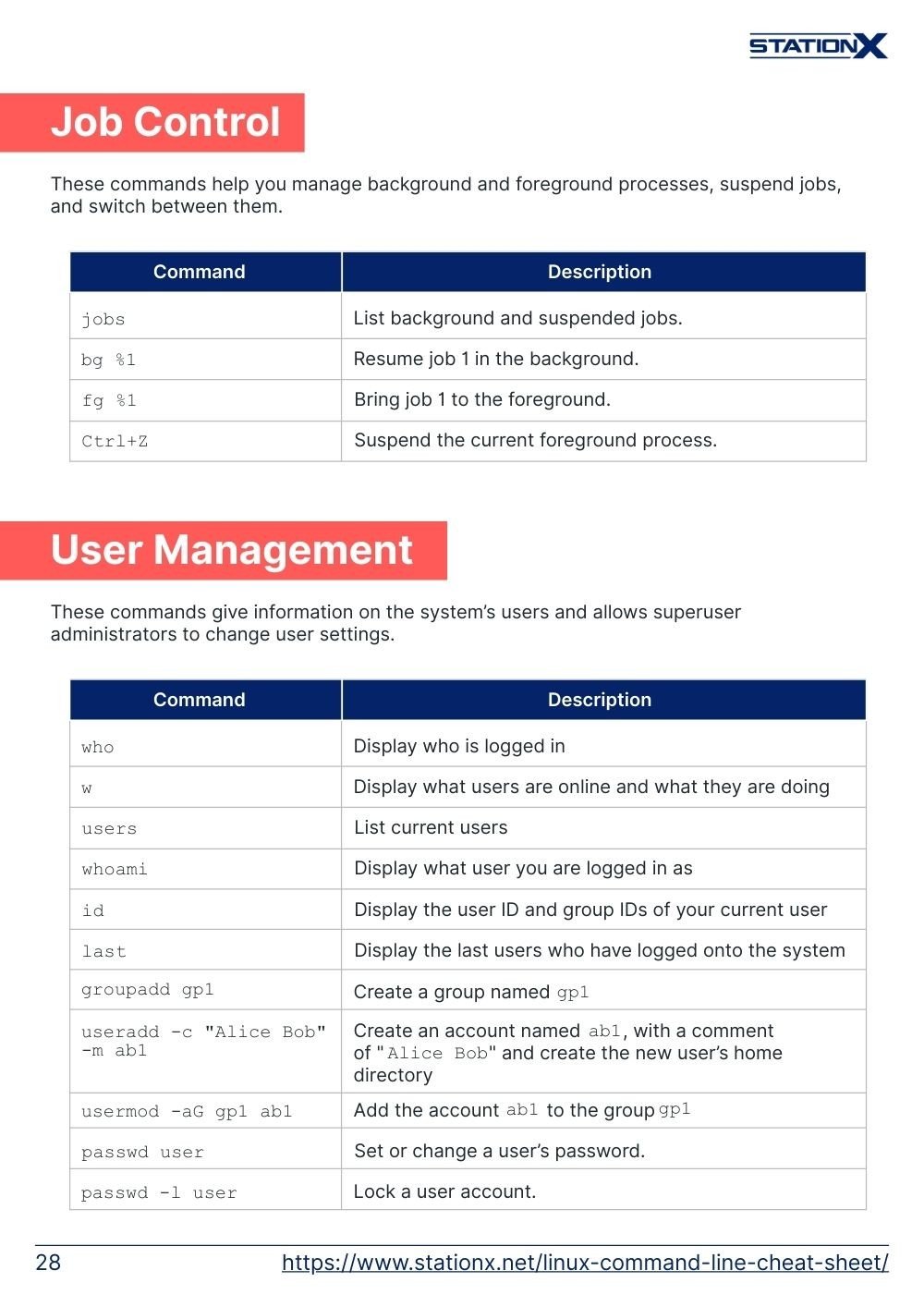
Job Control
These commands help you manage background and foreground processes, suspend jobs, and switch between them.
| Command | Description |
jobs | List background and suspended jobs. |
bg %1 | Resume job 1 in the background. |
fg %1 | Bring job 1 to the foreground. |
Ctrl+Z | Suspend the current foreground process. |
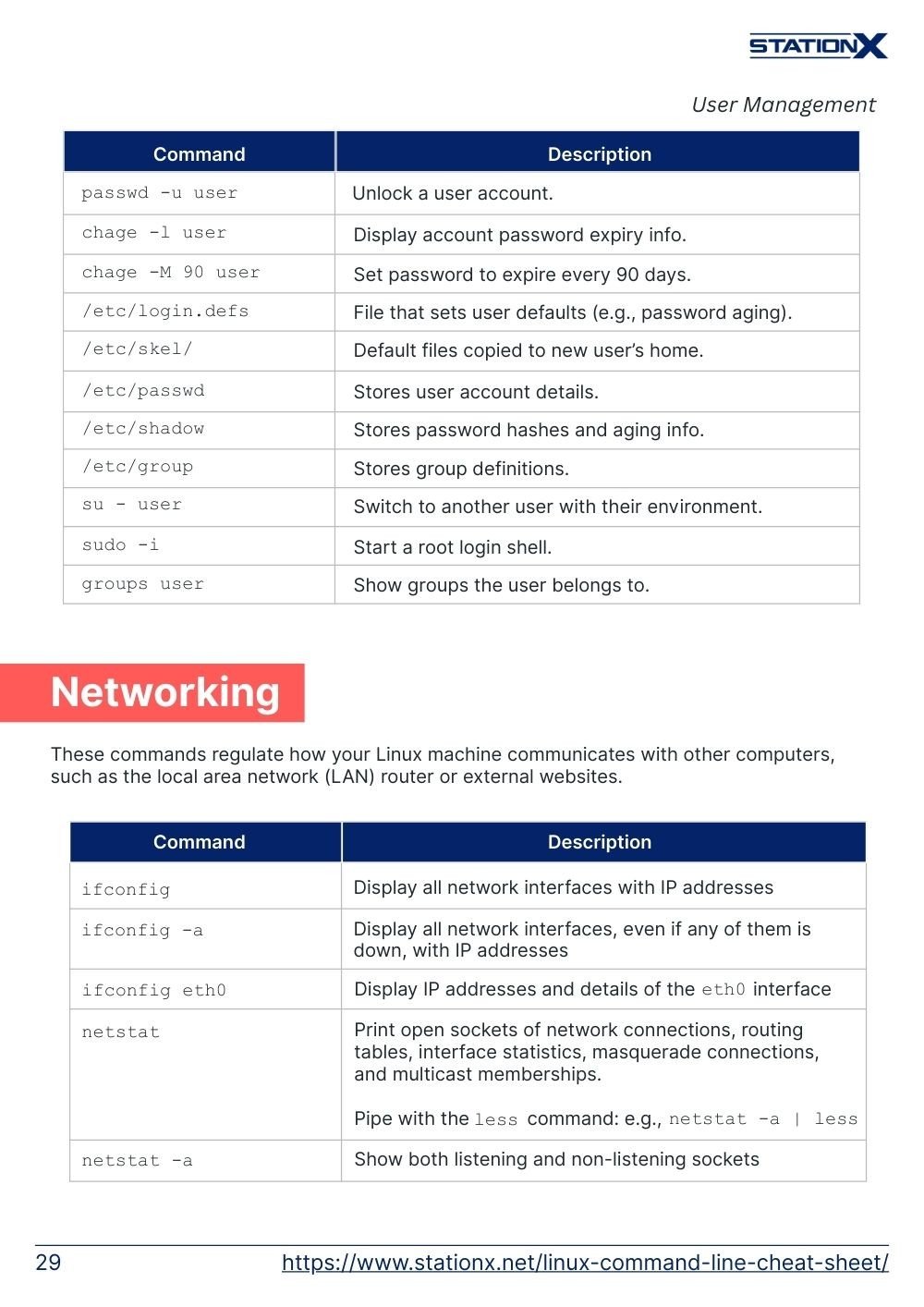
User Management
These commands give information on the system’s users and allows superuser administrators to change user settings.
| Command | Description |
|---|---|
who | Display who is logged in |
w | Display what users are online and what they are doing |
users | List current users |
whoami | Display what user you are logged in as |
id | Display the user ID and group IDs of your current user |
last | Display the last users who have logged onto the system |
groupadd gp1 | Create a group named gp1 |
useradd -c "Alice Bob" -m ab1 | Create an account named ab1, with a comment of "Alice Bob" and create the new user’s home directory |
userdel ab1 | Delete the account named ab1 |
usermod -aG gp1 ab1 | Add the account ab1 to the group gp1 |
passwd user | Set or change a user’s password. |
passwd -l user | Lock a user account. |
passwd -u user | Unlock a user account. |
chage -l user | Display account password expiry info. |
chage -M 90 user | Set password to expire every 90 days. |
/etc/login.defs | File that sets user defaults (e.g., password aging). |
/etc/skel/ | Default files copied to new user’s home. |
/etc/passwd | Stores user account details. |
/etc/shadow | Stores password hashes and aging info. |
/etc/group | Stores group definitions. |
su - user | Switch to another user with their environment. |
sudo -i | Start a root login shell. |
groups user | Show groups the user belongs to. |
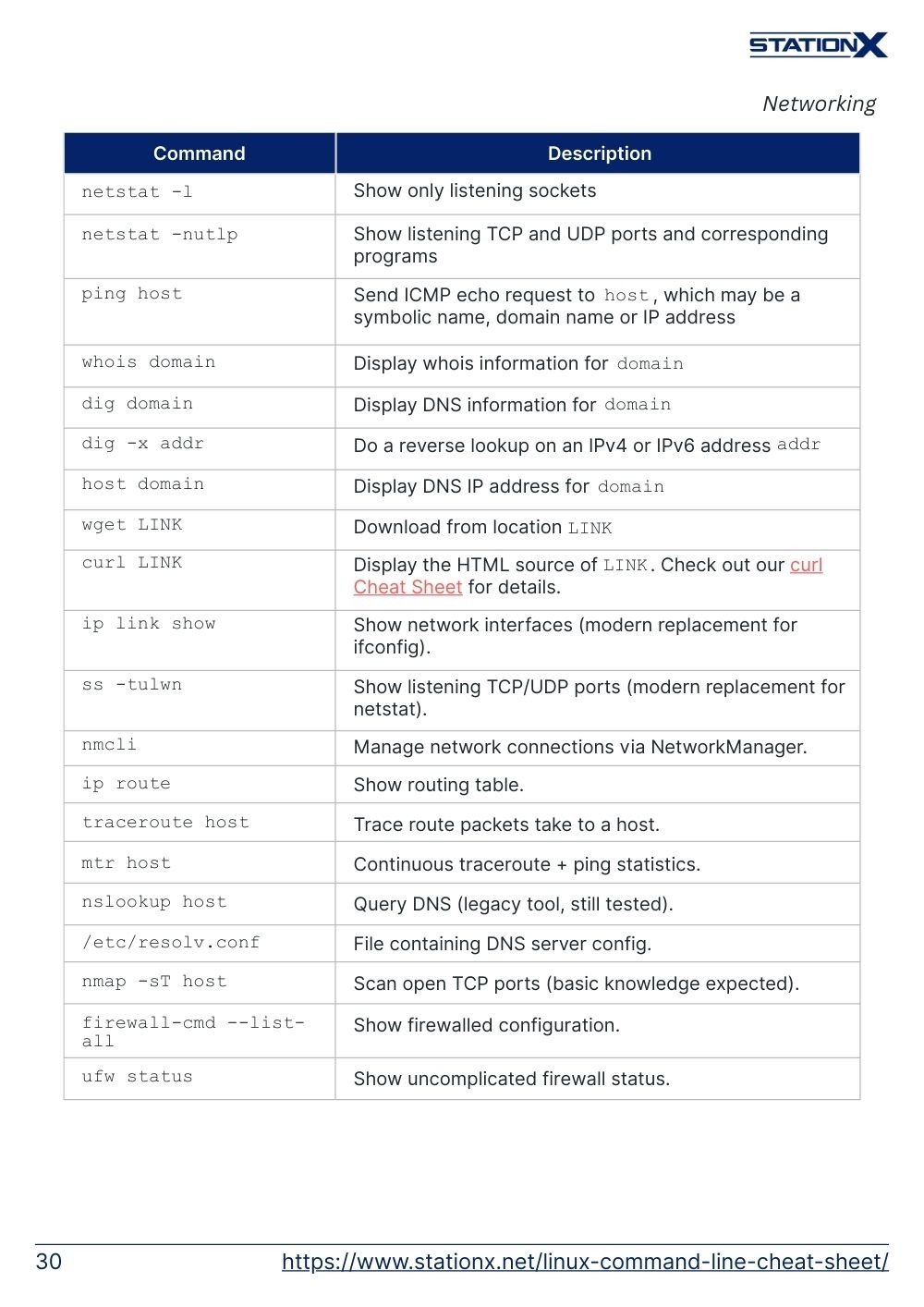
Networking
These commands regulate how your Linux machine communicates with other computers, such as the local area network (LAN) router or external websites.
| Command | Description |
|---|---|
ifconfig | Display all network interfaces with IP addresses |
ifconfig -a | Display all network interfaces, even if any of them is down, with IP addresses |
ifconfig eth0 | Display IP addresses and details of the eth0 interface |
ip a | Another way to display all network interfaces with IP addresses |
ethtool eth0 | Query or control network driver and hardware settings of the interface eth0 |
netstat | Print open sockets of network connections, routing tables, interface statistics, masquerade connections, and multicast memberships. Pipe with the less command: e.g., netstat -a | less |
netstat -a | Show both listening and non-listening sockets |
netstat -l | Show only listening sockets |
netstat -nutlp | Show listening TCP and UDP ports and corresponding programs |
ping host | Send ICMP echo request to host, which may be a symbolic name, domain name or IP address |
whois domain | Display whois information for domain |
dig domain | Display DNS information for domain |
dig -x addr | Do a reverse lookup on an IPv4 or IPv6 address addr |
host domain | Display DNS IP address for domain |
wget LINK | Download from location LINK |
curl LINK | Display the HTML source of LINK. Check out our curl Cheat Sheet for details. |
ip link show | Show network interfaces (modern replacement for ifconfig). |
ss -tulwn | Show listening TCP/UDP ports (modern replacement for netstat). |
nmcli | Manage network connections via NetworkManager. |
ip route | Show routing table. |
traceroute host | Trace route packets take to a host. |
mtr host | Continuous traceroute + ping statistics. |
nslookup host | Query DNS (legacy tool, still tested). |
/etc/resolv.conf | File containing DNS server config. |
nmap -sT host | Scan open TCP ports (basic knowledge expected). |
firewall-cmd --list-all | Show firewalld configuration. |
ufw status | Show uncomplicated firewall status. |
Installing New Programs
A package file is an archive containing compiled software and other resources it uses. The package file extension and the package installer (a utility for installing new programs) depend on the Linux distribution.
Know your system’s Linux distribution to understand the correct installation commands tailored to it. If the package comes with a README component, it should contain application-specific installation instructions such as extracting TAR files, ./setup.sh, and make install.
Package Management Overview
The following table is on package management in popular Linux distributions.
| Linux Distribution | Package File Extension | Package Installer(s) | Extra Information |
Debian/Ubuntu | .deb | apt, dpkg | Repo configs: /etc/apt/sources.list, /etc/apt/sources.list.d/ |
Rocky / Fedora / Red Hat Enterprise Linux | .rpm | yum, dnf | Repo configs: /etc/yum.repos.d/ |
Arch Linux / Manjaro / Garuda / Chakra | .pkg, .pacman, .pkg.tar(.xz/.zst/.gz) | pacman | Package databases are in /var/lib/pacman/ |
Universal | .snap, .flatpak, .AppImage | snap, flatpak, (run directly for AppImage) | Snap (snap), Flatpak (flatpak), AppImage (run directly). |
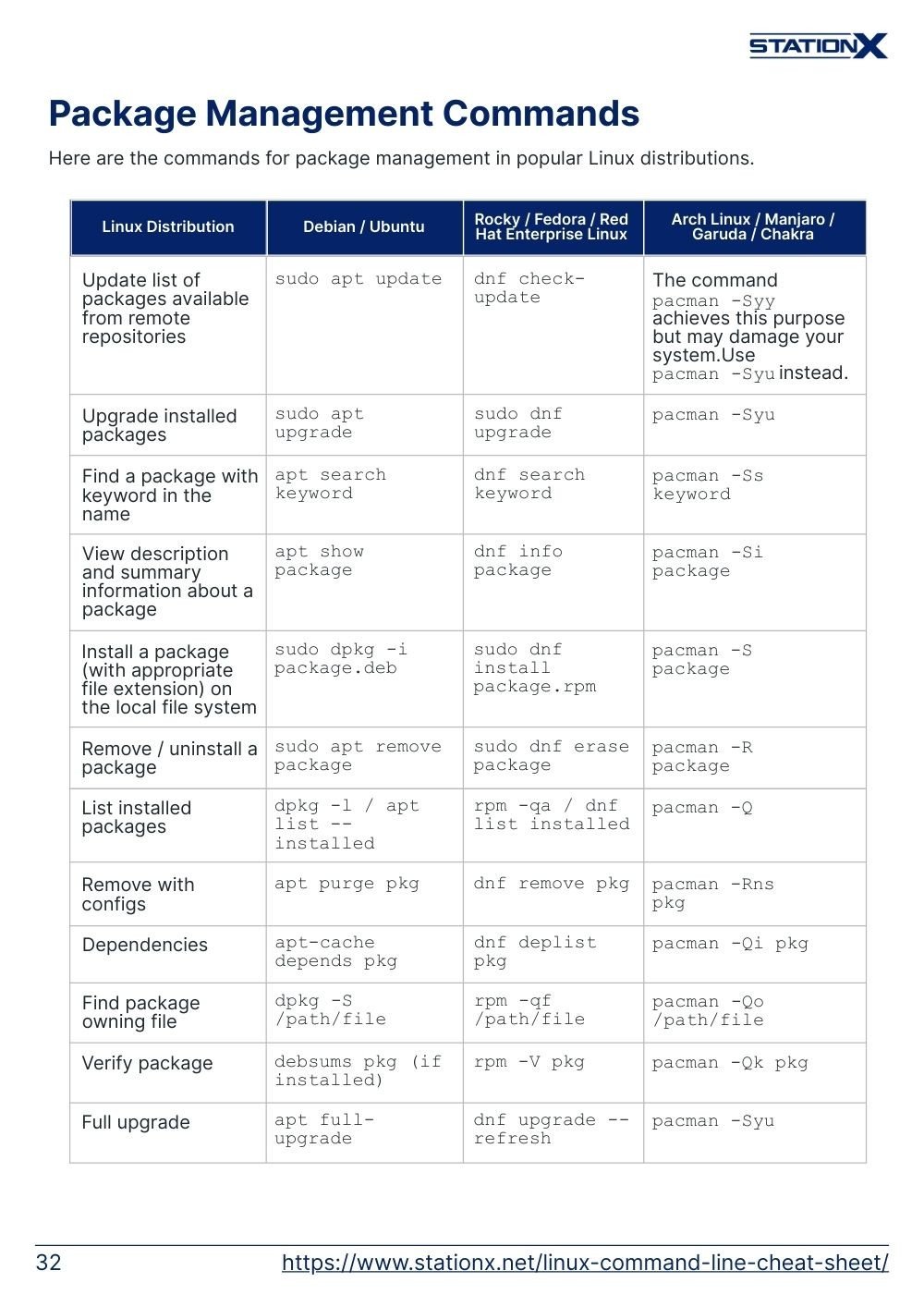
Package Management Commands
Here are the commands for package management in popular Linux distributions.
| Linux distribution | Debian / Ubuntu | Rocky / Fedora / Red Hat Enterprise Linux | Arch Linux / Manjaro / Garuda / Chakra |
|---|---|---|---|
| Update list of packages available from remote repositories | sudo apt update | dnf check-update | The command pacman -Syy achieves this purpose but may damage your system.Use pacman -Syu instead. |
| Upgrade installed packages | sudo apt upgrade | sudo dnf upgrade | pacman -Syu |
| Find a package with keyword in the name | apt search keyword | dnf search keyword | pacman -Ss keyword |
| View description and summary information about a package | apt show package | dnf info package | pacman -Si package |
| Install a package (with appropriate file extension) on the local file system | sudo dpkg -i package.deb | sudo dnf install package.rpm | pacman -S package |
| Remove / uninstall a package | sudo apt remove package | sudo dnf erase package | pacman -R package |
| List installed packages | dpkg -l / apt list --installed | rpm -qa / dnf list installed | pacman -Q |
| Remove with configs | apt purge pkg | dnf remove pkg | pacman -Rns pkg |
| Dependencies | apt-cache depends pkg | dnf deplist pkg | pacman -Qi pkg |
| Find package owning file | dpkg -S /path/file | rpm -qf /path/file | pacman -Qo /path/file |
| Verify package | debsums pkg (if installed) | rpm -V pkg | pacman -Qk pkg |
| Full upgrade | apt full-upgrade | dnf upgrade --refresh | pacman -Syu |
Security Tools
These commands are used to manage and configure Linux security frameworks like SELinux and AppArmor. They help enforce access controls, monitor security contexts, define policies, and switch between enforcement and permissive modes.
| Command | Description |
getenforce | Show current SELinux mode (enforcing, permissive, disabled). |
setenforce 0 1 | Set SELinux mode: 0 = permissive, 1 = enforcing. |
getsebool -a | List SELinux booleans and their states. |
setsebool -P var on off | Set SELinux boolean var on or off, persistent across reboots. |
chcon -t type file | Change SELinux security context of a file. |
restorecon -Rv path | Restore SELinux context defaults on a path. |
semanage fcontext -a -t type path | Define default SELinux context rules. |
audit2allow | Suggest SELinux policy changes from audit logs. |
aa-status | Show AppArmor profile status. |
aa-enforce profile | Put an AppArmor profile in enforce mode. |
aa-complain profile | Put an AppArmor profile in complain mode (log only). |
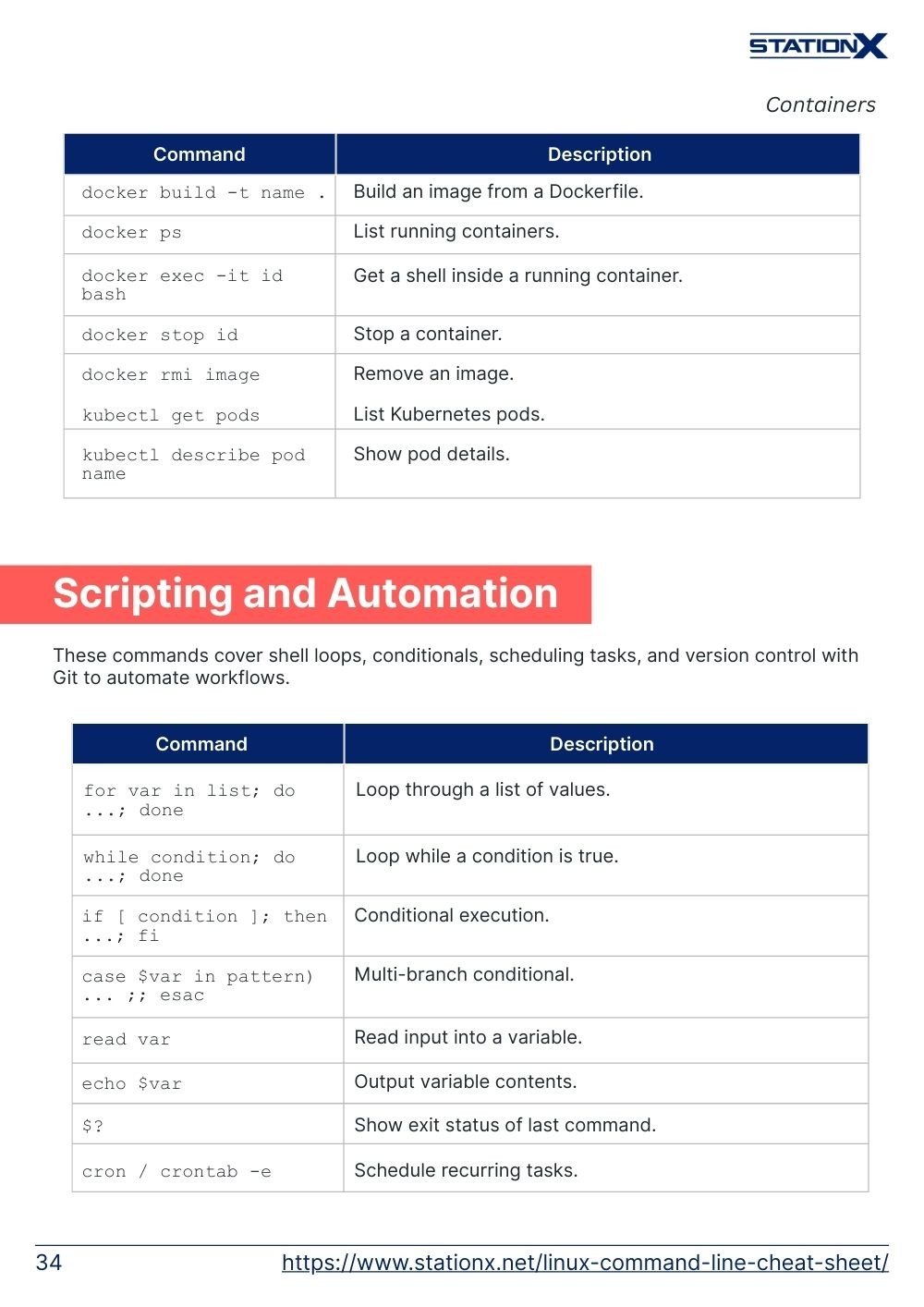
Containers
Working with containers is central to modern DevOps and cloud-native environments. These commands let you build and run Docker images, manage active containers, and interact with Kubernetes pods for orchestration.
| Command | Description |
docker run -it image | Run a container interactively. |
docker build -t name . | Build an image from a Dockerfile. |
docker ps | List running containers. |
docker exec -it id bash | Get a shell inside a running container. |
docker stop id | Stop a container. |
docker rmi image | Remove an image. |
kubectl get pods | List Kubernetes pods. |
kubectl describe pod name | Show pod details. |
Scripting and Automation
These commands cover shell loops, conditionals, scheduling tasks, and version control with Git to automate workflows.
| Command | Description |
for var in list; do ...; done | Loop through a list of values. |
while condition; do ...; done | Loop while a condition is true. |
if [ condition ]; then ...; fi | Conditional execution. |
case $var in pattern) ... ;; esac | Multi-branch conditional. |
read var | Read input into a variable. |
echo $var | Output variable contents. |
$? | Show exit status of last command. |
cron / crontab -e | Schedule recurring tasks. |
at time | Schedule a one-time task. |
git clone url | Clone a Git repo. |
git add file | Stage file changes. |
git commit -m "msg" | Commit changes. |
git push | Push commits to remote repo. |
git checkout branch | Switch to a branch. |
vi Editor Basics
The vi editor is a powerful text editor available on all Unix-like systems. These commands cover basic navigation, editing, and saving within vi.
| Command | Description |
vi file | Open file in vi editor. |
i | Switch to insert mode. |
Esc | Return to command mode. |
:w | Save changes. |
:q | Quit vi. |
:q! | Quit without saving. |
:wq | Save and quit. |
dd | Delete the current line. |
yy | Copy (yank) the current line. |
p | Paste copied or deleted text. |
/pattern | Search for pattern. |
n | Repeat last search. |
Linux Commands Cheat Sheet Conclusion
Learning basic Linux commands is a solid first step toward building a career in IT and cyber security. You’re now ready to practice these skills on any Linux distribution you prefer, whether that’s Ubuntu, Fedora, or security-focused systems like Kali Linux and Parrot OS. Don’t forget to grab our handy Unix Commands Cheat Sheet to keep your skills sharp.
To continue your journey, explore our Complete Linux Training Courses Bundle. This all-in-one bundle takes you far beyond the basics, covering Linux administration, shell scripting, system security, and much more, giving you a well-rounded foundation for both IT operations and cyber security.
And if you’re looking to expand even further, StationX also offers CompTIA Linux+ exam vouchers for those interested in certification, as well as our industry-leading Master’s Program, which provides 30,000+ cybersecurity courses & labs with guided learning, certifications, and full career support.
The Ultimate Linux Courses Mastery Bundle includes:
- Linux Course for Beginners
- Linux Online Training: Level Up in 5 Days
- Learn Linux Quickly: Command Line Essentials
- Linux Administrator Course
- Linux Administration Course: Beginner to Advanced
- Linux Security Training: Practical Security Guide
- Linux System Administration Training: LAMP Step-By-Step














Thank you sir
You are welcome.
Awesome thanks so much, cant wait to play around with these and learn so many new ones too :)
My pleasure.
Excellent, thanks for sharing, superb..
Thank you so much, awesome work!
Thank you for reading my work!
how we can download?
This website is a gem! A lot of info and you’ll learn every day something new!
Can I bypass bitlocker recovery via Linux?
so much information on this page ….loaded and very useful. Bless you all!